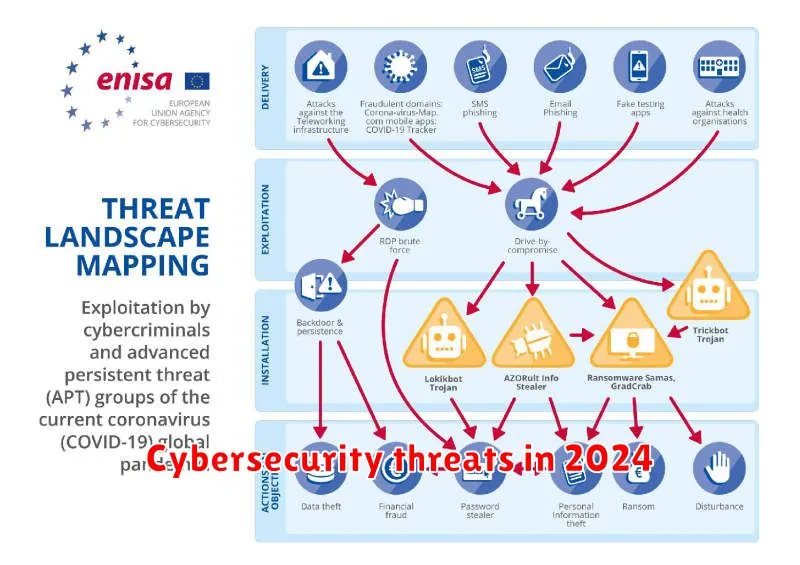
In the ever-evolving landscape of technology, cybersecurity has become a paramount concern for individuals, businesses, and governments alike. As we enter 2024, the threat landscape is becoming increasingly sophisticated, with attackers employing novel techniques to exploit vulnerabilities and compromise sensitive data. From ransomware attacks to data breaches, the potential consequences of cyberattacks are far-reaching, impacting everything from financial stability to national security.
This article delves into the top cybersecurity threats anticipated in 2024, providing insights into the tactics employed by adversaries and offering practical mitigation strategies to help individuals and organizations stay ahead of the curve. We will explore emerging threats such as artificial intelligence (AI)-powered attacks, the growing prevalence of social engineering, and the increasing sophistication of ransomware campaigns. By understanding the latest threats and implementing effective security measures, we can collectively strengthen our defenses and safeguard against the ever-present dangers of the digital realm.
The Evolving Threat Landscape: What to Expect in 2024

The cyber threat landscape is constantly evolving, with new threats emerging and existing ones becoming more sophisticated. To stay ahead of the curve and protect your organization, it is crucial to understand the latest trends and emerging threats. In this article, we will delve into the key predictions for the cyber threat landscape in 2024.
Rise of AI-Powered Attacks
Artificial intelligence (AI) is rapidly transforming various industries, and the cyber security world is no exception. In 2024, we can expect to see a significant increase in AI-powered attacks. These attacks will leverage AI to automate tasks like reconnaissance, phishing, and malware development, making them more efficient and difficult to detect. AI-powered malware will be able to adapt and evade traditional security solutions, posing a significant challenge to security teams.
Increased Targeting of Supply Chains
Supply chain attacks have become increasingly common in recent years, and this trend is likely to continue in 2024. Attackers will target vulnerabilities in the supply chains of organizations, aiming to gain access to sensitive data or disrupt operations. This could involve targeting software vendors, cloud providers, or other third-party services that organizations rely on. Supply chain security should be a top priority for businesses in the coming year.
The Rise of Ransomware 2.0
Ransomware attacks have evolved significantly in recent years, with attackers employing new tactics and demanding higher ransoms. In 2024, we can expect to see the rise of Ransomware 2.0, which will combine sophisticated techniques like AI, double extortion, and data exfiltration to maximize their impact. Attackers will not only encrypt data but also threaten to leak sensitive information if their demands are not met. This will put even greater pressure on organizations to pay ransoms, making ransomware a more significant threat than ever before.
