In the digital age, our data is more valuable than ever before. From our browsing history to our social media interactions, every click and every swipe leaves a trail of information that companies can use to understand our habits, preferences, and even our vulnerabilities. This raises critical questions about data privacy and the rights we have over our own information. As we enter 2024 and beyond, the landscape of data privacy is evolving at an unprecedented pace, with new regulations, technologies, and societal expectations shaping the way we interact with data.
Navigating this complex and ever-changing landscape requires a nuanced understanding of the challenges and opportunities it presents. This article will delve into the key trends shaping data privacy in 2024 and beyond, exploring topics such as emerging regulations, the rise of data privacy technologies, the evolving role of businesses in protecting user data, and the increasing awareness and activism around data privacy rights. By understanding these trends, individuals and organizations can make informed decisions about how to protect their data and ensure responsible data practices in the digital age.
The Evolving Landscape of Data Privacy Regulations
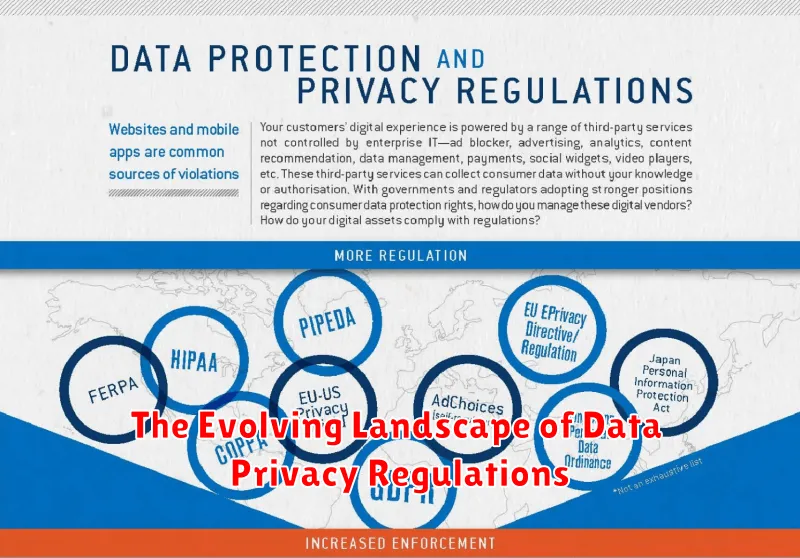
In the digital age, data has become a valuable asset. It fuels businesses, powers innovation, and shapes our online experiences. However, the collection and use of personal data raise significant privacy concerns. As technology advances and data flows across borders, the need for robust data privacy regulations has become increasingly urgent.
The landscape of data privacy regulations is constantly evolving, driven by a growing awareness of the potential harms of data misuse and the increasing sophistication of data collection and analysis techniques. From the European Union’s General Data Protection Regulation (GDPR) to California’s California Consumer Privacy Act (CCPA), jurisdictions around the world are enacting new laws to protect individuals’ rights to privacy.
These regulations establish frameworks for the collection, processing, and storage of personal data, placing significant obligations on organizations that handle such data. Key principles include:
- Transparency and Consent: Individuals must be informed about how their data is being used and have the right to consent to its collection and processing.
- Purpose Limitation: Data should only be collected for specified, legitimate purposes and not used for any other purpose without consent.
- Data Minimization: Only the necessary data should be collected and processed.
- Data Security: Organizations must implement appropriate technical and organizational measures to protect personal data from unauthorized access, use, disclosure, alteration, or destruction.
- Individual Rights: Individuals have the right to access, correct, delete, and restrict the processing of their data.
The implications of these regulations are far-reaching. Organizations must adapt their practices and technologies to comply with these new requirements. This includes implementing data privacy policies, conducting data audits, training employees, and establishing robust data security protocols. Failure to comply can result in significant fines and reputational damage.
The evolving landscape of data privacy regulations presents both challenges and opportunities. While it requires organizations to invest time and resources in compliance, it also creates an environment of trust and transparency, fostering a more secure and ethical data ecosystem. By understanding and embracing these regulations, organizations can navigate the changing landscape, protect individual rights, and build a more responsible data-driven future.
