In the ever-evolving landscape of the digital world, where information flows freely and seamlessly, the importance of data encryption cannot be overstated. From personal financial details to confidential business records, our sensitive data is constantly at risk of falling into the wrong hands. As cyber threats become increasingly sophisticated, safeguarding our digital assets has become paramount. Data encryption acts as a robust shield, transforming our valuable information into an unreadable code, preventing unauthorized access and ensuring the integrity of our data.
The need for data encryption extends far beyond individual concerns, impacting businesses, governments, and individuals alike. As we increasingly rely on online platforms for communication, transactions, and data storage, data encryption plays a critical role in protecting our privacy and security. This article delves into the crucial role of data encryption in today’s digital world, exploring its benefits, various methods, and its impact on our everyday lives. Join us as we uncover the significance of data encryption and understand why it is essential for safeguarding our digital future.
Understanding Data Encryption
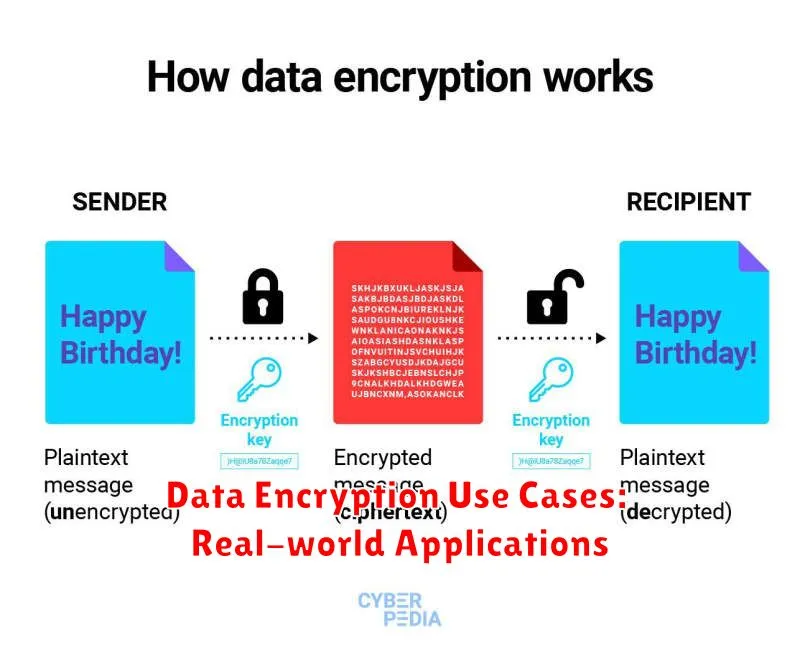
In today’s digital world, data security is paramount. Data breaches and cyberattacks are becoming increasingly common, putting sensitive information at risk. This is where data encryption comes in. Data encryption is a process of converting data into an unreadable format, known as ciphertext, using an encryption algorithm and a key. Only authorized individuals with the correct decryption key can access the original data.
Why is Data Encryption Important?
Data encryption is crucial for several reasons:
- Confidentiality: Encryption ensures that only authorized individuals can access sensitive information, protecting it from unauthorized access.
- Integrity: Encryption helps maintain the integrity of data by detecting any unauthorized modifications or alterations.
- Compliance: Many industries have regulations that mandate data encryption to protect sensitive information, such as healthcare, finance, and government.
Types of Data Encryption
There are various types of data encryption methods, each with its own strengths and weaknesses:
- Symmetric-key encryption: Uses the same key for both encryption and decryption. This method is fast and efficient but requires secure key distribution.
- Asymmetric-key encryption: Uses separate keys for encryption and decryption. One key is public and can be shared freely, while the other is private and kept secret. This method is more secure than symmetric-key encryption but slower.
- Hashing: A one-way function that converts data into a fixed-length string. Hashing is used for data integrity verification and password storage.
How Data Encryption Works
The basic principles of data encryption involve:
- Encryption: The process of converting plaintext into ciphertext using an encryption algorithm and a key.
- Decryption: The process of converting ciphertext back into plaintext using the same algorithm and the corresponding decryption key.
The encryption algorithm determines the mathematical operations used to transform the data, while the key provides the specific parameters for these operations. The strength of encryption depends on the complexity of the algorithm and the length and randomness of the key.
Examples of Data Encryption
Data encryption is widely used in various applications, including:
- Secure websites (HTTPS): Uses encryption to protect communication between a website and a user’s browser.
- Email encryption: Protects email content from unauthorized access during transmission.