The Growing Importance of Zero Trust Security
As the threat landscape becomes more complex, organizations need to adopt a more proactive security approach. Zero trust security is a framework that assumes no user or device can be trusted by default, requiring strict verification and authentication before granting access to resources. This approach will become increasingly important in 2024 as organizations look for ways to mitigate the risks posed by AI-powered attacks, supply chain vulnerabilities, and other emerging threats.
The Need for Proactive Security Measures
Staying ahead of the curve in cybersecurity requires a proactive approach. Organizations must invest in robust security solutions, train their employees on best practices, and stay up-to-date on the latest threats and vulnerabilities. Regular security assessments and penetration testing are crucial for identifying weaknesses that attackers could exploit. It is also essential to develop an incident response plan and practice it regularly to ensure that the organization is prepared to respond effectively to cyberattacks.
The cyber threat landscape is constantly changing, and staying ahead of the curve requires vigilance, adaptability, and a commitment to security. By understanding the key trends and predictions for 2024, organizations can take proactive steps to protect themselves from emerging threats and ensure the safety and security of their data and operations.
1. Rise of AI-Powered Cyberattacks

The landscape of cyberattacks is rapidly evolving, with artificial intelligence (AI) playing an increasingly prominent role. AI-powered tools are enabling attackers to automate and scale their operations, leading to more sophisticated and difficult-to-detect attacks. These tools can analyze vast amounts of data, identify vulnerabilities, and execute attacks with precision and speed that surpasses human capabilities.
AI is being used in a variety of ways to enhance cyberattacks, including:
- Automated phishing attacks: AI algorithms can analyze user data and social media posts to create highly personalized phishing emails that are more likely to be opened and clicked.
- Malware development and distribution: AI can be used to generate new and highly effective malware strains that are difficult to detect and analyze. It can also be used to automate the distribution of malware through various channels.
- Target identification and reconnaissance: AI can be used to scan networks and systems for vulnerabilities and identify potential targets. This information can be used to plan and execute highly targeted attacks.
- Social engineering attacks: AI-powered chatbots can be used to impersonate real people and manipulate victims into providing sensitive information or granting access to systems.
The use of AI in cyberattacks presents significant challenges for security professionals. Traditional security measures may not be effective against these new threats, and new approaches are needed to protect against AI-powered attacks.
2. The Growing Threat of Ransomware
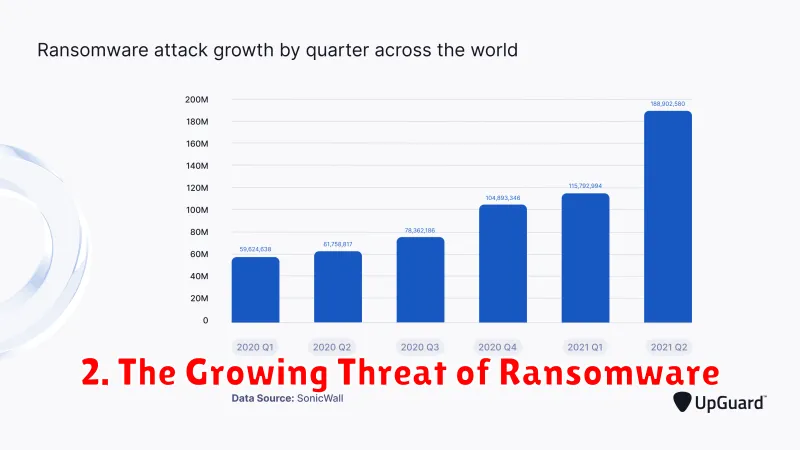
Ransomware has become a significant and ever-growing threat in the cyber world. It is a type of malware that encrypts a victim’s data, making it inaccessible without a decryption key. The attackers then demand payment, usually in cryptocurrency, to provide the key and restore the data.