Key Data Privacy Laws in 2024: A Global Overview

In the ever-evolving digital landscape, data privacy has become a paramount concern. As businesses increasingly collect and utilize personal data, the need for robust legal frameworks to protect individuals’ rights has grown exponentially. 2024 sees a continued surge in data privacy legislation worldwide, with new laws emerging and existing ones being refined. This comprehensive guide explores some of the key data privacy laws that will shape the global regulatory landscape in 2024.
The General Data Protection Regulation (GDPR) – Europe
The GDPR, which came into effect in 2018, remains a cornerstone of data privacy regulations in the European Union (EU). It mandates stringent data processing principles, including lawful, fair, and transparent processing, purpose limitation, data minimization, and accuracy. The GDPR also grants individuals robust rights concerning their personal data, such as the right to access, rectification, erasure, and restriction of processing.
The California Consumer Privacy Act (CCPA) – United States
California has been at the forefront of data privacy legislation in the US with the CCPA. This law grants California residents the right to know what personal data businesses collect about them, the right to delete that data, and the right to opt-out of the sale of their personal information. The CCPA also imposes specific obligations on businesses regarding data security and breach notification.
The Brazil General Data Protection Law (LGPD) – Brazil
Brazil’s LGPD, which entered into force in 2020, is a comprehensive data protection law that aligns with the GDPR in many aspects. It establishes principles for data processing, requires data controllers to obtain consent for data collection and use, and grants individuals the right to access, rectification, and erasure of their personal data. The LGPD also has provisions for data breach notification and penalties for non-compliance.
The Personal Information Protection Law (PIPL) – China
China’s PIPL, which came into effect in 2021, has significantly impacted data privacy practices in the country. It governs the processing of personal information of individuals within China and imposes strict requirements on data controllers, including obtaining consent for data collection, ensuring data security, and adhering to data localization provisions.
The Asia-Pacific Economic Cooperation (APEC) Cross-Border Privacy Rules (CBPR) System
The APEC CBPR System provides a framework for organizations to comply with data protection requirements in participating APEC economies. It promotes cross-border data flows while ensuring the protection of personal information. The CBPR System encourages organizations to adhere to a set of principles, including notice, choice, access, and security.
Global Trends in Data Privacy
The global data privacy landscape is continuously evolving, with several trends emerging. These include:
- Increased focus on data minimization: Data privacy laws are increasingly emphasizing the principle of data minimization, requiring organizations to collect and retain only the data that is absolutely necessary for their purposes.
- Expansion of data subject rights: Individuals are gaining more control over their personal data, with laws granting them rights to access, rectify, and delete their information.
- Emphasis on data security and breach notification: Data privacy laws are placing a strong emphasis on data security, requiring organizations to implement appropriate technical and organizational measures to protect personal data from unauthorized access, use, or disclosure. Organizations are also obligated to promptly notify individuals and relevant authorities of data breaches.
- Emergence of sector-specific regulations: Regulatory frameworks are being tailored to address the unique privacy needs of specific sectors, such as healthcare, finance, and education.
Challenges and Opportunities
The increasing complexity of data privacy laws presents challenges for organizations. Maintaining compliance across jurisdictions requires a comprehensive understanding of applicable regulations, careful planning, and ongoing monitoring. However, the growing focus on data privacy also presents opportunities. Organizations that prioritize data protection and implement robust privacy practices can gain a competitive advantage by building trust with their customers and stakeholders. They can also avoid costly fines and legal repercussions associated with data privacy breaches.
Conclusion
The data privacy landscape in 2024 is dynamic and complex. Organizations must remain vigilant about evolving regulations and adapt their data practices to ensure compliance. By embracing data privacy principles, businesses can foster a culture of trust, protect individuals’ rights, and navigate the regulatory landscape successfully.
The Impact of Emerging Technologies on Data Privacy

The rapid advancement of emerging technologies has significantly impacted various aspects of our lives, including data privacy. Technologies like artificial intelligence (AI), the Internet of Things (IoT), and cloud computing have revolutionized how we collect, store, and use data. While these technologies offer numerous benefits, they also raise concerns about the potential for data breaches and privacy violations.
