In today’s digital landscape, ransomware attacks are a growing threat, targeting individuals and organizations alike. These malicious attacks can cripple your business, steal your data, and leave you with costly recovery efforts. But fear not! This comprehensive guide will empower you with the knowledge and tools to build an impenetrable defense against ransomware threats.
By understanding the latest ransomware tactics, implementing robust security measures, and fostering a culture of cybersecurity awareness, you can protect your valuable data and minimize the risk of falling victim to these devastating attacks. From understanding the anatomy of a ransomware attack to adopting proactive security strategies, we’ll delve into every aspect of building a fortified defense that will safeguard your digital assets.
Understanding the Ransomware Threat
Ransomware is a type of malicious software that encrypts a victim’s data, making it inaccessible. The attackers then demand a ransom payment in exchange for the decryption key. This can have devastating consequences for individuals and businesses alike, leading to data loss, financial losses, and reputational damage.
How Ransomware Works
Ransomware typically spreads through phishing emails, malicious websites, or infected software. Once it gains access to a device, it will encrypt files, often using strong encryption algorithms. The attacker will then display a ransom note, demanding payment in cryptocurrency, such as Bitcoin, to regain access to the data.
Types of Ransomware
There are various types of ransomware, each with its own methods and objectives. Some of the most common types include:
- Cryptolocker: This type of ransomware encrypts files and demands payment for decryption. It was one of the first and most notorious ransomware strains.
- WannaCry: This ransomware spread rapidly in 2017, targeting vulnerable Windows systems. It used a flaw in the Windows operating system to gain access to devices.
- NotPetya: This ransomware was designed to cause maximum disruption, rather than simply demanding ransom. It overwrote data on infected devices, making recovery very difficult.
Protecting Yourself from Ransomware
While ransomware can be a serious threat, there are steps you can take to protect yourself:
- Keep your software updated: Regularly update your operating system and software programs to patch security vulnerabilities.
- Use strong passwords: Create strong, unique passwords for all your online accounts.
- Be cautious of suspicious emails and links: Don’t open emails or click on links from unknown senders.
- Back up your data: Regularly back up your important files to a separate device or cloud storage service.
- Use a reputable antivirus program: Install and keep your antivirus software updated.
What to Do if You’re Infected
If you suspect you may have been infected with ransomware, it’s crucial to act quickly:
- Disconnect from the internet: This prevents the ransomware from spreading to other devices.
- Contact your IT department or cybersecurity experts: Get professional assistance to assess the situation and develop a plan for recovery.
- Do not pay the ransom: Paying the ransom does not guarantee you’ll get your data back, and it only encourages further criminal activity.
Ransomware is a growing threat, but with proper precautions and a proactive approach to cybersecurity, you can significantly reduce your risk of falling victim.
How Ransomware Attacks Work
Ransomware is a type of malicious software that encrypts a victim’s files, making them inaccessible. The attacker then demands a ransom payment in exchange for the decryption key. Ransomware attacks can target individuals, businesses, and even governments, and they can cause significant financial and operational damage.
There are several different ways that ransomware can infect a system. One common method is through phishing emails. These emails may contain malicious attachments or links that, when clicked, download the ransomware onto the victim’s computer. Another way that ransomware can spread is through vulnerable software. If a piece of software has a security flaw, an attacker can exploit that flaw to install ransomware on the system.
Once ransomware is installed, it will typically begin to encrypt the victim’s files. This process can take anywhere from a few minutes to several hours, depending on the size and type of files being encrypted. Once the files are encrypted, they will be inaccessible to the victim until the ransom is paid.
The ransom amount demanded by attackers can vary greatly. Some attacks may demand a few hundred dollars, while others may demand thousands or even millions of dollars. The ransom amount is often determined by the severity of the attack and the value of the data that has been encrypted.
Once the ransom has been paid, the attacker will usually provide the victim with a decryption key. However, there is no guarantee that the key will work or that the attacker will not demand additional payment. In some cases, attackers may even release the decryption key publicly, making it available to anyone who has been infected.
Here are some tips to protect yourself from ransomware attacks:
- Keep your software up to date. This includes your operating system, antivirus software, and other applications.
- Be careful about what emails you open and what links you click on. Don’t open emails from unknown senders or click on links that you are not sure about.