- File encryption: Encrypts files stored on a computer or cloud storage, making them inaccessible to unauthorized users.
- Database encryption: Protects sensitive data stored in databases.
Conclusion
Data encryption is an essential security measure for protecting sensitive information in today’s digital landscape. By understanding the principles and types of encryption, individuals and organizations can make informed decisions about protecting their data and minimizing the risk of data breaches and cyberattacks.
Common Data Encryption Methods
Data encryption is the process of converting data into an unreadable format, making it inaccessible to unauthorized individuals. It’s an essential security measure to protect sensitive information from unauthorized access, disclosure, alteration, or destruction. There are several common data encryption methods used today, each with its strengths and weaknesses. Here’s a breakdown of some of the most popular:
Symmetric Encryption
Symmetric encryption uses a single key for both encrypting and decrypting data. This key must be kept secret and shared securely with authorized individuals.
- Advantages: Fast and efficient for large amounts of data.
- Disadvantages: Key management is a challenge, as the same key is used for both encryption and decryption.
Popular symmetric encryption algorithms include:
- AES (Advanced Encryption Standard): A widely used and robust algorithm.
- DES (Data Encryption Standard): An older algorithm considered less secure for modern applications.
- 3DES (Triple DES): An enhancement of DES, offering stronger security.
Asymmetric Encryption
Asymmetric encryption, also known as public-key cryptography, uses two separate keys: a public key and a private key. The public key can be shared freely, while the private key must be kept secret.
- Advantages: Secure key management, as only the private key can decrypt data encrypted with the corresponding public key.
- Disadvantages: Slower than symmetric encryption.
Common asymmetric encryption algorithms include:
- RSA (Rivest–Shamir–Adleman): A widely used algorithm for digital signatures and encryption.
- ECC (Elliptic Curve Cryptography): A more efficient alternative to RSA for certain applications.
Hashing
Hashing converts data into a fixed-length string of characters called a hash. It is a one-way function, meaning the original data cannot be retrieved from the hash.
- Advantages: Ensures data integrity, as any modification to the data will result in a different hash.
- Disadvantages: Not a true encryption method as it doesn’t provide confidentiality.
Popular hashing algorithms include:
- SHA-256 (Secure Hash Algorithm 256): A widely used algorithm for hashing passwords and other data.
- MD5 (Message Digest 5): An older algorithm considered less secure for modern applications.
Choosing the Right Encryption Method
The best encryption method for a particular application depends on various factors, including:
- Sensitivity of the data: More sensitive data requires stronger encryption.
- Performance requirements: Symmetric encryption is generally faster for large amounts of data.
- Key management complexity: Asymmetric encryption offers better key management but can be more complex to implement.
It’s important to choose an encryption method that aligns with the security needs and technical capabilities of your organization.
Symmetric vs. Asymmetric Encryption: Choosing the Right Approach
In the realm of cybersecurity, encryption plays a pivotal role in safeguarding sensitive information. Two primary encryption methods, symmetric and asymmetric encryption, offer distinct advantages and disadvantages, making the choice between them crucial for ensuring data security. Understanding the nuances of each approach is essential for selecting the most appropriate solution for specific scenarios.
Symmetric Encryption
Symmetric encryption, also known as secret-key encryption, employs a single key to both encrypt and decrypt data. This key must be shared between the sender and receiver, making secure key distribution a critical concern.
Advantages of Symmetric Encryption:
- Speed: Symmetric encryption algorithms are generally faster than asymmetric algorithms, making them ideal for encrypting large volumes of data.
- Efficiency: Symmetric encryption requires less computational power, leading to improved performance.
Disadvantages of Symmetric Encryption:
- Key Management: Securely distributing and managing the shared key can be challenging, especially in environments with multiple users or geographically dispersed parties.
- Scalability: Key management becomes more complex as the number of users increases, making it less suitable for large-scale applications.
Asymmetric Encryption
Asymmetric encryption, also known as public-key encryption, utilizes two distinct keys: a public key and a private key. The public key can be shared freely, while the private key must be kept secret. Encryption is performed using the public key, while decryption requires the corresponding private key.
Advantages of Asymmetric Encryption:
- Key Management: Key distribution is simplified as only the public key needs to be shared, eliminating the need for secure key exchange.
- Digital Signatures: Asymmetric encryption enables the creation of digital signatures, providing authenticity and non-repudiation.
- Scalability: Asymmetric encryption is well-suited for large-scale applications with multiple users, as key management is less complex.