AI and Data Privacy
AI algorithms heavily rely on vast amounts of data for training and operation. This dependence raises concerns about the potential misuse of personal data. For instance, facial recognition systems, powered by AI, can identify individuals in public spaces without their consent. The use of AI for targeted advertising can also lead to the profiling and manipulation of individuals based on their online behavior.
IoT and Data Security
The proliferation of connected devices in the IoT ecosystem generates an unprecedented volume of data. These devices often collect sensitive information, including location data, health data, and financial transactions. The lack of robust security measures in some IoT devices makes them vulnerable to cyberattacks, potentially exposing users’ personal data.
Cloud Computing and Data Protection
Cloud computing offers convenient data storage and access, but it also introduces new challenges for data protection. Data stored in the cloud may be subject to unauthorized access or breaches, especially if the cloud provider has weak security protocols. The use of cloud services for sensitive data requires careful consideration of data encryption, access control, and compliance with data privacy regulations.
Challenges and Mitigation Strategies
The impact of emerging technologies on data privacy presents significant challenges. Governments, organizations, and individuals must work collaboratively to mitigate these risks.
- Data Minimization: Organizations should collect and store only the data necessary for their specific purposes.
- Data Encryption: Encryption protects data in transit and at rest, making it incomprehensible to unauthorized parties.
- Privacy-Preserving Technologies: Techniques like differential privacy and federated learning can enhance data privacy while enabling data analysis.
- Data Governance: Establishing clear data governance policies and procedures is crucial for responsible data handling.
- Public Awareness: Raising public awareness about data privacy issues is essential to empower individuals to protect their own information.
Conclusion
Emerging technologies are transforming the data landscape, posing both opportunities and challenges for data privacy. By implementing appropriate safeguards and promoting responsible data practices, we can harness the benefits of these technologies while protecting the fundamental right to privacy. The future of data privacy hinges on our collective efforts to navigate this evolving technological landscape with caution and foresight.
Data Minimization and Purpose Limitation: Core Principles

In the realm of data privacy and security, two fundamental principles stand tall: data minimization and purpose limitation. These principles, often intertwined, serve as cornerstones for ethical and responsible data handling practices. Let’s delve into their essence, understanding their significance and how they safeguard our information.
Data Minimization: Only Collect What You Need
Data minimization dictates that organizations should only collect, store, and process the data that is strictly necessary for the stated purpose. It’s about avoiding data bloat and focusing solely on the essentials. This principle has several advantages:
- Reduced Risk: Less data means fewer potential vulnerabilities and a decreased risk of breaches, leaks, or unauthorized access.
- Enhanced Efficiency: Streamlining data collection and storage improves operational efficiency, reducing the burden on resources and infrastructure.
- Improved Privacy: By collecting only essential information, organizations minimize the potential for misuse or inappropriate disclosure of sensitive data.
Purpose Limitation: Clear and Specific Use Cases
Purpose limitation demands that data should only be used for the specific and legitimate purpose for which it was collected. This means avoiding “data creep” – the unauthorized expansion of data use beyond its original intention.
Imagine signing up for a newsletter and suddenly receiving targeted ads based on your personal preferences. This scenario could violate the principle of purpose limitation, as the data collected for newsletter subscriptions should not be repurposed for advertising without your informed consent.
The Power of Combined Application
When combined, data minimization and purpose limitation create a powerful shield for data privacy. They work together to:
- Prevent Data Overcollection: By focusing on the minimum necessary data and its intended use, organizations limit the potential for excessive data gathering.
- Establish Clear Boundaries: Defining specific purposes for data use sets clear boundaries, ensuring transparency and accountability.
- Foster Trust: By adhering to these principles, organizations demonstrate respect for user privacy, building trust and confidence.
Implementing Data Minimization and Purpose Limitation
Organizations can effectively implement these principles through:
- Conducting Data Audits: Regularly review data holdings to identify unnecessary information and eliminate it.
- Implementing Data Minimization Policies: Establish guidelines that specify the minimum data required for various purposes.
- Obtaining Explicit Consent: Clearly communicate the purpose of data collection and obtain explicit consent from individuals before collecting their data.
Conclusion: A Foundation for Responsible Data Handling
Data minimization and purpose limitation are not just legal requirements but ethical imperatives. By embracing these core principles, organizations can create a responsible and transparent data handling environment, safeguarding individual privacy and building trust in the digital world.
