In today’s digital landscape, small businesses face a growing threat from cyberattacks. Data breaches, ransomware, and other cyber threats can be devastating, costing businesses money, time, and reputation. Cybersecurity is no longer a luxury; it’s a necessity for all businesses, regardless of size. That’s why it’s crucial to invest in the right cybersecurity tools to safeguard your digital assets.
This article will explore essential cybersecurity tools that can help small businesses protect themselves from cyber threats. We’ll cover everything from antivirus software and firewalls to data backup and employee training. Whether you’re a startup or a well-established company, this guide will provide valuable insights into building a robust cybersecurity strategy that can help you stay ahead of the curve and keep your business safe.
The Growing Need for Cybersecurity for Small Businesses
In today’s digital age, cybersecurity is no longer a concern only for large corporations. Small businesses are increasingly becoming targets of cyberattacks, making it crucial for them to prioritize their online security. With the increasing reliance on technology for operations, data storage, and customer interactions, small businesses are exposed to a multitude of cyber threats.
One of the primary reasons for the growing need for cybersecurity for small businesses is the increasing sophistication of cyberattacks. Hackers are constantly developing new techniques to exploit vulnerabilities and gain access to sensitive information. From phishing scams to ransomware attacks, small businesses are vulnerable to a wide range of cyber threats that can cause significant financial and reputational damage.
Another factor driving the need for cybersecurity is the rise of remote work and cloud computing. As more businesses embrace remote work and store their data in the cloud, they are expanding their attack surface and making themselves more susceptible to cyber threats. The decentralized nature of remote work makes it challenging to secure all devices and data, requiring comprehensive cybersecurity measures.
The consequences of a cyberattack can be devastating for small businesses. Data breaches can lead to financial losses, legal liabilities, and reputational damage. Ransomware attacks can cripple operations and disrupt critical business processes. In addition, cyberattacks can compromise customer trust and erode brand reputation, making it difficult to attract new customers and retain existing ones.
To mitigate these risks, small businesses need to implement robust cybersecurity measures. This includes:
- Strong passwords and multi-factor authentication to prevent unauthorized access
- Regular software updates to patch security vulnerabilities
- Employee cybersecurity training to raise awareness and reduce human error
- Firewalls and intrusion detection systems to prevent malicious activity
- Data backup and recovery plans to protect against data loss
- Incident response plans to handle cyberattacks effectively
Investing in cybersecurity is not an optional expense for small businesses. It’s an essential investment to protect their assets, reputation, and future success. By taking proactive measures to strengthen their online security, small businesses can mitigate their risk and thrive in the digital age.
Cybersecurity Threats Facing Small Businesses
In today’s digital age, small businesses are increasingly vulnerable to cyberattacks. While large corporations often have dedicated cybersecurity teams and robust security measures, small businesses may lack the resources and expertise to protect themselves adequately. This leaves them susceptible to a wide range of threats, which can have devastating consequences.
One of the most common threats facing small businesses is phishing. Phishing attacks involve sending emails or messages that appear to be from legitimate sources, but are actually designed to trick users into revealing sensitive information, such as login credentials or credit card details. Small businesses are often targeted because they may have less sophisticated email filters and security awareness training.
Another major threat is malware, which can include viruses, worms, and ransomware. Malware can be spread through various means, such as email attachments, infected websites, or malicious downloads. Once installed, malware can steal data, disrupt business operations, or even hold sensitive information hostage for ransom.
Data breaches are a serious concern for all businesses, but especially for small businesses that store sensitive customer information. Breaches can occur through various methods, such as hacking, phishing, or employee negligence. The consequences of a data breach can be severe, including financial losses, reputational damage, and legal repercussions.
Denial-of-service (DoS) attacks can also pose a significant threat to small businesses. DoS attacks attempt to overwhelm a website or network with traffic, making it unavailable to legitimate users. These attacks can disrupt business operations and lead to lost revenue.
In addition to the threats mentioned above, small businesses must also be aware of emerging threats such as cryptojacking, where hackers use a business’s computer resources to mine cryptocurrency without their knowledge or consent. The rise of the Internet of Things (IoT) also presents new cybersecurity challenges, as devices connected to the internet can become entry points for attackers.
To mitigate cybersecurity risks, small businesses should implement a comprehensive approach that includes the following:
- Strong passwords and multi-factor authentication: Use strong passwords for all accounts and enable multi-factor authentication whenever possible.