The impact of ransomware can be devastating. Victims may suffer significant financial losses, business disruptions, and reputational damage. Criminals are continuously developing new and sophisticated ransomware strains, making them increasingly difficult to detect and prevent.
The Rise of Ransomware Attacks
Ransomware attacks have been on the rise in recent years, with both the frequency and severity of attacks increasing. According to a report by the Cybersecurity and Infrastructure Security Agency (CISA), ransomware attacks have become the most common cybercrime affecting U.S. businesses.
Several factors have contributed to the rise of ransomware, including the growing sophistication of cybercriminals, the increasing reliance on digital data, and the availability of ransomware-as-a-service (RaaS) platforms.
Protecting Yourself from Ransomware
While ransomware is a serious threat, there are steps individuals and organizations can take to protect themselves:
- Keep your software up to date: Patching vulnerabilities promptly helps prevent ransomware from exploiting weaknesses in your systems.
- Back up your data regularly: Having regular backups allows you to restore your data even if it’s encrypted by ransomware.
- Be cautious of suspicious emails and attachments: Avoid clicking on links or opening attachments from unknown senders.
- Use strong passwords: Choose unique and complex passwords for all your online accounts.
- Educate your employees: Train employees on best practices for recognizing and avoiding ransomware threats.
By taking these steps, individuals and organizations can significantly reduce their risk of falling victim to a ransomware attack.
3. Exploiting Cloud Vulnerabilities

Cloud computing offers various benefits, but it also introduces new security vulnerabilities. Attackers can exploit these vulnerabilities to gain unauthorized access to sensitive data and resources. Understanding these vulnerabilities is crucial for organizations to implement effective security measures.
Common Cloud Vulnerabilities:
-
Misconfigured Cloud Services: Improperly configured cloud services, such as storage buckets or databases, can expose sensitive data to unauthorized access.
-
Insecure APIs: Weak API authentication and authorization mechanisms can allow attackers to access or manipulate data through APIs.
-
Lack of Patching and Updates: Outdated cloud infrastructure and software can be vulnerable to known exploits and vulnerabilities.
-
Insufficient Data Encryption: Inadequate encryption of data at rest and in transit can expose sensitive information to attackers.
-
Lack of Identity and Access Management (IAM): Weak IAM controls can allow unauthorized users to access cloud resources.
-
Cloud-Specific Attacks: Attackers can exploit cloud-specific vulnerabilities, such as serverless computing or container security flaws.
Exploiting Cloud Vulnerabilities:
Attackers can exploit cloud vulnerabilities using various techniques, including:
-
Credential Stuffing: Attackers use stolen or leaked credentials to gain access to cloud accounts.
-
Brute Force Attacks: Attackers try to guess passwords or API keys through repeated attempts.
-
SQL Injection: Attackers inject malicious SQL code into cloud databases to gain unauthorized access or modify data.
-
Cross-Site Scripting (XSS): Attackers inject malicious JavaScript code into cloud applications to steal user credentials or manipulate data.
-
Denial-of-Service (DoS) Attacks: Attackers overwhelm cloud resources with traffic, making them unavailable to legitimate users.
Mitigating Cloud Vulnerabilities:
To mitigate cloud vulnerabilities, organizations should implement the following security best practices:
-
Implement Strong IAM Controls: Use multi-factor authentication (MFA), least privilege access, and role-based access control (RBAC) to limit access to cloud resources.
-
Secure Cloud Services: Properly configure cloud services, such as storage buckets, databases, and network firewalls, to prevent unauthorized access.
-
Regularly Patch and Update: Keep cloud infrastructure and software up to date with the latest security patches and updates.
-
Encrypt Data at Rest and in Transit: Encrypt data stored in cloud databases and applications, as well as data transmitted over the network.
-
Monitor Cloud Security: Regularly monitor cloud environments for suspicious activity and security breaches.
-
Implement Security Automation: Automate security tasks, such as patching and vulnerability scanning, to improve efficiency and effectiveness.