Strengthening Data Security Measures

In today’s digital age, data is a valuable asset that needs to be protected. With the increasing prevalence of cyberattacks, it’s more important than ever to strengthen data security measures. Implementing robust security measures can help organizations safeguard sensitive information, minimize risks, and maintain customer trust. Here are some essential strategies for strengthening data security:
1. Implement Strong Authentication
Strong authentication is the first line of defense against unauthorized access. Two-factor authentication (2FA) adds an extra layer of security by requiring users to provide two different forms of identification, such as a password and a one-time code sent to their mobile device. Multi-factor authentication (MFA) goes further by requiring multiple forms of authentication, such as a password, a fingerprint scan, and a security key.
2. Encrypt Data at Rest and in Transit
Encryption is crucial for protecting data from unauthorized access, even if the system is compromised. Data encryption at rest ensures that data stored on hard drives, servers, and other storage devices is scrambled and unreadable to unauthorized individuals. Data encryption in transit protects data while it’s being transmitted between systems, such as when sending emails or accessing cloud services.
3. Regularly Update Software and Systems
Software vulnerabilities can create security loopholes that hackers can exploit. Regularly updating software and systems is essential to patch security flaws and protect against known vulnerabilities. Keeping systems up-to-date ensures that the latest security patches are applied, reducing the risk of attacks.
4. Implement a Secure Network Infrastructure
A secure network infrastructure is essential for protecting data from external threats. This includes using strong firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to monitor network traffic and prevent unauthorized access. Implementing network segmentation can also help isolate sensitive data and prevent attackers from spreading across the network.
5. Train Employees on Security Best Practices
Employees are often the weakest link in data security. It’s crucial to train employees on security best practices, such as recognizing phishing emails, using strong passwords, and reporting suspicious activities. Regular security awareness training can help educate employees about potential threats and equip them with the knowledge to protect sensitive information.
6. Implement a Data Loss Prevention (DLP) Solution
Data loss prevention (DLP) solutions can help prevent sensitive data from leaving the organization’s network. DLP solutions can monitor data in real-time, detect suspicious activities, and block unauthorized data transfers. They can also enforce policies to restrict data access and prevent accidental or intentional data leaks.
7. Conduct Regular Security Audits
Regular security audits are essential to identify vulnerabilities and assess the effectiveness of existing security measures. These audits should be conducted by independent security professionals who can provide an objective assessment of the organization’s security posture. Audits can help uncover hidden risks and identify areas for improvement.
8. Implement a Comprehensive Security Incident Response Plan
In the event of a data breach, it’s crucial to have a comprehensive security incident response plan in place. This plan should outline steps to contain the breach, mitigate damage, and recover lost data. It should also include procedures for notifying relevant stakeholders, such as law enforcement and affected individuals.
Strengthening data security measures is an ongoing process. By implementing these strategies, organizations can significantly reduce their risk of data breaches and protect sensitive information. Continuous vigilance, adaptation to evolving threats, and a commitment to security best practices are essential for safeguarding data in the digital age.
Navigating Consent and Data Subject Rights
In the digital age, where data is the new currency, understanding the concepts of consent and data subject rights is crucial for both individuals and organizations. This article will delve into these critical aspects, providing insights into their significance and how they shape the landscape of data privacy.
What is Consent?
Consent refers to the voluntary, informed, specific, and unambiguous agreement by an individual to the processing of their personal data. It’s a fundamental pillar of data protection, ensuring individuals have control over their information. To be valid, consent must be freely given, without any coercion or undue influence.
Data Subject Rights: Empowering Individuals
Data subject rights are a set of legal rights granted to individuals concerning their personal data. These rights are designed to empower individuals and give them control over how their information is used. Some key data subject rights include:
- Right to access: Individuals have the right to access their personal data held by an organization.
- Right to rectification: Individuals can request the correction of inaccurate or incomplete data.
- Right to erasure (right to be forgotten): In certain circumstances, individuals can request the deletion of their personal data.
- Right to restriction of processing: Individuals can request the limitation of processing their data in specific cases.
- Right to data portability: Individuals have the right to receive their personal data in a portable format.