- Regular software updates: Keep all software and operating systems up-to-date to patch security vulnerabilities.
- Security awareness training for employees: Educate employees about common cyber threats and best practices for protecting sensitive information.
- Data backups: Regularly back up important data to ensure that it can be restored in the event of a cyberattack.
- Firewall protection: Use a strong firewall to block unauthorized access to the business network.
- Antivirus software: Install and maintain antivirus software to protect against malware threats.
- Incident response plan: Develop a plan for responding to a cyberattack, including steps for containing the damage and recovering lost data.
By taking these steps, small businesses can significantly reduce their risk of falling victim to cyberattacks. It’s essential to remember that cybersecurity is an ongoing process, and businesses must be vigilant in protecting their sensitive data and systems.
Data Breaches and Financial Losses
Data breaches are a growing problem for businesses and individuals alike. In recent years, there have been a number of high-profile data breaches that have resulted in the theft of millions of sensitive data. These breaches can have a devastating impact on businesses, costing them millions of dollars in lost revenue, legal fees, and reputational damage.
One of the most common ways that data breaches occur is through phishing attacks. Phishing attacks are emails or websites that are designed to trick users into revealing their personal information, such as their username, password, or credit card number. Once a hacker has obtained this information, they can use it to gain access to the victim’s accounts and steal their money.
Another common way that data breaches occur is through malware. Malware is software that is designed to damage or disable a computer system. Once malware has infected a computer, it can be used to steal data, monitor the user’s activities, or launch other attacks.
The financial losses associated with data breaches can be significant. In addition to the direct costs of lost revenue and legal fees, businesses can also suffer reputational damage that can take years to recover from. Customers may be reluctant to do business with a company that has been the victim of a data breach, and the company’s stock price may decline.
There are a number of steps that businesses can take to protect themselves from data breaches. These include:
- Implementing strong passwords and multi-factor authentication
- Educating employees about phishing attacks and malware
- Using firewalls and antivirus software
- Encrypting sensitive data
- Having a comprehensive data breach response plan
By taking these steps, businesses can significantly reduce their risk of being the victim of a data breach.
Malware and Ransomware Attacks
Malware and ransomware attacks are becoming increasingly common, with attackers constantly finding new ways to exploit vulnerabilities in systems and networks. These attacks can have devastating consequences for individuals and businesses, resulting in financial losses, data breaches, and reputational damage.
Malware is any software designed to damage or disable a computer system. It can take many forms, including viruses, worms, Trojans, and spyware. Malware can spread through various means, such as email attachments, malicious websites, and infected software. Once installed, it can steal sensitive data, disrupt system operations, and even render a computer unusable.
Ransomware is a type of malware that encrypts a victim’s files, making them inaccessible. The attackers then demand a ransom payment, usually in cryptocurrency, to decrypt the files. Ransomware attacks can cripple businesses, forcing them to shut down operations or pay the ransom to regain access to their data.
How to Protect Yourself from Malware and Ransomware Attacks
There are several steps you can take to protect yourself from malware and ransomware attacks:
- Keep your software updated: Regularly install security updates and patches for your operating system, applications, and antivirus software. These updates often include fixes for vulnerabilities that attackers could exploit.
- Use a strong antivirus program: Install a reputable antivirus program and keep it updated. This will help detect and remove malware before it can cause damage.
- Be cautious about email attachments and links: Don’t open email attachments or click on links from unknown senders. Be wary of emails that seem suspicious or urgent. If you’re unsure, contact the sender to verify the authenticity of the email.
- Back up your data regularly: Regularly back up your important files to an external hard drive or cloud storage service. This will help you recover your data if it is encrypted by ransomware.
- Be aware of phishing attacks: Phishing attacks are designed to trick you into revealing sensitive information, such as passwords or credit card numbers. Be careful about websites and emails that ask for personal information.
By following these tips, you can significantly reduce your risk of falling victim to malware and ransomware attacks.
Phishing Scams and Social Engineering
In today’s digital age, where information is readily available and transactions are conducted online, it’s crucial to be aware of the various threats that lurk in cyberspace. One of the most prevalent and sophisticated threats is phishing, a type of social engineering attack aimed at stealing sensitive information such as usernames, passwords, credit card details, and bank account numbers.