By adopting a proactive security approach and implementing robust security measures, organizations can mitigate cloud vulnerabilities and protect their data and resources from attacks.
4. Mobile Devices: A Prime Target

Mobile devices have become an indispensable part of our lives, and unfortunately, they’ve also become a prime target for cybercriminals. With the rise of mobile banking, online shopping, and social media access from our phones, our sensitive data is constantly at risk. Here are some reasons why mobile devices are so vulnerable:
- Lack of Security Awareness: Many users don’t prioritize mobile security as they do for their computers. They may be unaware of the risks involved or simply not take the necessary precautions.
- Open Wi-Fi Networks: Public Wi-Fi networks are notorious for their lack of security. Connecting to an unsecured network can expose your data to hackers.
- Malicious Apps: The Google Play Store and Apple App Store are not immune to malicious apps. Downloading an infected app can grant hackers access to your device and personal data.
- Phishing Scams: Mobile devices are susceptible to phishing attacks through text messages (SMS) and emails. These scams often lure users into clicking on malicious links that steal their login credentials or financial information.
To protect your mobile device, be sure to install a reputable antivirus app, enable strong passwords and two-factor authentication, and avoid connecting to public Wi-Fi networks whenever possible. Regularly update your operating system and apps to patch any security vulnerabilities. Lastly, be cautious of suspicious links and messages, and always verify the authenticity of any website or app before entering sensitive information.
5. The Internet of Things (IoT) and Associated Risks

The Internet of Things (IoT) is a network of physical devices, vehicles, home appliances, and other items embedded with electronics, software, sensors, actuators, and network connectivity that enables these objects to collect and exchange data. The IoT is rapidly expanding, with billions of devices already connected and projections of trillions more to come in the next few years. While the IoT offers numerous benefits, such as increased efficiency, automation, and convenience, it also poses significant security risks.
Security Risks Associated with IoT
IoT devices are often designed with limited security features, making them vulnerable to attack. Some of the key security risks associated with the IoT include:
- Data breaches: Sensitive data, such as personal information, financial data, and location data, can be stolen from IoT devices.
- Denial of service attacks: Attackers can overload IoT devices, making them unavailable to legitimate users.
- Malware infections: IoT devices can be infected with malware, which can be used to steal data, launch attacks on other systems, or control the device itself.
- Man-in-the-middle attacks: Attackers can intercept communications between IoT devices and other systems, allowing them to steal data or inject malicious code.
- Physical security risks: IoT devices can be physically accessed, allowing attackers to tamper with them or gain unauthorized access to data.
Mitigating IoT Security Risks
There are a number of steps that can be taken to mitigate the security risks associated with the IoT:
- Use strong passwords and authentication: Ensure that all IoT devices are protected with strong passwords and multi-factor authentication.
- Keep software up to date: Regularly update IoT device firmware and software to patch security vulnerabilities.
- Use a secure network: Connect IoT devices to a secure network, such as a virtual private network (VPN), to protect data from eavesdropping.
- Implement security policies: Establish clear security policies for the use of IoT devices within an organization.
- Use security solutions: Employ security solutions specifically designed for IoT devices, such as intrusion detection systems and firewalls.
As the IoT continues to grow, it is essential to address the security risks associated with this technology. By taking proactive steps to mitigate these risks, organizations and individuals can ensure that the IoT remains a safe and beneficial technology.