- Back up your data regularly. This will help you to recover your files if they are encrypted by ransomware.
- Consider using a ransomware protection tool. These tools can help to detect and prevent ransomware attacks.
If you believe that you have been infected with ransomware, there are a few things you can do:
- Disconnect from the internet. This will help to prevent the ransomware from spreading to other devices.
- Do not pay the ransom. Paying the ransom does not guarantee that you will get your files back, and it may even encourage attackers to carry out more attacks.
- Contact a cybersecurity expert. They can help you to remove the ransomware and recover your files.
Ransomware is a growing threat, and it is important to take steps to protect yourself. By following the tips above, you can help to reduce your risk of becoming a victim.
Common Ransomware Attack Vectors
Ransomware is a type of malware that encrypts a victim’s files, making them inaccessible. The attackers then demand a ransom payment in exchange for the decryption key. Ransomware attacks can be devastating, causing significant financial and reputational damage. In this article, we will discuss some of the most common ransomware attack vectors.
Phishing Emails
Phishing emails are one of the most common methods used by ransomware attackers. These emails typically contain malicious attachments or links that, when clicked, download ransomware onto the victim’s computer. These emails often spoof legitimate organizations or individuals, making them appear credible. For example, an email might appear to be from a bank or credit card company, requesting that you click a link to update your account information. If you fall for this trick, you could unknowingly install ransomware on your computer.
Exploiting Vulnerabilities
Ransomware attackers often exploit vulnerabilities in software to gain access to a victim’s system. These vulnerabilities can be found in operating systems, applications, and even network devices. Attackers can use these vulnerabilities to bypass security measures and install ransomware without the user’s knowledge. This is why it is important to keep your software updated with the latest security patches.
Malicious Websites
Ransomware can also be spread through malicious websites. These websites often host drive-by downloads, where ransomware is automatically downloaded to the victim’s computer without their knowledge. These websites often contain content that is designed to entice users to click on links or download files. It is important to be aware of the websites you visit and to avoid clicking on links or downloading files from unknown sources.
Removable Media
Ransomware can also be spread through removable media, such as USB drives and external hard drives. If you insert a removable drive that has been infected with ransomware, the malware can spread to your computer. It is important to be cautious about the removable media you use and to scan it for malware before connecting it to your computer.
Social Engineering
Social engineering is a tactic that relies on human interaction to gain access to systems or information. Attackers may use deception, manipulation, or impersonation to convince victims to provide them with sensitive information or grant them access to their systems. Social engineering can be used to spread ransomware by convincing victims to open malicious attachments or click on malicious links.
Protecting Yourself
There are a number of steps you can take to protect yourself from ransomware attacks:
- Be cautious about the emails you open and the links you click.
- Keep your software up to date.
- Use a strong password and change it regularly.
- Back up your important files regularly.
- Be aware of social engineering tactics.
- Consider investing in a good security solution, such as an antivirus program or a firewall.
By taking these steps, you can significantly reduce your risk of becoming a victim of ransomware.
The Devastating Impact of Ransomware Attacks
Ransomware attacks have become increasingly common in recent years, with devastating consequences for individuals, businesses, and governments. These attacks involve malicious software that encrypts a victim’s data, rendering it inaccessible until a ransom is paid. The impact of ransomware attacks can be far-reaching, affecting not only the victim’s immediate operations but also their reputation, financial stability, and overall security posture.
One of the most significant impacts of ransomware attacks is the disruption of critical business operations. When data is encrypted, organizations may be unable to access essential files, such as customer records, financial data, and operational documents. This can lead to significant downtime, productivity losses, and revenue disruptions. In some cases, businesses may be forced to shut down operations entirely, causing significant financial damage and reputational harm.
Beyond financial losses, ransomware attacks can have serious implications for an organization’s reputation. Public awareness of a ransomware attack can damage trust in the organization, leading to customer churn, investor concerns, and a decline in brand value. The negative publicity surrounding a ransomware attack can also make it difficult for organizations to attract and retain talent.
Ransomware attacks can also have a significant impact on individual victims. Individuals may lose access to personal data, such as photos, financial records, and medical information. The loss of such data can be deeply distressing and can have lasting consequences for individuals’ financial security, personal identity, and overall well-being.