Disadvantages of Asymmetric Encryption:
- Speed: Asymmetric encryption algorithms are generally slower than symmetric algorithms, making them less efficient for encrypting large amounts of data.
- Complexity: Implementing asymmetric encryption can be more complex than symmetric encryption due to the use of two keys.
Choosing the Right Approach
The choice between symmetric and asymmetric encryption depends on specific requirements and constraints:
- For high-performance data encryption: Symmetric encryption is the preferred choice due to its speed and efficiency.
- For secure communication with multiple parties: Asymmetric encryption provides a more robust solution for key management and digital signatures.
- For sensitive applications requiring strong authentication: Asymmetric encryption with digital signatures is essential to ensure authenticity and non-repudiation.
In many cases, a hybrid approach combining both symmetric and asymmetric encryption is employed to leverage the strengths of each method. For example, asymmetric encryption can be used to securely exchange a symmetric key, which can then be used to encrypt large volumes of data efficiently.
Ultimately, selecting the appropriate encryption method is crucial for ensuring the confidentiality, integrity, and authenticity of sensitive information. By carefully considering the advantages and disadvantages of both symmetric and asymmetric encryption, organizations can make informed decisions that effectively safeguard their valuable assets.
Benefits of Data Encryption for Businesses
In today’s digital world, data is everything. Businesses rely on data to operate, make decisions, and stay ahead of the competition. But data is also vulnerable to attack. Hackers are constantly looking for ways to steal sensitive information, and they are becoming increasingly sophisticated in their methods. That’s why data encryption is essential for any business that wants to protect its data and its reputation.
Data encryption is the process of converting data into an unreadable format, making it incomprehensible to anyone who doesn’t have the decryption key. This helps to protect data from unauthorized access, use, disclosure, disruption, modification, or destruction.
Benefits of Data Encryption:
- Protection Against Data Breaches: Data encryption is the most effective way to protect your data from hackers. Even if hackers gain access to your systems, they won’t be able to read your data if it’s encrypted.
- Compliance with Regulations: Many industries have regulations that require businesses to encrypt sensitive data. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires businesses that process credit card payments to encrypt cardholder data.
- Improved Data Security: Data encryption helps to ensure that only authorized users can access your data. This can help to prevent data leaks, misuse, and fraud.
- Enhanced Data Integrity: Encryption can help to protect the integrity of your data. If data is encrypted, it’s much harder for hackers to modify it without being detected.
- Increased Customer Trust: Customers are more likely to trust businesses that take steps to protect their data. By encrypting your data, you can show your customers that you are committed to their privacy and security.
Types of Data Encryption:
There are several different types of data encryption, each with its own strengths and weaknesses. Some of the most common types of encryption include:
- Symmetric Encryption: This type of encryption uses the same key to encrypt and decrypt data. It is fast and efficient, but it can be vulnerable if the key is compromised.
- Asymmetric Encryption: This type of encryption uses two keys: a public key and a private key. The public key can be used to encrypt data, but only the private key can decrypt it. This is a more secure type of encryption, but it can be slower than symmetric encryption.
Conclusion:
Data encryption is an essential security measure for any business. It can help to protect your data from unauthorized access, use, disclosure, disruption, modification, or destruction. By implementing data encryption, businesses can protect their data, comply with regulations, improve data security, enhance data integrity, and increase customer trust. If you haven’t already, consider implementing data encryption in your business today.
Data Encryption Best Practices
Data encryption is a crucial aspect of cybersecurity, protecting sensitive information from unauthorized access. Implementing robust encryption practices is essential for businesses and individuals alike. This article will explore essential data encryption best practices to safeguard your valuable data.
Choose Strong Encryption Algorithms
Selecting a strong encryption algorithm is fundamental. AES (Advanced Encryption Standard) is widely considered a secure and robust algorithm, frequently used for data encryption. Other reputable options include Twofish and Blowfish.
Implement Strong Passwords and Keys
The security of your encryption hinges on the strength of your passwords and keys. Avoid simple passwords and utilize complex combinations of upper and lowercase letters, numbers, and symbols. Consider using a password manager to generate and store strong credentials securely.
Encrypt Data at Rest and in Transit
Encryption should be applied to data both when it’s stored (at rest) and when it’s being transmitted (in transit). For data at rest, use encryption tools like BitLocker or FileVault. For data in transit, utilize secure protocols like HTTPS and TLS/SSL.