Phishing attacks typically involve fraudulent emails, text messages, or websites designed to mimic legitimate sources. These deceptive messages often urge recipients to click on malicious links or download attachments that contain malware. Once clicked, the malware can install itself on the victim’s device, granting attackers access to their data and potentially compromising their entire system.
Social engineering is a manipulative technique used by attackers to trick individuals into divulging confidential information or granting unauthorized access to systems. Phishing is a prime example of social engineering, as it exploits human psychology and trust to gain access to sensitive data.
Here are some common tactics used in phishing attacks:
- Spoofing: Attackers create fake websites or emails that look identical to legitimate ones, such as banks, online retailers, or social media platforms.
- Urgency and Scarcity: Phishing emails often create a sense of urgency or scarcity, urging recipients to act quickly before they miss out on an opportunity or face a negative consequence.
- Personalization: Attackers may personalize their emails or messages by using the recipient’s name or other personal information obtained from data breaches or social media profiles.
- Baiting: Phishing attacks may offer tempting rewards or prizes to entice victims into clicking on malicious links or downloading attachments.
To protect yourself from phishing scams and social engineering attacks, it’s important to be vigilant and practice good online security habits:
- Be cautious of suspicious emails, texts, and websites. Hover over links before clicking on them to check their destination URL.
- Never click on links or download attachments from unknown senders.
- Verify the authenticity of websites before entering personal information. Look for HTTPS in the website address and check for trust seals from reputable organizations.
- Use strong passwords and enable two-factor authentication wherever possible.
- Keep your software up to date to patch security vulnerabilities.
- Be skeptical of offers that seem too good to be true.
- Report phishing attempts to the appropriate authorities or your service providers.
By staying informed, practicing caution, and implementing sound security measures, you can significantly reduce your risk of becoming a victim of phishing scams and social engineering attacks.
Essential Cybersecurity Tools for Small Businesses
In today’s digital landscape, cybersecurity is no longer an option but a necessity for businesses of all sizes. Small businesses, in particular, are vulnerable to cyberattacks due to limited resources and a lack of dedicated IT staff. However, there are a range of affordable and user-friendly cybersecurity tools available that can help small businesses protect their data and systems.
1. Anti-Virus Software
Anti-virus software is the foundation of any comprehensive cybersecurity strategy. It protects your devices from malware, viruses, and other threats that can steal your data, disrupt your operations, or even shut down your business. There are many excellent anti-virus solutions available, both free and paid, from reputable vendors such as Norton, McAfee, and Bitdefender.
2. Firewall
A firewall acts as a barrier between your network and the outside world, blocking unauthorized access to your systems. Firewalls can be hardware-based or software-based, and they are essential for preventing hackers from infiltrating your network. Most routers come with built-in firewalls, but you can also install additional software firewalls for an extra layer of protection.
3. Data Backup and Recovery
Data backups are crucial for protecting your business from data loss due to cyberattacks, hardware failures, or natural disasters. Regularly backing up your data to an off-site location ensures that you can restore your systems and files in the event of a catastrophic event. There are many cloud-based backup services available that are affordable and easy to use.
4. Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security to your accounts by requiring you to enter a code from your phone or email in addition to your password. This makes it much harder for hackers to gain access to your sensitive information, even if they steal your password. 2FA is now available for many online services and apps.
5. Employee Training
Human error is a major cause of security breaches, so it’s essential to train your employees on basic cybersecurity best practices. This includes topics such as strong password creation, phishing prevention, and safe browsing habits. Regular training sessions will help your employees stay vigilant and prevent them from accidentally compromising your security.
6. Security Monitoring and Incident Response
Security monitoring tools can help you detect suspicious activity on your network and systems, allowing you to respond quickly to potential threats. These tools can monitor for malware, intrusions, and other anomalies. Incident response plans outline the steps you need to take in the event of a security breach, ensuring that you can minimize damage and restore operations quickly.
Conclusion
Investing in cybersecurity tools is an essential part of protecting your small business from the ever-growing threat of cyberattacks. By implementing these measures, you can minimize your risk of data loss, financial losses, and reputational damage. Remember that cybersecurity is an ongoing process, and you should continuously review and update your security measures to stay ahead of evolving threats.