In addition to the immediate impact, ransomware attacks can have long-term consequences for security posture. Victims may need to invest significant resources in data recovery, security hardening, and incident response capabilities. They may also face regulatory scrutiny and legal liabilities related to data breaches and privacy violations.
To mitigate the impact of ransomware attacks, organizations and individuals must take proactive steps to strengthen their security defenses. This includes implementing strong passwords, using multi-factor authentication, regularly backing up data, and keeping software up to date. Organizations should also develop comprehensive incident response plans and educate employees about the risks of ransomware attacks.
The threat of ransomware is a serious challenge that requires a multi-faceted approach to address. By taking proactive measures to protect their data and systems, individuals and organizations can minimize the devastating impact of these attacks.
Essential Steps to Prevent Ransomware Attacks
Ransomware is a type of malicious software that encrypts your files, making them inaccessible until you pay a ransom to the attackers. These attacks can be devastating, causing significant financial losses and disruption to businesses and individuals alike. Fortunately, there are several steps you can take to protect yourself from ransomware attacks.
1. Keep your software up to date
Software updates often include security patches that fix vulnerabilities that attackers exploit. Make sure to install the latest updates for your operating system, antivirus software, and other applications. This will help ensure that your systems are protected against the latest ransomware threats.
2. Use strong passwords
A strong password is essential for protecting your accounts and devices. Avoid using common passwords and make sure to use a different password for each account. You should also use a password manager to help you create and store strong passwords.
3. Be cautious of email attachments
Ransomware often spreads through email attachments. Be cautious about opening attachments from unknown senders or unexpected attachments from known senders. If you’re unsure about an attachment, it’s best to contact the sender to verify its legitimacy. Also, avoid clicking on suspicious links in emails.
4. Back up your data
Regularly backing up your data is crucial for ransomware recovery. If your files are encrypted, you can restore them from a backup. Make sure to back up your data to an external drive or cloud storage. Don’t forget to test your backups regularly to ensure they are working properly.
5. Install a reputable antivirus and anti-malware software
Antivirus and anti-malware software can help detect and remove ransomware from your system. Make sure to choose a reputable software provider and keep it updated. Additionally, consider using a firewall to protect your network from unauthorized access.
6. Educate your employees
If you are a business owner, it’s important to educate your employees about ransomware threats. Train them on how to identify suspicious emails, attachments, and websites. Encourage them to report any suspicious activity to the IT department.
7. Implement a security awareness program
Regularly conduct security awareness training for employees to reinforce best practices. This will help employees stay informed about evolving cyber threats and make more informed decisions in their day-to-day work.
8. Implement a security incident response plan
Develop a detailed plan for responding to ransomware attacks. This plan should outline steps to isolate the affected system, contain the spread of the malware, and recover data from backups. It should also include communication protocols for stakeholders.
9. Consider purchasing cyber insurance
Cyber insurance can help offset the financial burden of a ransomware attack. It can cover costs associated with data recovery, legal expenses, and business interruption. Make sure to research different policies to find one that suits your needs and budget.
By taking these steps, you can significantly reduce the risk of falling victim to a ransomware attack. Remember, staying vigilant and proactive is key to protecting yourself and your business from these increasingly sophisticated threats.
Implementing a Robust Cybersecurity Strategy
In today’s digital age, cybersecurity is paramount for individuals and organizations alike. A robust cybersecurity strategy is essential to protect sensitive data, maintain operational continuity, and safeguard against cyber threats. This article will delve into the key elements of implementing a comprehensive cybersecurity strategy.
1. Risk Assessment and Threat Identification
The first step is to conduct a thorough risk assessment to identify potential threats and vulnerabilities. This involves analyzing assets, identifying potential attackers, and assessing the likelihood and impact of potential attacks. By understanding your risks, you can prioritize your security efforts and allocate resources effectively.
2. Security Policies and Procedures
Clear and comprehensive security policies and procedures are crucial for establishing a strong cybersecurity foundation. These policies should outline acceptable use of technology, data protection practices, incident response protocols, and employee responsibilities. Regularly review and update these policies to reflect evolving threats and technologies.
3. Network Security
Securing your network is paramount to preventing unauthorized access and data breaches. Implement firewalls, intrusion detection and prevention systems (IDS/IPS), and strong passwords to protect your network perimeter. Regularly patch vulnerabilities and update security software to stay ahead of attackers.