Regularly Update Encryption Keys
Periodically rotate your encryption keys to enhance security. This reduces the risk of compromise if a key is exposed. Establish a regular schedule for key rotation and ensure all systems are updated accordingly.
Use Data Loss Prevention (DLP) Solutions
Data Loss Prevention (DLP) solutions play a crucial role in preventing unauthorized data transfer. These tools can detect and block sensitive information from being shared outside of authorized channels. Consider implementing DLP solutions to bolster your data security strategy.
Implement Access Control Mechanisms
Restrict access to encrypted data to authorized personnel. Utilize role-based access control (RBAC) to grant different levels of access depending on user roles and responsibilities.
Educate Users on Encryption Best Practices
A well-informed workforce is a key defense against data breaches. Train users on the importance of data encryption and best practices for handling sensitive information. Encourage them to report suspicious activities and utilize strong passwords.
Regularly Review and Evaluate Security
Data security is an ongoing process. Conduct regular reviews of your encryption practices and security protocols. Stay updated on industry best practices, emerging threats, and vulnerabilities. Consider engaging security experts for vulnerability assessments and penetration testing to identify and address any weaknesses.
Conclusion
Implementing strong data encryption practices is paramount for protecting sensitive information from unauthorized access and breaches. By adhering to these best practices, businesses and individuals can significantly reduce the risk of data compromise and maintain the integrity of their valuable assets.
The Future of Data Encryption
In an increasingly digital world, data security has become paramount. As cyber threats evolve and become more sophisticated, the need for robust data encryption solutions is more critical than ever. Data encryption plays a vital role in safeguarding sensitive information from unauthorized access, ensuring data privacy and integrity.
The future of data encryption is a fascinating landscape, shaped by advancements in technology and evolving security challenges. Here are some key trends shaping the future of data encryption:
Homomorphic Encryption
Homomorphic encryption is a revolutionary technology that allows computations to be performed on encrypted data without decrypting it. This means that data can be processed and analyzed while remaining protected, offering significant advantages for privacy-preserving data analytics and cloud computing.
Quantum-Resistant Encryption
As quantum computing technology advances, existing encryption methods based on traditional algorithms could become vulnerable. Quantum-resistant encryption algorithms are being developed to withstand the power of quantum computers, ensuring the long-term security of sensitive data.
AI-Powered Encryption
Artificial intelligence (AI) is transforming the cybersecurity landscape, and data encryption is no exception. AI algorithms can be used to detect and respond to threats, enhance encryption key management, and automate data protection tasks.
Edge Encryption
With the rise of the Internet of Things (IoT) and edge computing, data is increasingly generated and processed at the edge of the network. Edge encryption involves encrypting data at the source, minimizing the risk of data breaches during transmission and processing.
Zero-Trust Security
Zero-trust security principles are gaining traction, emphasizing the need to verify and authenticate all users and devices before granting access to data. This approach will likely drive the adoption of more sophisticated encryption techniques, including multi-factor authentication and granular access control.
The future of data encryption is characterized by continuous innovation and adaptation. As technology evolves and cyber threats become more advanced, data encryption will remain a cornerstone of cybersecurity, safeguarding sensitive information and ensuring the privacy and integrity of data in the digital age.
Data Encryption Algorithms: From DES to AES and Beyond
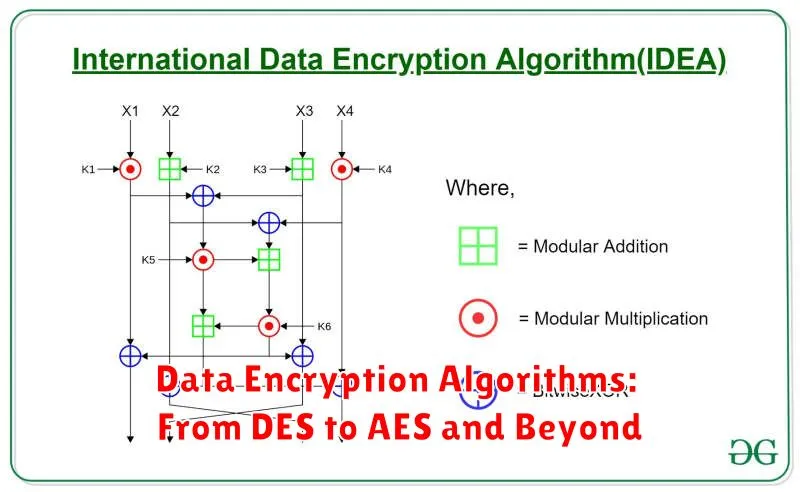
In the digital age, where data is constantly being transmitted and stored online, data encryption has become crucial for protecting sensitive information. Encryption algorithms are mathematical functions that transform plaintext into unreadable ciphertext, making it impossible for unauthorized individuals to access the data. Over the years, numerous encryption algorithms have been developed, each with its own strengths and weaknesses. This article explores the evolution of data encryption algorithms, from the early days of DES to the modern era of AES and beyond.