Firewall Protection: Your First Line of Defense
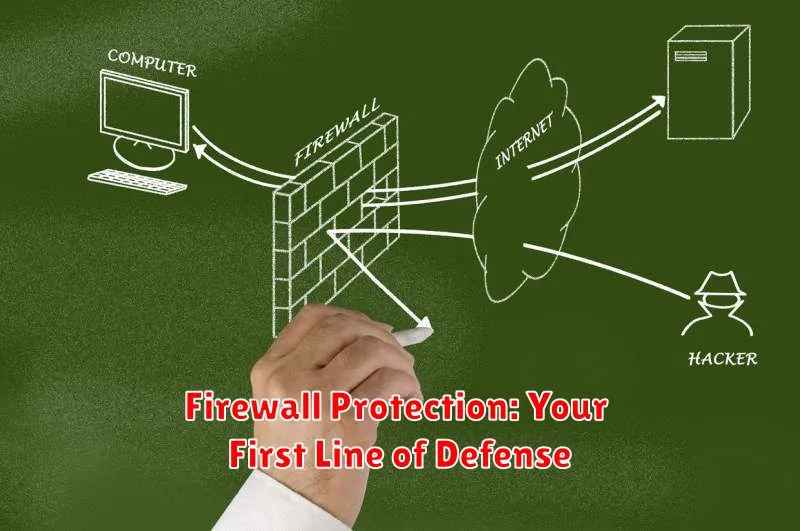
In today’s digital age, where cyber threats are becoming increasingly sophisticated, securing your data and devices is paramount. A firewall acts as a crucial line of defense, preventing unauthorized access to your network and protecting your valuable information from malicious attacks. Let’s delve into the world of firewalls and understand their significance in safeguarding your online presence.
Imagine a firewall as a digital gatekeeper. It meticulously examines incoming and outgoing network traffic, allowing only authorized connections while blocking any suspicious activity. This security measure operates on a set of rules, diligently scrutinizing every communication attempt, ensuring that only trusted sources are granted access to your network.
Types of Firewalls: A Diverse Arsenal
Firewalls come in various forms, each with its unique set of capabilities. Here are some common types:
- Hardware Firewalls: These physical devices are typically installed at the edge of your network, effectively acting as a barrier between your internal systems and the external world. They are known for their high performance and robust security features.
- Software Firewalls: These virtual firewalls are installed on individual computers or servers, providing an extra layer of protection. They are often pre-installed in operating systems or can be downloaded as separate applications.
- Cloud-Based Firewalls: As the name suggests, these firewalls reside in the cloud, providing security for your online resources and applications. They are highly scalable and offer flexible deployment options.
Benefits of Firewall Protection: A Comprehensive Shield
Employing a firewall offers numerous benefits, including:
- Prevents Unauthorized Access: Firewalls act as vigilant gatekeepers, blocking any attempts to access your network without proper authorization, preventing unauthorized users from gaining access to your sensitive data.
- Protects Against Malware: Firewalls can identify and block malicious software, such as viruses, worms, and Trojan horses, from entering your network, safeguarding your systems from infections.
- Enhances Network Security: By filtering network traffic and enforcing security policies, firewalls create a secure and controlled environment for your network, reducing the risk of breaches and attacks.
- Provides Network Visibility: Firewalls offer valuable insights into network activity, providing detailed logs of traffic patterns, potential threats, and security events, allowing you to monitor and analyze your network behavior effectively.
Choosing the Right Firewall: A Strategic Decision
Selecting the right firewall for your specific needs is crucial. Consider factors like:
- Network Size: Choose a firewall that can handle the volume of traffic in your network. Smaller networks may require less powerful firewalls, while larger networks may demand more robust solutions.
- Security Requirements: Evaluate the level of security you require based on your industry, data sensitivity, and potential threats. Some firewalls offer more advanced features, like intrusion detection and prevention systems.
- Budget: Firewalls vary in cost, so consider your budget constraints and choose a solution that fits your financial resources.
- Ease of Management: Look for a firewall that is easy to configure, manage, and maintain, reducing administrative overhead and ensuring efficient operation.
In conclusion, firewalls are an indispensable component of any comprehensive cybersecurity strategy. They provide a robust first line of defense, protecting your network and data from malicious attacks. By understanding the different types, benefits, and considerations involved in choosing a firewall, you can make informed decisions to ensure the security of your online presence.
Antivirus and Anti-Malware Software: Keeping Threats at Bay

In today’s digital age, where our lives are increasingly intertwined with technology, it’s more important than ever to protect our devices from malicious threats. Antivirus and anti-malware software are essential tools for safeguarding our computers, smartphones, and other connected devices from viruses, malware, and other cyberattacks.