- Right to object: Individuals can object to the processing of their data based on legitimate interests or direct marketing.
The Importance of Transparency
Transparency is essential when dealing with data. Organizations should be upfront with individuals about how they collect, use, and store personal data. Clear and concise privacy policies, along with readily available information about data subject rights, are vital to fostering trust and compliance.
Navigating the Legal Landscape
Data protection laws, such as the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States, have established a legal framework for data privacy. These regulations provide guidance on consent, data subject rights, and other aspects of data processing.
Key Considerations
Here are some key considerations for organizations and individuals when navigating consent and data subject rights:
- Obtain clear and unambiguous consent before processing personal data.
- Ensure individuals are fully informed about how their data will be used.
- Respect data subject rights and comply with relevant data protection laws.
- Implement robust data security measures to protect personal information.
- Regularly review and update privacy policies to reflect changes in data processing practices.
Conclusion
Consent and data subject rights are integral to responsible data handling. Organizations must prioritize transparency, respect individual autonomy, and comply with applicable regulations. By embracing these principles, we can create a more secure and trustworthy digital environment for all.
Cross-Border Data Transfers and Compliance Challenges

In today’s globalized world, businesses often operate across borders, necessitating the transfer of data between countries. This raises significant challenges in ensuring compliance with various data protection laws and regulations. The transfer of personal data from one country to another can be complex and subject to strict rules, making it crucial for organizations to understand the legal framework and implement appropriate measures to protect sensitive information.
Key Considerations for Cross-Border Data Transfers
When transferring personal data across borders, businesses must consider several key factors:
- Data Protection Laws in the Origin and Destination Countries: Each country has its own data protection laws, including the General Data Protection Regulation (GDPR) in the European Union, the California Consumer Privacy Act (CCPA) in the United States, and the Personal Information Protection and Electronic Documents Act (PIPEDA) in Canada. Businesses must comply with the laws of both the country where the data originates and the country where it is being transferred.
- Data Transfer Mechanisms: There are various mechanisms for transferring data across borders, including:
- Standard Contractual Clauses (SCCs): These are pre-approved contracts that organizations can use to transfer data between EU countries and countries outside the EU.
- Binding Corporate Rules (BCRs): These are internal company rules that allow for data transfers between different branches of the same company, provided they meet certain requirements.
- Data Protection Impact Assessments (DPIAs): These assessments help organizations identify and mitigate risks associated with data transfers.
- Legitimate Interests: In some cases, organizations can rely on legitimate interests as a legal basis for data transfers.
- Data Subject Rights: Data subjects have certain rights related to their personal data, such as the right to access, rectification, erasure, and restriction of processing. These rights must be respected regardless of where the data is transferred.
- Enforcement and Penalties: Failure to comply with data protection laws can result in significant fines and penalties. Organizations must understand the enforcement mechanisms and potential consequences in the countries involved in the data transfer.
Best Practices for Cross-Border Data Transfers
To minimize risks and ensure compliance, businesses should adopt the following best practices:
- Conduct a Comprehensive Data Mapping Exercise: Identify all personal data that is being transferred, including the type of data, source, destination, and purpose of transfer.
- Perform Due Diligence on Data Recipients: Ensure that the recipient of the data has appropriate data protection policies and practices in place.
- Implement Appropriate Technical and Organizational Measures: Use encryption, access controls, and other measures to protect the data during transfer.
- Obtain Consent and Provide Clear Information to Data Subjects: Inform individuals about how their data will be used and transferred, and obtain their consent if necessary.
- Regularly Review and Update Data Transfer Practices: Keep up with changes in data protection laws and regulations, and adjust data transfer practices accordingly.
Conclusion
Cross-border data transfers are an integral part of many businesses, but they present unique challenges in ensuring compliance with data protection laws. By understanding the legal framework, adopting best practices, and implementing appropriate security measures, organizations can mitigate risks, protect sensitive information, and maintain trust with data subjects.
The Role of Privacy Professionals in 2024 and Beyond
The landscape of data privacy is constantly evolving, driven by technological advancements, changing regulations, and evolving societal expectations. In this dynamic environment, the role of privacy professionals has become increasingly crucial. As we enter 2024 and beyond, privacy professionals are expected to play a pivotal role in navigating the complexities of data privacy and ensuring responsible data handling practices.