4. Endpoint Security
Endpoint devices, such as laptops, smartphones, and tablets, are often vulnerable to attacks. Implement endpoint security solutions, including antivirus software, anti-malware protection, and data loss prevention (DLP) tools. Ensure all devices are encrypted and regularly updated with the latest security patches.
5. User Education and Training
Human error is a major contributor to security breaches. Educate users about common cyber threats, phishing scams, and safe browsing practices. Implement regular security awareness training programs to foster a security-conscious culture within your organization.
6. Data Backup and Recovery
In the event of a data breach or system failure, having reliable data backups is crucial for business continuity. Implement regular data backup procedures and ensure that backups are stored securely and accessible. Test your recovery plan regularly to ensure its effectiveness.
7. Incident Response Plan
A well-defined incident response plan outlines the steps to take in the event of a security breach. This plan should include procedures for containing the incident, investigating the cause, and mitigating damage. Regularly test and update your incident response plan to ensure its effectiveness.
8. Continuous Monitoring and Improvement
Cybersecurity is an ongoing process. Continuously monitor your security posture, analyze threat intelligence, and adapt your strategy as threats evolve. Implement security information and event management (SIEM) tools to collect and analyze security data, identify anomalies, and detect potential threats.
By implementing these key elements, you can establish a robust cybersecurity strategy that protects your organization from cyber threats. Remember that cybersecurity is an ongoing process that requires continuous vigilance, adaptation, and improvement.
Educating Employees about Ransomware Threats
Ransomware is a type of malware that encrypts a victim’s files, making them inaccessible. Attackers then demand payment (usually in cryptocurrency) in exchange for a decryption key. Ransomware attacks can be devastating for individuals and businesses alike, leading to data loss, downtime, and financial losses.
One of the most effective ways to protect against ransomware is to educate employees about the threat. Employees are often the weakest link in an organization’s cybersecurity defenses, and they need to be aware of the risks and how to protect themselves.
Here are some tips for educating employees about ransomware threats:
1. Explain the basics of ransomware. Employees should understand what ransomware is, how it works, and the potential consequences of an attack.
2. Discuss common attack vectors. Ransomware can be spread in a number of ways, such as through phishing emails, malicious websites, and infected software. Employees should be aware of these attack vectors and how to avoid them.
3. Emphasize the importance of strong passwords. Strong passwords are essential for protecting against ransomware attacks. Employees should use unique and complex passwords for all of their accounts, and they should never share their passwords with anyone.
4. Encourage employees to be cautious about opening attachments and clicking on links. Phishing emails are a common way for attackers to spread ransomware. Employees should be wary of any suspicious emails, and they should never open attachments or click on links from unknown senders.
5. Explain the importance of regularly backing up data. Regular data backups are essential for recovering from a ransomware attack. Employees should be encouraged to back up their data to a separate device, such as an external hard drive or cloud storage service.
6. Train employees on how to recognize and report suspicious activity. If an employee suspects that they have been the victim of a ransomware attack, they should report it to their IT department immediately.
7. Implement a company-wide cybersecurity policy. This policy should outline the organization’s security practices and expectations for employees.
By educating employees about ransomware threats, businesses can significantly reduce their risk of becoming victims. It is important to make cybersecurity a top priority and to invest in the necessary resources to protect your organization.
Data Backup and Recovery Best Practices
Data is the lifeblood of any business, and losing it can be catastrophic. That’s why it’s essential to have a robust data backup and recovery plan in place. A good backup and recovery plan can help you minimize downtime, protect your data from loss, and ensure business continuity in the event of a disaster.
Here are some best practices for data backup and recovery:
1. Define Your Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO)
Your RPO is the maximum amount of data you’re willing to lose in the event of a disaster. Your RTO is the maximum amount of time you can afford to be down before your systems are back up and running. Once you’ve defined your RPO and RTO, you can choose a backup strategy that meets your needs.
2. Choose the Right Backup Solution
There are many different backup solutions available, so it’s important to choose one that’s right for your business. Some factors to consider include:
- The type of data you need to back up (e.g., servers, desktops, laptops, cloud data)
- The volume of data you need to back up
- Your budget
- Your recovery time objectives
Some common backup solutions include:
- On-premises backup: This involves storing your backups on physical devices, such as tapes or hard drives, located on your premises.