6. Insider Threats: A Persistent Danger
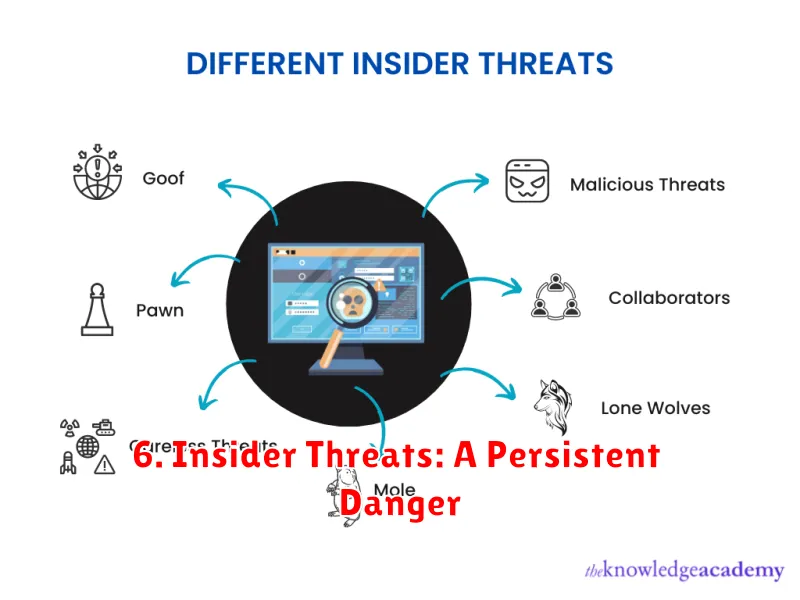
Insider threats are a significant concern for organizations of all sizes. These threats come from individuals who have legitimate access to sensitive information, systems, and networks. They can be employees, contractors, former employees, or even business partners. Unlike external threats that come from outside the organization, insider threats can have a more profound impact as they are often more knowledgeable about the organization’s systems and security measures.
Insider threats can be intentional or unintentional. Intentional threats are often driven by malicious intent, such as financial gain, revenge, or espionage. Unintentional threats can occur due to negligence, lack of awareness, or simply human error. Regardless of the intent, insider threats can cause substantial damage to an organization, leading to data breaches, system downtime, reputational harm, and financial losses.
Here are some examples of insider threats:
- Data theft: An employee stealing confidential data for personal gain or to sell to competitors.
- System sabotage: A disgruntled employee deliberately disrupting or damaging critical systems.
- Data leakage: An employee accidentally sharing sensitive information with unauthorized individuals.
- Malware infection: An employee unknowingly clicking on a malicious link or downloading a compromised file, introducing malware into the organization’s network.
- Social engineering: An employee being tricked into revealing sensitive information or granting access to unauthorized individuals.
To mitigate insider threats, organizations need to implement a comprehensive security strategy that includes:
- Strong access controls: Limiting access to sensitive information and systems based on the principle of least privilege.
- Employee training and awareness programs: Educating employees on security risks, best practices, and reporting procedures.
- Data loss prevention (DLP): Implementing measures to prevent sensitive data from leaving the organization’s network.
- Regular security audits and assessments: Identifying vulnerabilities and weaknesses in security systems.
- Incident response plan: Establishing procedures for detecting, containing, and responding to insider threat incidents.
By taking proactive steps to manage insider threats, organizations can significantly reduce their risk of experiencing a security breach or data loss. It’s crucial to remember that insider threats are not always easy to identify or prevent, but with the right strategies and measures, organizations can minimize their exposure to these persistent dangers.
7. Social Engineering: Deception at its Finest

Social engineering is a type of attack that relies on human interaction and psychological manipulation to gain access to sensitive information or systems. Attackers often use deception, impersonation, or other tactics to trick victims into revealing confidential data, granting access to restricted areas, or performing actions that compromise security.
Social engineering attacks can take many forms, including:
- Phishing: Sending emails or messages that appear to be from legitimate sources, such as banks or government agencies, in order to trick victims into clicking on malicious links or providing sensitive information.
- Baiting: Offering victims something tempting, such as a free gift or a discount, in order to lure them into clicking on a malicious link or downloading a malicious file.
- Pretexting: Creating a false scenario or story to gain access to information or systems.
- Quid pro quo: Offering something of value in exchange for something else, such as a bribe or a favor.
- Scareware: Using fear or intimidation to trick victims into taking actions that compromise their security.