In 2024 and beyond, the role of privacy professionals will encompass several key areas:
1. Navigating a Complex Regulatory Landscape
The data privacy landscape is becoming increasingly complex, with a proliferation of regulations worldwide. The General Data Protection Regulation (GDPR) in the European Union, the California Consumer Privacy Act (CCPA) in the United States, and similar legislation in other jurisdictions have significantly raised the bar for data protection. Privacy professionals will need to navigate this intricate regulatory framework, ensuring compliance with all applicable laws and standards.
2. Addressing Emerging Privacy Technologies
The rapid pace of technological innovation is constantly introducing new privacy challenges. Technologies such as artificial intelligence (AI), the Internet of Things (IoT), and blockchain are transforming data collection and processing, creating new opportunities and risks. Privacy professionals will need to stay ahead of the curve, understanding the privacy implications of emerging technologies and developing strategies to mitigate potential risks.
3. Building Trust and Transparency
In an era of heightened data privacy concerns, building trust and transparency is paramount. Privacy professionals will play a critical role in communicating privacy policies and practices to individuals, fostering transparency and building confidence in how organizations handle personal data. This will involve developing clear and concise privacy policies, implementing robust data security measures, and providing individuals with meaningful control over their data.
4. Advocating for Responsible Data Use
Privacy professionals will need to champion responsible data use practices within their organizations and advocate for ethical data handling principles. This involves promoting data minimization, ensuring data security, and fostering a culture of data privacy awareness among employees. By advocating for responsible data use, privacy professionals can help ensure that organizations use data ethically and responsibly.
5. Adapting to a Data-Driven World
Organizations are increasingly relying on data to make decisions and improve operations. Privacy professionals will need to adapt to this data-driven environment, balancing the needs for data-driven innovation with the protection of individuals’ privacy. This will involve developing data governance frameworks that strike a balance between data utilization and privacy protection.
In conclusion, the role of privacy professionals in 2024 and beyond is essential for navigating the complex and evolving data privacy landscape. By navigating regulations, addressing emerging technologies, building trust and transparency, advocating for responsible data use, and adapting to a data-driven world, privacy professionals will play a vital role in shaping a future where data is used ethically and responsibly.
Building a Culture of Data Privacy within Organizations

In today’s digital age, where data is the new gold, organizations face a critical challenge: balancing innovation and growth with responsible data handling. The increasing awareness of data privacy and the implementation of regulations like the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have made it imperative for businesses to prioritize data privacy and build a robust culture around it.
A culture of data privacy goes beyond mere compliance; it’s a mindset that permeates every aspect of an organization, from leadership to employees. It’s about embedding data privacy principles into every business decision, ensuring that data is handled ethically and responsibly.
Key Pillars of a Data Privacy Culture
Building a strong data privacy culture requires a multi-faceted approach. Here are some key pillars to consider:
- Leadership Buy-in: Data privacy starts at the top. Leaders must champion a data-centric mindset and set the tone for the organization. They need to demonstrate commitment to data privacy and invest in the necessary resources.
- Employee Education and Training: A well-informed workforce is crucial. Employees should understand their responsibilities regarding data privacy, the relevant regulations, and the potential consequences of data breaches. Regular training sessions and workshops are essential to keep everyone on the same page.
- Clear Data Privacy Policies and Procedures: Organizations should have comprehensive data privacy policies that outline their approach to data collection, use, storage, and sharing. These policies must be easily accessible and understood by all employees.
- Data Minimization: Only collect and store the data that’s necessary for the intended purpose. This principle reduces the risk of data breaches and ensures that sensitive information is not unnecessarily exposed.
- Data Security Measures: Implement robust technical controls to protect data from unauthorized access, use, disclosure, alteration, or destruction. This includes firewalls, encryption, access controls, and regular security audits.
- Data Subject Rights: Organizations must empower individuals to exercise their rights to access, rectify, erase, restrict, or object to the processing of their data. This includes establishing clear procedures for handling data subject requests.
- Transparency and Accountability: Be transparent with individuals about how their data is being used and collected. Provide clear and concise privacy notices and ensure accountability for data privacy practices. This includes a designated data protection officer (DPO) to oversee data privacy compliance.