- Cloud backup: This involves storing your backups in the cloud, which can be a more cost-effective and scalable option.
- Hybrid backup: This combines on-premises and cloud backup solutions, offering the best of both worlds.
3. Test Your Backup and Recovery Plan Regularly
It’s essential to test your backup and recovery plan regularly to ensure it’s working properly. This involves restoring data from your backups and verifying that it’s complete and accurate. You should also test your backup and recovery plan after any significant changes to your IT infrastructure, such as the installation of new software or hardware.
4. Implement Data Security Measures
Data security is essential to protect your data from unauthorized access, use, disclosure, disruption, modification, or destruction. Some data security measures to implement include:
- Encryption: Encrypting your data can help protect it from unauthorized access.
- Access control: Restricting access to your data to authorized users can help prevent unauthorized access.
- Data loss prevention (DLP): DLP solutions can help prevent sensitive data from leaving your organization.
5. Document Your Backup and Recovery Plan
A well-documented backup and recovery plan will help you to quickly recover from a disaster. Your plan should include:
- A description of your backup strategy
- A list of all your backup systems and storage locations
- Procedures for restoring data from your backups
- Contact information for key personnel involved in the backup and recovery process
By following these best practices, you can ensure that your data is protected and that your business can recover quickly from any disaster.
The Role of Security Software in Ransomware Prevention
Ransomware is a type of malware that encrypts a victim’s data and demands payment for its decryption. It is a serious threat to individuals and businesses alike, and can cause significant financial and operational damage. Security software plays a critical role in ransomware prevention, and its importance cannot be overstated. By implementing comprehensive security measures, individuals and businesses can significantly reduce their risk of falling victim to ransomware attacks.
Key Security Software Features for Ransomware Prevention
Security software provides a variety of features that are essential for preventing ransomware attacks. Some of the most important features include:
- Antivirus Protection: Antivirus software detects and removes known ransomware threats. It scans files and programs for malicious code and can block or quarantine suspicious files.
- Firewall: A firewall acts as a barrier between your device and the internet, blocking unauthorized access and preventing malicious software from entering your system.
- Behavioral Analysis: Advanced security software uses behavioral analysis to detect suspicious activity on your device. It monitors for unusual file access patterns, encryption attempts, and other signs of ransomware infection.
- Real-time Protection: Real-time protection continuously monitors your system for threats and provides instant alerts and blocking mechanisms. It can prevent ransomware from running or spreading before it causes any damage.
- Data Backup: Regular data backups are essential for recovering data that has been encrypted by ransomware. Even if the attack is successful, you can restore your data from a backup.
Benefits of Security Software for Ransomware Prevention
Investing in robust security software offers numerous benefits for ransomware prevention:
- Reduced Risk of Infection: Security software significantly reduces the risk of ransomware infection by detecting and blocking threats before they can compromise your device.
- Data Protection: Security software helps protect your data from encryption by ransomware. It can detect and prevent malicious activity that attempts to encrypt your files.
- Reduced Downtime: If a ransomware attack occurs, security software can help minimize downtime by quickly identifying and containing the infection. This reduces the time it takes to recover your data and resume normal operations.
- Financial Savings: By preventing ransomware attacks, security software can save you from significant financial losses associated with data recovery, ransom payments, and business disruptions.
- Peace of Mind: Implementing comprehensive security measures provides peace of mind knowing that your devices and data are protected from ransomware threats.
Conclusion
Security software plays a crucial role in preventing ransomware attacks. By utilizing features like antivirus protection, firewalls, behavioral analysis, and real-time protection, you can significantly reduce the risk of falling victim to these malicious threats. It is essential to invest in reputable security software and maintain regular updates to ensure optimal protection against evolving ransomware threats.
Network Security Measures for Ransomware Protection
Ransomware has become a significant threat to businesses and individuals alike. It encrypts your data and demands a ransom payment for its decryption. This article will discuss effective network security measures you can implement to protect your organization against ransomware attacks.
Strong Passwords and Multi-Factor Authentication (MFA)
Start with the basics: enforce strong passwords for all accounts, encourage users to utilize unique passwords for different accounts, and implement multi-factor authentication (MFA). MFA adds an extra layer of security by requiring users to provide two or more forms of identification before granting access. This significantly reduces the risk of unauthorized access, even if a password is compromised.