What is Antivirus Software?
Antivirus software is designed to detect and remove viruses from computer systems. Viruses are malicious programs that can replicate themselves and spread to other devices. They can cause various problems, including data loss, system crashes, and security breaches.
What is Anti-Malware Software?
Anti-malware software is a broader category of software that protects against a wider range of threats, including malware, spyware, ransomware, and adware. Malware is a generic term for any software designed to harm or disrupt computer systems.
How Do Antivirus and Anti-Malware Programs Work?
Antivirus and anti-malware programs work by using various techniques, including:
- Signature-based detection: These programs maintain a database of known malware signatures and scan files for matches.
- Heuristic analysis: This method analyzes the behavior of programs and identifies suspicious activities that might indicate malware.
- Cloud-based scanning: Some programs use cloud services to scan files and identify threats more quickly and effectively.
- Real-time protection: This feature monitors your computer’s activity and blocks suspicious files or websites from accessing your system.
Why Is It Important to Use Antivirus and Anti-Malware Software?
There are many reasons why it’s crucial to use antivirus and anti-malware software:
- Protection against viruses and malware: These programs are the first line of defense against malicious software that can damage your computer or steal your data.
- Prevention of data loss: Viruses and malware can encrypt or delete your files, leading to significant data loss.
- Protection against ransomware: Ransomware is a type of malware that locks your files and demands payment for their release. Antivirus software can help prevent ransomware infections.
- Enhanced online security: Antivirus and anti-malware programs can protect your computer from online threats, such as phishing scams and malicious websites.
- Peace of mind: Knowing that your computer is protected from threats can give you peace of mind while you browse the internet, work, or play games.
Choosing the Right Antivirus and Anti-Malware Software
With so many antivirus and anti-malware programs available, it can be challenging to choose the right one. Here are some factors to consider:
- Features: Look for a program that offers comprehensive protection against all types of threats, including viruses, malware, ransomware, and phishing attacks.
- Performance: The program should not significantly impact your computer’s performance. Look for programs with lightweight features and efficient scanning capabilities.
- Ease of use: The software should be easy to install, configure, and use. It should have a user-friendly interface.
- Customer support: Choose a program that offers reliable customer support in case you need assistance.
- Price: Antivirus and anti-malware software comes in various price ranges. Choose a program that fits your budget and offers the features you need.
Best Practices for Protecting Your Devices
In addition to using antivirus and anti-malware software, here are some best practices for protecting your devices from threats:
- Keep your software updated: Regularly update your operating system, antivirus software, and other programs to patch security vulnerabilities.
- Be cautious with email attachments and links: Avoid opening email attachments or clicking on links from unknown senders. Be wary of suspicious emails, even if they appear to be from a legitimate source.
- Use strong passwords: Create strong passwords that are difficult to guess and use a different password for each online account.
- Enable two-factor authentication: Two-factor authentication adds an extra layer of security by requiring you to enter a code from your phone in addition to your password.
- Be careful about what you download: Only download software from trusted sources, such as the official website of the developer. Avoid downloading software from suspicious websites or file-sharing networks.
- Use a firewall: A firewall can help prevent unauthorized access to your computer from the internet.
- Be aware of phishing scams: Phishing scams are designed to trick you into giving up your personal information. Be cautious about clicking on links or providing information on websites that look suspicious.
Conclusion
Antivirus and anti-malware software are essential tools for protecting your devices from threats. By using these programs and following best practices, you can significantly reduce your risk of cyberattacks and keep your data safe.
Password Managers: Simplifying Secure Access

In today’s digital world, we are bombarded with numerous accounts and logins. From banking to social media, our online lives are intertwined with a multitude of platforms, each demanding a unique password. Managing all these passwords can be a daunting task, leading to security risks and frustration. This is where password managers come to the rescue.
Password managers are software applications designed to store and manage your passwords securely. They provide a central repository for all your login credentials, eliminating the need to remember countless complex passwords. Instead, you only need to remember a single, strong master password to access your entire password vault.
Benefits of Using a Password Manager
There are several compelling reasons to consider using a password manager:
- Enhanced Security: Password managers use strong encryption algorithms to safeguard your passwords, preventing unauthorized access. They also generate and store complex passwords that are difficult to crack, significantly bolstering your online security.