Social engineering attacks are particularly effective because they exploit human trust and vulnerability. Attackers often target victims who are not tech-savvy, who are under time pressure, or who are simply unaware of the risks.
To protect yourself from social engineering attacks, it’s important to be aware of the tactics that attackers use and to practice good security habits, such as:
- Be wary of unsolicited emails and messages, especially those that ask for personal information or that contain suspicious links.
- Verify the authenticity of requests for information or access to systems before taking any action.
- Be cautious about what you share online, and be aware that your social media posts can be used by attackers to gather information about you.
- Keep your software up to date, as this will help to protect you from known vulnerabilities.
- Use strong passwords and don’t reuse the same password for multiple accounts.
By being aware of the risks and taking precautions, you can help to protect yourself from social engineering attacks.
8. Data Breaches and Privacy Concerns
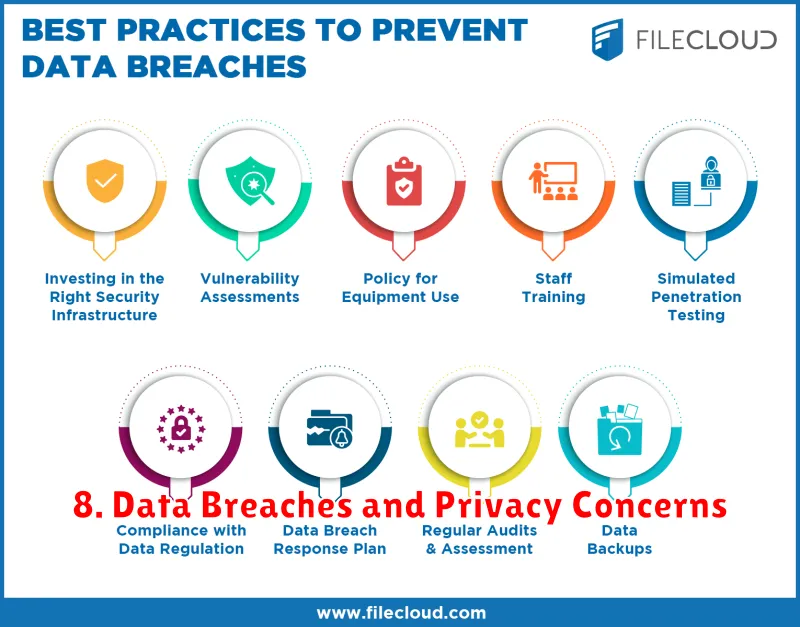
As the world becomes increasingly reliant on technology, the potential for data breaches and privacy concerns has become a significant issue. Data breaches occur when sensitive information, such as personal data, financial information, or intellectual property, is accessed or stolen by unauthorized individuals. These breaches can have devastating consequences for individuals, organizations, and even entire nations.
One of the primary concerns surrounding data breaches is the potential for identity theft. When personal data is compromised, it can be used by criminals to impersonate individuals and gain access to their bank accounts, credit cards, or other sensitive financial information. This can lead to financial losses, damage to credit scores, and significant stress for victims.
Another concern is the potential for privacy violations. Data breaches can expose personal information, such as medical records, social media activity, or browsing history, to unauthorized individuals. This can violate individuals’ privacy and leave them vulnerable to harassment, discrimination, or even physical harm.
Data breaches can also have significant impacts on organizations. They can lead to financial losses, damage to reputation, and even legal action. Businesses may be forced to pay hefty fines, settle lawsuits, and provide credit monitoring services to affected customers. In some cases, data breaches can even lead to the closure of businesses.
The rise of cybercrime has further exacerbated the problem of data breaches and privacy concerns. Cybercriminals are increasingly sophisticated and use advanced techniques to target organizations and individuals. They may use malware, phishing scams, or social engineering tactics to gain access to sensitive information. The rapid evolution of cybercrime makes it difficult for organizations and individuals to stay ahead of the curve and protect themselves.