Regular Software Updates and Patches
Cybercriminals often exploit vulnerabilities in outdated software to infiltrate networks. Keep all software, including operating systems, applications, and antivirus programs, up to date with the latest patches. These updates frequently contain security fixes that can patch vulnerabilities exploited by ransomware. Automatic updates are recommended to ensure prompt patching.
Network Segmentation and Access Control
Network segmentation divides a network into smaller, isolated segments. Limiting access to sensitive data by segmenting the network reduces the impact of a ransomware attack. Implement access control lists (ACLs) to restrict access to critical resources based on user roles and permissions. This approach restricts the spread of ransomware within the network.
Backup and Recovery Strategies
A robust backup and recovery plan is crucial for ransomware protection. Regularly back up your critical data and store backups offline or in a separate, secure location. This ensures that you can recover your data even if ransomware encrypts your primary systems. Regularly test your backup and recovery procedures to ensure they function effectively.
Employee Training and Awareness
Employee education is a vital component of ransomware defense. Train your employees to recognize and avoid common phishing scams, suspicious emails, and malicious websites. Encourage them to report any suspicious activities promptly to the IT security team. Teach employees to be vigilant and cautious while browsing the web and opening attachments.
Network Monitoring and Intrusion Detection Systems (IDS)
Utilize network monitoring tools and intrusion detection systems (IDS) to detect unusual network activity, suspicious traffic patterns, and potential ransomware attacks. These tools can help identify and block malicious activity in real time. Regularly analyze security logs for potential indicators of compromise (IOCs) to identify and respond to threats.
Data Encryption
Encrypt sensitive data at rest and in transit. Encryption adds an extra layer of protection, even if ransomware gains access to your network. Consider implementing data loss prevention (DLP) solutions to prevent unauthorized data transfers.
Endpoint Security
Implement endpoint security solutions like antivirus, endpoint detection and response (EDR), and next-generation firewalls (NGFW) on all devices connected to the network. These solutions can detect and prevent malware, including ransomware, from executing on devices and compromising data. Regularly update these security tools and configure them appropriately.
Incident Response Plan
Develop a comprehensive incident response plan to guide your actions in the event of a ransomware attack. This plan should outline steps to contain the attack, recover data, and restore operations. Regularly test and refine this plan to ensure its effectiveness.
Conclusion
Ransomware poses a serious threat to businesses and individuals. By implementing these network security measures, you can significantly reduce the risk of a successful ransomware attack. Regularly review and update your security practices to stay ahead of evolving threats. Proactive security measures are critical to protecting your data and ensuring business continuity.
Responding to a Ransomware Attack

A ransomware attack can be a devastating event for any organization, causing significant disruption, financial losses, and reputational damage. It’s crucial to have a well-defined plan in place to respond effectively and minimize the impact. This article outlines key steps to take when facing a ransomware attack.
1. Containment
The first priority is to contain the attack and prevent further spread. This involves isolating infected systems from the network, disconnecting from the internet, and disabling any shared resources.
2. Assess the Impact
Once containment is in place, it’s essential to assess the extent of the attack. Identify the affected systems, data, and the potential impact on business operations. This helps determine the best course of action and prioritize recovery efforts.
3. Investigate the Attack
Investigate the attack to understand how it occurred. Determine the entry point, the ransomware variant used, and the affected systems. This information is crucial for future security improvements.
4. Data Recovery
Data recovery is a critical part of the response. If backups are available, restore affected systems from a clean backup. If backups are not available, consider data recovery services or negotiate with the attackers if possible.
5. Incident Reporting
Report the incident to the appropriate authorities, including law enforcement and cybersecurity agencies. This can help in identifying and pursuing the attackers.
6. System Restoration
After data recovery, restore the affected systems. This involves reinstalling operating systems, applications, and configuring security settings. Implement strong security measures to prevent future attacks.
7. Post-Attack Review
Once the attack is contained and systems are restored, conduct a post-attack review. This involves analyzing the incident to identify vulnerabilities and weaknesses in security controls. Implement necessary improvements to prevent similar attacks in the future.
8. Remediation
Remediate any vulnerabilities identified during the investigation and review. This may involve patching systems, updating software, and implementing new security measures.