- Convenience: By storing all your passwords in one central location, you can access them quickly and easily across multiple devices. This eliminates the need to constantly search for forgotten passwords or rely on weak and easily guessable ones.
- Improved Password Hygiene: Password managers encourage the use of unique and strong passwords for each account, reducing the risk of a security breach compromising multiple accounts.
- Automatic Password Updates: Some password managers offer features like automatic password updates. If a website suffers a data breach and requires you to change your password, the manager can automatically update it across all your accounts, ensuring seamless security.
Choosing the Right Password Manager
With numerous password managers available, selecting the right one can be overwhelming. Consider factors such as:
- Platform Compatibility: Choose a password manager that supports your preferred operating systems and devices.
- Security Features: Look for features such as two-factor authentication, password strength indicators, and automatic password updates.
- Ease of Use: The interface should be user-friendly and intuitive, making it easy to store, access, and manage your passwords.
- Pricing: Password managers can be free or paid. Consider your needs and budget when making your decision.
Conclusion
In today’s increasingly digital world, password managers have become an essential tool for protecting your online security and simplifying access to your accounts. By choosing a reputable password manager, you can safeguard your credentials, enhance your online security posture, and enjoy the convenience of seamless logins.
Two-Factor Authentication: Adding an Extra Layer of Security

In today’s digital age, where our personal and sensitive information is constantly under threat, it’s more important than ever to take precautions to safeguard our online accounts. One of the most effective ways to bolster security is by implementing two-factor authentication (2FA). This additional layer of protection adds an extra step to the login process, making it significantly harder for unauthorized individuals to access our accounts.
2FA works by requiring users to provide two distinct forms of authentication before granting access. The first factor is typically something you know, such as a password or PIN. The second factor, which serves as the extra layer of security, is something you have, such as a physical token or a code sent to your phone.
Types of Two-Factor Authentication
There are various methods of 2FA available, each with its own strengths and weaknesses. Some common types include:
- SMS or Email Codes: A one-time code is sent to the user’s phone or email address. This method is relatively simple but can be vulnerable to SIM swapping attacks.
- Authenticator Apps: These apps generate time-based codes that change every 30 seconds. They provide a more secure alternative to SMS or email codes, as they’re not susceptible to SIM swapping.
- Hardware Tokens: Physical tokens, such as USB keys or key fobs, generate unique codes that need to be entered alongside the password. These tokens offer the highest level of security but can be inconvenient to carry around.
- Biometric Authentication: This method uses unique biological traits, such as fingerprints or facial recognition, to verify the user’s identity. Biometric authentication is convenient but can be compromised if the biometric data is stolen.
Benefits of Two-Factor Authentication
Implementing 2FA offers numerous benefits for both individuals and organizations:
- Enhanced Security: 2FA significantly reduces the risk of unauthorized access to accounts, as it makes it much harder for hackers to gain entry even if they know the password.
- Protection Against Phishing Attacks: Phishing attacks rely on tricking users into providing their login credentials. 2FA helps prevent these attacks by requiring an additional authentication factor that phishers cannot obtain.
- Improved Compliance: Many industries have regulations that require the use of multi-factor authentication to protect sensitive information. 2FA helps organizations comply with these regulations.
- Peace of Mind: Knowing that your accounts are protected with an extra layer of security can give you peace of mind and allow you to browse the internet with greater confidence.
Conclusion
Two-factor authentication is a critical security measure that everyone should consider implementing. By adding this extra layer of protection, we can significantly reduce the risk of our accounts being compromised. Whether you’re an individual or an organization, adopting 2FA is a wise step towards securing your digital life.
Virtual Private Network (VPN): Secure Remote Access

A Virtual Private Network (VPN) is a technology that creates a secure and encrypted connection over a public network, such as the internet. This allows users to access private networks remotely and securely, as if they were directly connected to the network. VPNs are widely used for various purposes, including:
Privacy and Security
VPNs encrypt data transmitted between your device and the VPN server, making it difficult for third parties to intercept or monitor your online activity. This is especially important when using public Wi-Fi networks, which are notoriously vulnerable to security breaches.
Bypass Geo-restrictions
Many websites and streaming services restrict access based on geographical location. A VPN can help you bypass these restrictions by connecting you to a server in a different country, allowing you to access content that would otherwise be unavailable.