The Rise of DES
The Data Encryption Standard (DES), developed in the 1970s, was the first widely adopted encryption algorithm. It used a 56-bit key to encrypt data, providing a reasonable level of security at the time. However, as computing power increased, DES became vulnerable to brute-force attacks, where attackers systematically try all possible keys until they find the right one.
The Evolution to 3DES and AES
To address the vulnerabilities of DES, a more robust algorithm, known as Triple DES (3DES), was developed. 3DES essentially applied DES three times, effectively increasing the key length and strengthening the encryption. However, 3DES was relatively slow and computationally intensive.
In the early 2000s, the Advanced Encryption Standard (AES) emerged as the successor to DES. AES utilizes a 128-bit key, making it significantly more secure than its predecessors. Its speed and efficiency have made it the de facto standard for encryption today, widely used in applications ranging from secure websites to data storage devices.
Beyond AES: The Future of Encryption
As technology continues to advance, the threat of sophisticated cyberattacks is ever-present. While AES remains a highly secure algorithm, researchers are constantly working on developing even more robust encryption methods. Some promising areas of research include:
- Post-quantum cryptography: Algorithms designed to withstand attacks from quantum computers, which have the potential to break current encryption methods.
- Homomorphic encryption: Enables computations on encrypted data without decrypting it, preserving data privacy while enabling data analysis.
- Lattice-based cryptography: A promising new approach that leverages mathematical structures known as lattices to create robust encryption algorithms.
Conclusion
Data encryption algorithms have played a crucial role in protecting sensitive information in the digital age. From the early days of DES to the widespread adoption of AES, encryption has evolved significantly to meet the ever-increasing threats. As technology continues to advance, research into new and improved encryption methods will remain essential to safeguard our data in the future.
Exploring Encryption Key Management Solutions

In the realm of cybersecurity, protecting sensitive data is paramount. Encryption plays a vital role in safeguarding information from unauthorized access. However, the management of encryption keys, which are essential for unlocking encrypted data, presents a significant challenge.
Effective encryption key management is crucial for maintaining the integrity and confidentiality of encrypted data. This involves the secure generation, storage, distribution, and revocation of encryption keys. Failing to implement robust key management practices can leave organizations vulnerable to data breaches and security risks.
Key Management Solutions
Fortunately, numerous key management solutions are available to address the complexities of managing encryption keys. These solutions can be broadly categorized into hardware security modules (HSMs), software key management systems (SKMS), and cloud-based key management services.
Hardware Security Modules (HSMs)
HSMs are specialized hardware devices designed to protect sensitive cryptographic keys and operations. They provide a high level of security by physically isolating keys from the main system and offering tamper-proof environments. HSMs are typically used in scenarios requiring the highest level of security, such as financial institutions and government agencies.
Software Key Management Systems (SKMS)
SKMS are software applications that manage encryption keys within a software environment. They offer flexibility and scalability but may require additional security measures to mitigate potential vulnerabilities. SKMS are suitable for organizations that require a less expensive and more flexible solution compared to HSMs.
Cloud-Based Key Management Services
Cloud-based key management services provide a managed solution for encryption key management. They handle key generation, storage, and distribution in the cloud, offering scalability and ease of use. These services are particularly beneficial for organizations adopting cloud-based infrastructure or migrating sensitive data to the cloud.
Choosing the Right Solution
The choice of an encryption key management solution depends on several factors, including the sensitivity of the data, the organization’s security requirements, budget constraints, and technical expertise.
It’s essential to carefully evaluate the features and capabilities of different solutions before making a decision. Consider factors such as:
- Key generation and distribution methods
- Key storage and access controls
- Key rotation and revocation procedures
- Compliance with industry standards and regulations
- Integration with existing systems
Conclusion
Encryption key management is a critical aspect of data security. Implementing robust key management practices can significantly enhance the protection of sensitive information. By exploring the available solutions and carefully evaluating the factors mentioned above, organizations can choose the most appropriate key management solution to meet their specific requirements.