9. Communication
Maintain open communication with stakeholders, including employees, customers, and partners. Inform them about the incident and the steps taken to address it. Transparency is essential to rebuilding trust.
10. Prevention
Proactive security measures are essential to prevent future ransomware attacks. Implement strong passwords, multi-factor authentication, regular backups, and employee security training. Stay informed about the latest threats and vulnerabilities.
Responding to a ransomware attack requires a comprehensive and coordinated approach. A well-defined plan, swift action, and a focus on prevention can help mitigate the impact and protect your organization.
Recovering from a Ransomware Attack
A ransomware attack can be a devastating event for any organization. Not only can it result in the loss of valuable data, but it can also disrupt business operations and cause significant financial damage. If you’ve been hit by ransomware, it’s important to act quickly and decisively to minimize the impact. Here’s a step-by-step guide to help you recover from a ransomware attack:
1. Isolate the Infected Systems
The first step is to isolate the infected systems from your network. This will prevent the ransomware from spreading to other devices. If possible, disconnect the infected systems from the internet and any other network connections. You can also consider using a firewall to block traffic to and from the infected systems.
2. Backup and Restore
If you have a recent backup of your data, you can restore your systems to a clean state. This is the most effective way to recover from a ransomware attack. However, it’s important to make sure that the backup is not infected. You should also consider using a different backup solution to avoid future attacks.
3. Contact Your Security Provider
Contact your security provider for assistance in containing and removing the ransomware. They may have expertise in dealing with ransomware attacks and can provide valuable guidance.
4. Consider Paying the Ransom
Paying the ransom is a controversial decision. While it may seem like the quickest way to get your data back, there’s no guarantee that the attackers will actually provide you with a decryption key. Furthermore, paying the ransom can encourage further attacks. You may consider paying the ransom if you are in a situation where data loss is catastrophic and backup options are inadequate.
5. Report the Attack to Authorities
Report the ransomware attack to the appropriate authorities, such as the FBI or your local law enforcement agency. This will help law enforcement investigate the attack and potentially track down the attackers.
6. Learn From the Experience
After you’ve recovered from the attack, it’s important to take steps to prevent similar attacks in the future. This includes implementing strong security measures, such as:
- Using strong passwords and multi-factor authentication.
- Keeping your software up to date.
- Training employees on cybersecurity best practices.
- Regularly backing up your data.
- Investing in robust security tools such as endpoint protection, firewalls, and intrusion detection systems.
Conclusion
A ransomware attack can be a challenging experience, but it’s important to remember that you’re not alone. By taking swift action and following these steps, you can minimize the impact of a ransomware attack and protect your organization from future attacks.
The Importance of Incident Response Planning
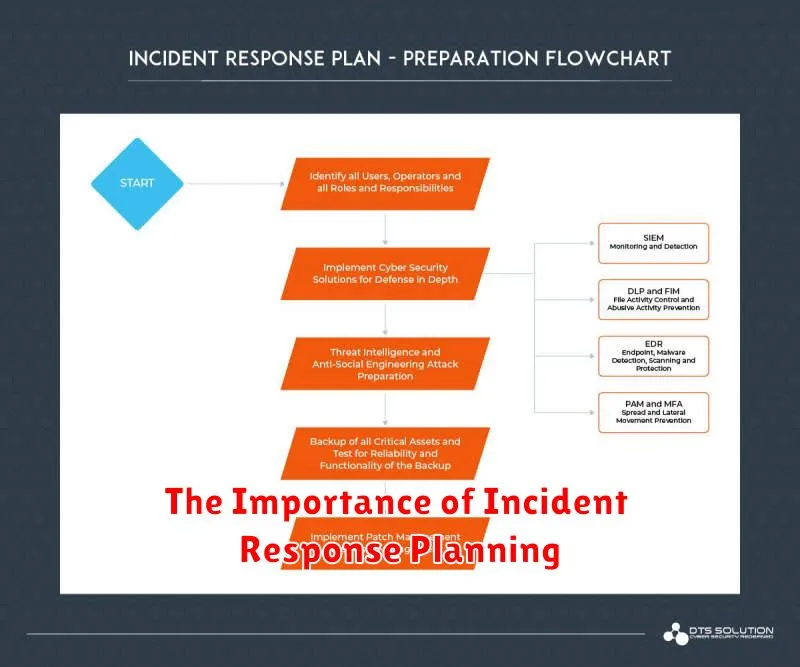
In today’s digital world, businesses are increasingly vulnerable to cyberattacks. From data breaches to ransomware attacks, the consequences of a security incident can be devastating. This is why it is essential for organizations of all sizes to have a comprehensive incident response plan in place.