Anonymity
VPNs can mask your IP address, making it difficult to track your online activity. This can provide a degree of anonymity, especially when browsing websites or downloading files anonymously.
Remote Access to Private Networks
VPNs are commonly used for businesses to provide secure remote access to their internal networks. This allows employees to access company resources from anywhere in the world, while maintaining data security.
How VPNs Work
When you connect to a VPN, your device establishes a secure tunnel to a VPN server. All your internet traffic is then routed through this tunnel, encrypted and decrypted by the VPN server. This means that even if someone intercepts your data, they won’t be able to decipher it without the VPN server’s decryption key.
Choosing a VPN
When choosing a VPN, consider factors like:
- Security features: Look for strong encryption protocols, such as AES-256.
- Privacy policy: Choose a VPN with a no-logs policy, meaning they don’t store your browsing history or activity.
- Server locations: Select a VPN with servers in the locations you need to access.
- Speed: Choose a VPN with fast servers, especially if you plan to stream content.
- Price: VPN services come at various price points. Choose one that fits your budget and needs.
Conclusion
VPNs are an essential tool for protecting your online privacy and security. Whether you’re using public Wi-Fi, accessing geographically restricted content, or simply want to browse the internet anonymously, a VPN can provide the necessary protection.
Data Backup and Recovery Solutions: Protecting Against Data Loss

In today’s digital age, data is the lifeblood of businesses and individuals alike. From financial records to personal photos, the information we store on our devices is invaluable. However, the risk of data loss is ever-present, due to factors such as hardware failures, natural disasters, malware attacks, and human error. That’s where data backup and recovery solutions come in, providing a crucial safety net to protect your vital data.
The Importance of Data Backup
Data backup is the process of creating copies of your data and storing them in a separate location. This ensures that you have a readily available backup in case the original data is lost or corrupted. Regular data backup is essential for several reasons:
- Data Recovery: In case of data loss, you can restore your data from the backup, minimizing downtime and potential financial losses.
- Disaster Recovery: Data backups can help you recover from natural disasters, such as fires or floods, that could destroy your original data.
- Versioning: Data backups often include versioning, allowing you to revert to previous versions of files in case of accidental edits or corruption.
- Compliance: Some industries have regulations that require data backups for compliance purposes.
Types of Data Backup Solutions
There are various data backup solutions available, each with its own advantages and disadvantages. Some of the most common options include:
- Local Backups: Data is stored on a local storage device, such as an external hard drive or USB drive. This is a simple and affordable option, but it’s vulnerable to physical damage or theft.
- Cloud Backups: Data is stored on remote servers in the cloud. This provides high availability and scalability, but it requires a reliable internet connection and may incur monthly fees.
- Hybrid Backups: A combination of local and cloud backups, offering a balance of security, affordability, and flexibility.
Data Recovery Services
Even with regular data backups, data loss can still occur. In such cases, data recovery services can help retrieve lost or corrupted data from damaged devices or storage media. These services employ specialized techniques and tools to recover data, but the success rate can vary depending on the severity of the damage.
Choosing the Right Solution
Selecting the appropriate data backup and recovery solution depends on various factors, including:
- Data Sensitivity: The importance and confidentiality of your data.
- Data Volume: The amount of data you need to back up.
- Budget: The cost of the backup solution and potential recovery services.
- Security Needs: The level of security required to protect your data.
Conclusion
Data backup and recovery solutions are crucial for protecting your valuable information from loss. By implementing a comprehensive backup strategy and choosing the right solutions, you can minimize the risk of data loss and ensure business continuity. Remember that data protection is an ongoing process, requiring regular review and updates to keep pace with evolving threats and technology.
Email Security Solutions: Preventing Phishing Attacks

In today’s digital age, email has become an integral part of our personal and professional lives. However, with the rise of cybercrime, email security has become a crucial concern. One of the most prevalent threats is phishing, a deceptive tactic used by cybercriminals to trick users into revealing sensitive information such as passwords, credit card details, or bank account information.
Phishing attacks typically involve sending emails that appear to be from legitimate sources, such as banks, online retailers, or government agencies. These emails often contain malicious links or attachments that, when clicked or opened, can install malware on the victim’s device or redirect them to fake websites designed to steal their credentials. To combat this growing threat, robust email security solutions are essential.