- Continuous Improvement: Data privacy is an ongoing process. Regularly review and update data privacy policies and practices to keep pace with evolving technologies and regulations. Foster a culture of continuous learning and improvement.
Benefits of a Data Privacy Culture
Building a data privacy culture offers numerous benefits:
- Enhanced Brand Reputation: Consumers are increasingly aware of data privacy and are more likely to trust companies that demonstrate strong data privacy practices. This can lead to increased customer loyalty and brand advocacy.
- Reduced Legal and Regulatory Risks: Compliance with data privacy regulations is crucial to avoid hefty fines and penalties. A strong data privacy culture minimizes the risk of data breaches and ensures regulatory compliance.
- Improved Operational Efficiency: Data privacy practices can lead to streamlined processes and reduced operational costs. For example, data minimization can simplify data management and reduce the risk of data breaches.
- Increased Innovation: When organizations build trust with their customers through responsible data handling, they can leverage data for innovation and development of new products and services.
Conclusion
In today’s data-driven world, building a culture of data privacy is no longer a choice; it’s a necessity. By embedding data privacy principles into every aspect of the organization, businesses can gain a competitive advantage, enhance customer trust, and navigate the ever-changing regulatory landscape. Building a data privacy culture is an investment in the long-term success of the organization.
The Future of Data Privacy: Trends and Predictions

The digital landscape is evolving at an unprecedented pace, and with it, the importance of data privacy is rising to the forefront. As we generate more data than ever before, concerns about how this information is collected, used, and protected are becoming increasingly prominent. In this article, we will delve into the future of data privacy, exploring key trends, emerging technologies, and predictions that will shape the landscape in the years to come.
The Rise of Data Minimalism
Data minimalism, a philosophy advocating for the collection and processing of only the absolutely essential data, is gaining traction. Consumers are becoming more aware of the value of their data and demanding greater control over how it is used. Organizations will need to adopt data-minimization practices to gain and maintain consumer trust.
The Power of Decentralized Technologies
Decentralized technologies, such as blockchain and distributed ledgers, are poised to play a transformative role in data privacy. These technologies offer a secure and transparent way to store and manage data, empowering individuals with greater control over their information. Blockchain, in particular, can enable secure and transparent data sharing, reducing the risks of data breaches and unauthorized access.
The Emergence of Privacy-Enhancing Technologies (PETs)
Privacy-enhancing technologies (PETs) are emerging as powerful tools for safeguarding data privacy. These technologies, such as differential privacy and homomorphic encryption, allow data to be analyzed without revealing sensitive information. PETs will be crucial for enabling data-driven insights while ensuring the privacy of individuals.
The Growing Importance of Data Governance
Effective data governance will be paramount for navigating the complexities of data privacy. Organizations will need to establish clear policies and procedures for data collection, use, and sharing, ensuring compliance with evolving regulations. This includes implementing data retention policies, conducting regular audits, and building robust data security measures.
The Impact of Artificial Intelligence (AI)
AI is rapidly transforming industries, and its impact on data privacy is significant. AI algorithms can be trained on massive datasets, raising concerns about potential biases and discrimination. Organizations must develop ethical AI frameworks that prioritize data privacy and mitigate potential risks.
Predictions for the Future
The future of data privacy will be characterized by:
- Increased regulation: Governments around the world are strengthening data privacy laws, such as the GDPR and CCPA, driving organizations to comply with stringent regulations.
- Empowered consumers: Consumers will demand more transparency and control over their data, leading to the adoption of data privacy-focused technologies and practices.
- Greater data security: Organizations will invest in advanced security measures to protect sensitive data from cyber threats and data breaches.
- The rise of data trusts: Data trusts will emerge as mechanisms for managing and sharing data ethically, fostering collaboration while ensuring privacy.
Conclusion
The future of data privacy is a complex and evolving landscape. As technology continues to advance, organizations must prioritize data privacy by embracing data minimalism, leveraging decentralized technologies, adopting PETs, and implementing robust data governance practices. By doing so, they can build trust with consumers, comply with regulations, and foster a future where data is used responsibly and ethically.