An incident response plan is a documented set of instructions that outlines how an organization will respond to a security incident. This plan should cover all aspects of the incident response process, from initial detection to recovery. A well-defined incident response plan can help organizations:
- Minimize the impact of a security incident
- Recover from a security incident quickly and efficiently
- Maintain business continuity
- Protect sensitive data
- Comply with regulatory requirements
Key Components of an Incident Response Plan
A comprehensive incident response plan should include the following key components:
- Incident identification and reporting: This component outlines the process for identifying and reporting security incidents. It should include clear definitions of what constitutes an incident and the appropriate channels for reporting.
- Incident containment: This component outlines the steps that should be taken to contain the incident and prevent further damage. This may involve isolating affected systems, shutting down services, or implementing other security measures.
- Incident analysis and investigation: This component outlines the process for analyzing the incident and determining its root cause. This may involve collecting evidence, interviewing witnesses, and conducting forensic analysis.
- Incident recovery: This component outlines the steps that should be taken to recover from the incident and restore normal operations. This may involve restoring data, rebuilding systems, or implementing new security controls.
- Incident communication: This component outlines the process for communicating with stakeholders during and after the incident. This may involve notifying affected individuals, issuing press releases, or working with law enforcement.
Benefits of Incident Response Planning
There are many benefits to having a well-defined incident response plan in place. These benefits include:
- Improved security posture: An incident response plan forces organizations to think about their security weaknesses and develop strategies for mitigating them.
- Faster incident response times: A well-defined incident response plan helps organizations respond to security incidents more quickly and efficiently.
- Reduced business disruption: An incident response plan helps minimize the impact of a security incident on business operations.
- Improved compliance: An incident response plan can help organizations comply with regulatory requirements.
- Enhanced reputation: A well-defined incident response plan can help organizations demonstrate their commitment to security and protect their reputation.
Conclusion
In conclusion, an incident response plan is a critical component of any organization’s security strategy. By having a plan in place, organizations can minimize the impact of security incidents, recover quickly, and protect their business from the devastating consequences of a cyberattack.
The Future of Ransomware Prevention
Ransomware is a type of malicious software that encrypts a victim’s data and demands payment for its decryption. It has become increasingly prevalent in recent years, costing businesses and individuals billions of dollars. As ransomware attacks continue to evolve, so too must our defenses. The future of ransomware prevention lies in a multi-layered approach that combines technological solutions with human awareness and education.
Advanced Endpoint Protection: Traditional antivirus software is no longer enough to protect against the sophisticated attacks used by ransomware actors. Next-generation endpoint protection solutions are essential. These solutions leverage artificial intelligence (AI) and machine learning (ML) to detect and prevent threats before they can execute.
Zero Trust Security: The zero-trust security model assumes that no user or device can be trusted by default. This approach involves verifying all users and devices before granting access to sensitive data. It also includes techniques like multi-factor authentication (MFA) and access control lists (ACLs) to limit access to critical systems.
Data Backup and Recovery: Even the most robust security measures can be breached. A comprehensive data backup and recovery strategy is essential. This involves regularly backing up important data to a secure location, such as the cloud, and testing the recovery process to ensure it is effective.
Employee Training: A key element in ransomware prevention is employee awareness and training. Educating employees about the risks of ransomware, common attack vectors, and best practices for avoiding infection is crucial. Regular phishing simulations can help test and improve employee awareness.
Cybersecurity Automation: Automating security tasks, such as vulnerability scanning and patch management, can free up security teams to focus on more strategic initiatives. Automation can also help to improve response times to security incidents.
The future of ransomware prevention requires a commitment to continuous improvement. Organizations must stay ahead of the curve by adopting new technologies and adapting their security practices to the ever-evolving threat landscape. By taking a proactive approach, businesses and individuals can better protect themselves from the devastating impact of ransomware.