Email Security Solutions for Preventing Phishing Attacks
There are various email security solutions available to protect against phishing attacks. Some of the most effective ones include:
- Email Filtering: Email filtering solutions analyze incoming emails for suspicious content, such as spam, malware, and phishing attempts. They use various techniques like blacklists, whitelists, and content analysis to identify and block malicious emails before they reach users’ inboxes.
- Anti-Phishing Training: Educating users about phishing attacks is crucial. Training programs teach employees how to identify phishing emails, recognize suspicious links and attachments, and report suspicious activities. Regular phishing simulations can help reinforce these skills.
- Domain-Based Message Authentication, Reporting & Conformance (DMARC): DMARC is an email authentication protocol that helps organizations prevent email spoofing and phishing attacks. It allows organizations to specify authorized senders for their domains, ensuring that emails coming from their domains are legitimate.
- Two-Factor Authentication (2FA): 2FA adds an extra layer of security by requiring users to provide two separate forms of authentication, such as a password and a code sent to their phone. This makes it much harder for phishers to access accounts even if they have stolen a password.
- Secure Email Gateways: Secure email gateways act as a firewall for email traffic, scanning emails for malware, phishing attempts, and other threats. They can block malicious emails and prevent them from reaching users’ inboxes.
Implementing Email Security Solutions
Implementing comprehensive email security solutions requires a multi-pronged approach. It involves:
- Choosing the Right Solutions: Select email security solutions that meet your organization’s specific needs and security requirements.
- Regular Updates and Maintenance: Keep your email security solutions up to date with the latest patches and updates to stay ahead of evolving phishing threats.
- User Training and Awareness: Train employees on phishing prevention techniques and encourage them to report suspicious emails.
- Continuous Monitoring and Analysis: Regularly monitor your email security logs and analyze phishing attempts to identify trends and adapt your security measures accordingly.
By implementing robust email security solutions and fostering a culture of security awareness, organizations can significantly reduce their risk of falling victim to phishing attacks. This proactive approach can protect sensitive data, maintain user trust, and ensure business continuity.
Employee Training and Awareness: Building a Human Firewall

In today’s digital landscape, cybersecurity threats are becoming increasingly sophisticated and relentless. Organizations face an uphill battle against malicious actors seeking to exploit vulnerabilities and compromise sensitive data. While technical security measures are crucial, a strong human firewall is equally essential for protecting an organization’s assets.
Employee training and awareness play a pivotal role in building this human firewall. By equipping employees with the knowledge and skills to identify and respond to security threats, organizations can significantly reduce their risk profile. This training empowers employees to become active participants in the security landscape, serving as the first line of defense against cyberattacks.
The Importance of Employee Training
Effective employee training covers a wide range of topics, including:
- Phishing and social engineering: Understanding how attackers manipulate individuals to gain access to sensitive information.
- Password security: Creating strong passwords and using multi-factor authentication.
- Data security: Recognizing and handling sensitive information appropriately.
- Malware and virus detection: Identifying and responding to malicious software.
- Reporting security incidents: Knowing how to communicate suspicious activities to the appropriate personnel.
Training programs should be tailored to the specific needs of each role and department, ensuring that employees receive the information relevant to their daily responsibilities. Interactive training methods, such as simulations and scenarios, enhance engagement and retention.
Creating a Culture of Security
Employee training is not a one-time event. It should be an ongoing process that reinforces security awareness and encourages employees to adopt best practices. Organizations should cultivate a culture of security where employees feel comfortable reporting suspicious activities and seeking help when they encounter unfamiliar situations.
Regular security updates, newsletters, and communication campaigns can keep employees informed about the latest threats and security protocols. Gamification and rewards can also incentivize employee participation and engagement.
Measuring Success
To assess the effectiveness of employee training programs, organizations should track key metrics such as:
- Number of security incidents reported: A decrease in incidents suggests that employees are becoming more vigilant.
- Employee satisfaction with training: Feedback from employees can identify areas for improvement.
- Time to respond to incidents: A faster response time indicates that employees are equipped with the necessary knowledge and skills.
Conclusion
Employee training and awareness are essential components of a comprehensive cybersecurity strategy. By empowering employees to become active participants in security, organizations can build a robust human firewall and minimize their risk of cyberattacks. Continuous training, a culture of security, and regular evaluation are key to ensuring the ongoing effectiveness of this crucial aspect of cybersecurity.