To address these challenges, individuals and organizations need to take steps to protect their data and privacy. This includes using strong passwords, enabling multi-factor authentication, being cautious about phishing scams, and keeping software updated. Organizations also need to invest in robust cybersecurity measures, implement data breach response plans, and provide training to employees on cybersecurity best practices.
9. The Importance of Cybersecurity Awareness Training

In today’s digital age, cybersecurity is more crucial than ever. With the ever-increasing number of cyberattacks, it’s essential for organizations to prioritize the security of their data and systems. One of the most effective ways to achieve this is through cybersecurity awareness training. This training equips employees with the knowledge and skills necessary to identify and mitigate potential threats, ultimately reducing the risk of cyberattacks.
Cybersecurity awareness training helps employees understand the importance of security and how their actions can impact the organization. It covers topics such as:
- Phishing scams: Employees learn how to identify and avoid suspicious emails, websites, and phone calls that aim to steal sensitive information.
- Malware: Training covers different types of malware, how it spreads, and how to protect against it. Employees learn to recognize signs of malware infection and report it promptly.
- Social engineering: This type of attack manipulates people into revealing sensitive information. Training helps employees understand social engineering tactics and how to resist them.
- Strong passwords: Employees learn the importance of creating strong passwords and the risks associated with using weak passwords.
- Data privacy: Training covers data privacy regulations and best practices for handling sensitive information.
Apart from enhancing security awareness, cybersecurity training also fosters a culture of security within the organization. Employees become more proactive in identifying and reporting security threats, contributing to a stronger security posture. This collaborative approach strengthens the overall cybersecurity ecosystem of the organization.
By investing in cybersecurity awareness training, organizations can significantly reduce their risk of cyberattacks. This training empowers employees to become active participants in protecting the organization’s data and systems, creating a safer and more secure digital environment.
10. Proactive Measures: Building a Robust Cybersecurity Posture

In today’s digital landscape, cybersecurity is no longer a mere afterthought but a paramount concern for individuals and organizations alike. The ever-evolving nature of cyber threats necessitates a proactive approach to safeguarding sensitive data and systems. Building a robust cybersecurity posture involves implementing a comprehensive strategy that encompasses multiple layers of defense, from technological solutions to user education and awareness.
One crucial aspect is regular security assessments. These assessments identify vulnerabilities and weaknesses in your systems, allowing you to address them before they are exploited by malicious actors. It is also vital to maintain up-to-date software and patches. Software updates often include security fixes that patch known vulnerabilities, making it significantly harder for attackers to gain access. Regular software updates are essential for maintaining a secure digital environment.
Furthermore, strong passwords are a fundamental pillar of cybersecurity. Using complex combinations of uppercase and lowercase letters, numbers, and symbols significantly enhances password strength, making it much harder for attackers to guess or crack them. It’s also a good idea to use a password manager to store and manage your passwords securely, eliminating the need to remember multiple complex passwords.
User education and awareness play a pivotal role in bolstering cybersecurity. Employees must be trained to recognize and avoid common phishing scams, malware infections, and other online threats. Implementing multi-factor authentication (MFA) adds an extra layer of security to your accounts by requiring multiple forms of authentication, such as a password and a code sent to your phone. This significantly reduces the risk of unauthorized access, even if an attacker manages to obtain your password.
Beyond these measures, it is crucial to establish a culture of security within your organization. This involves fostering a shared responsibility for cybersecurity, encouraging employees to report any suspicious activities, and prioritizing the adoption of security best practices. Regularly backing up your data is an essential precaution. In the event of a cyberattack or data loss, having backups allows you to restore your data and minimize disruption to your operations.
In conclusion, building a robust cybersecurity posture is an ongoing process that requires continuous vigilance and adaptation. By implementing these proactive measures, organizations and individuals can significantly enhance their security, mitigating the risks posed by ever-evolving cyber threats. Remember, a proactive approach to cybersecurity is the most effective way to protect your valuable data and systems from harm.