Data Encryption Use Cases: Real-world Applications
In today’s digital age, where data is constantly being generated, shared, and stored, data encryption has become an indispensable security measure. It involves transforming data into an unreadable format, rendering it inaccessible to unauthorized individuals. This article explores various real-world applications of data encryption, highlighting its significance in safeguarding sensitive information.
1. Financial Transactions
Financial institutions rely heavily on data encryption to protect sensitive customer information such as account numbers, credit card details, and transaction history. Encryption ensures that even if data is intercepted, it remains unreadable to hackers. This is critical in preventing fraud and identity theft, safeguarding the financial well-being of customers.
2. Healthcare Records
The healthcare industry deals with highly sensitive personal health information (PHI), including patient records, medical diagnoses, and treatment plans. Data encryption plays a vital role in protecting this information from unauthorized access. Encryption ensures that only authorized personnel can access patient data, maintaining confidentiality and complying with regulatory requirements such as HIPAA.
3. E-commerce and Online Shopping
With the rise of online shopping, data encryption is essential for securing customer data during transactions. Online retailers use encryption to protect sensitive information such as credit card numbers, billing addresses, and order history. Encryption ensures that even if a website is compromised, customer data remains protected.
4. Cloud Computing
Cloud computing services store vast amounts of data in data centers. Data encryption is crucial for safeguarding this data from unauthorized access, both during storage and transmission. Cloud providers implement various encryption techniques to ensure the confidentiality and integrity of data stored in the cloud.
5. Mobile Devices
Mobile devices store a wealth of personal information, including contact details, emails, photos, and financial data. Data encryption on mobile devices protects this information from theft or unauthorized access, even if the device is lost or stolen. Encryption ensures that the data remains inaccessible to anyone without the appropriate authorization.
Conclusion
Data encryption is an essential security measure across various industries and applications. It protects sensitive information from unauthorized access, ensuring the confidentiality and integrity of data. By implementing strong encryption techniques, organizations can mitigate risks, safeguard their reputation, and comply with regulatory requirements.
Compliance and Legal Requirements for Data Encryption

In today’s digital world, where data breaches are becoming increasingly common, data encryption plays a crucial role in protecting sensitive information. Encryption transforms data into an unreadable format, making it inaccessible to unauthorized individuals. Beyond safeguarding data from cyberattacks, encryption also helps organizations comply with various legal and regulatory requirements.
Key Compliance Regulations and Standards
Several regulations and standards mandate data encryption to ensure data privacy and security. Some of the prominent ones include:
- General Data Protection Regulation (GDPR): The GDPR requires organizations to implement appropriate technical and organizational measures, including encryption, to protect personal data.
- California Consumer Privacy Act (CCPA): Similar to GDPR, the CCPA emphasizes data security and mandates encryption for sensitive personal information.
- Payment Card Industry Data Security Standard (PCI DSS): This standard governs the handling of credit card data and mandates encryption for cardholder data at rest and in transit.
- Health Insurance Portability and Accountability Act (HIPAA): HIPAA regulations require encryption for protected health information (PHI) stored electronically.
- The Gramm-Leach-Bliley Act (GLBA): This act mandates financial institutions to protect customer financial information, including through encryption.
Benefits of Data Encryption for Compliance
Implementing data encryption provides numerous benefits for compliance, including:
- Reduced risk of data breaches: Encryption makes it difficult for unauthorized individuals to access sensitive data, minimizing the risk of data breaches and mitigating potential financial losses.
- Demonstrable compliance: Encryption serves as concrete evidence that an organization is taking appropriate measures to protect data, enhancing its compliance posture.
- Improved reputation: Complying with data privacy regulations and adopting strong security measures like encryption builds trust with customers and stakeholders, boosting the organization’s reputation.
- Enhanced legal defensibility: In the event of a data breach, encrypted data provides a strong legal defense, demonstrating that the organization took reasonable steps to protect sensitive information.
Choosing the Right Encryption Solution
The choice of encryption solution depends on various factors, including the type of data, the regulatory requirements, and the organization’s security needs. Organizations should carefully evaluate different encryption methods, such as symmetric-key encryption, asymmetric-key encryption, and homomorphic encryption, to determine the most suitable option.
Conclusion
Data encryption is not just a security best practice but also a legal necessity for many organizations. By implementing encryption solutions, organizations can effectively protect sensitive data, comply with regulatory requirements, and minimize the risk of data breaches and legal consequences. It is crucial for businesses to stay updated on evolving regulations and adopt appropriate encryption measures to ensure data privacy and security in the digital age.

