In today’s digital world, safeguarding your online accounts is more crucial than ever. With cyberattacks on the rise, it’s essential to go beyond traditional passwords and implement robust security measures. Two-factor authentication (2FA) is a powerful tool that can significantly enhance your security posture, acting as an extra layer of protection against unauthorized access.
This comprehensive guide will provide you with a step-by-step walkthrough of implementing 2FA across your various online accounts. We’ll explore the different types of 2FA, their benefits, and how to enable them effectively. Whether you’re a tech-savvy individual or just starting to prioritize online security, this guide will empower you to take control and bolster your digital defenses.
Understanding Two-Factor Authentication: An Essential Security Layer

In today’s digital world, where online accounts hold sensitive personal and financial information, safeguarding your data is paramount. One of the most effective ways to enhance your security posture is by implementing two-factor authentication (2FA). This article aims to shed light on 2FA, explaining what it is, how it works, and why it’s essential for protecting your online accounts.
What is Two-Factor Authentication?
2FA is a security measure that adds an extra layer of protection to your accounts by requiring two distinct forms of verification before granting access. The first factor is typically your password, which is something you know. The second factor, however, is something you have, like your smartphone, or something you are, such as your fingerprint or facial recognition.
How Does 2FA Work?
When you attempt to log in to an account with 2FA enabled, you’ll first be prompted to enter your password as usual. After successfully entering your password, you’ll receive a second authentication request, usually in the form of a:
- One-Time Password (OTP) sent to your smartphone via SMS or a dedicated authentication app
- Push notification on your mobile device that requires your confirmation
- Biometric authentication using fingerprint or facial recognition
By successfully verifying both factors, you prove that you are the legitimate account owner and gain access.
Why is Two-Factor Authentication Important?
2FA significantly reduces the risk of unauthorized access to your accounts, even if your password is compromised. Here’s why:
- Enhanced Security: 2FA creates a significant hurdle for attackers, as they need to acquire both your password and your second factor to gain access.
- Protection Against Phishing Attacks: Even if you’re tricked into entering your password on a phishing website, the attacker won’t have access to your second factor.
- Peace of Mind: Knowing that your accounts are protected by an extra layer of security can provide peace of mind and reduce the worry of potential data breaches.
Enabling Two-Factor Authentication
Most online services, including email, social media, and financial institutions, offer 2FA as a security option. To enable 2FA, navigate to the security settings of your account and follow the instructions provided. You’ll usually be asked to choose a preferred 2FA method and verify your contact information.
Conclusion
Implementing two-factor authentication is a crucial step towards safeguarding your online accounts. By adding an extra layer of security, you significantly reduce the risk of unauthorized access and protect your sensitive information from falling into the wrong hands. Take the necessary steps to enable 2FA on all your critical accounts today and enjoy greater peace of mind in the digital world.
Different Methods of Two-Factor Authentication
Two-factor authentication (2FA) is a security measure that requires users to provide two different forms of identification before granting access to an account. This helps protect against unauthorized access, even if one of the factors is compromised. There are various methods of 2FA, each with its own advantages and disadvantages.
Common Methods of Two-Factor Authentication:
Here are some of the most common methods of 2FA:
1. SMS or Email Codes
This is the most common method of 2FA. When you log in, you receive a one-time code via SMS or email that you need to enter to verify your identity. It’s simple to set up but can be vulnerable to phishing attacks and SIM swapping.
2. Authentication Apps
Authentication apps like Google Authenticator or Authy generate time-based one-time passwords (TOTPs) that you can use to verify your identity. These apps are more secure than SMS or email codes because they are not susceptible to phishing attacks. However, you need to have the app installed on your device.
3. Hardware Tokens
Hardware tokens are physical devices that generate one-time passwords. They are generally more secure than software-based methods because they are not vulnerable to malware or phishing attacks. However, they can be lost or stolen, and they can be more expensive to purchase.
4. Biometrics
Biometric authentication methods like fingerprint scanning, facial recognition, and iris scanning can be used for 2FA. These methods are generally more secure than other methods because they are difficult to forge or steal. However, they can be expensive to implement and may raise privacy concerns.
5. Security Keys
Security keys are small, physical devices that plug into a computer’s USB port. They can be used to verify your identity without requiring a code. They are generally considered to be one of the most secure methods of 2FA. However, they can be lost or stolen, and they may not be compatible with all devices.
Choosing the Right Method for You
The best method of 2FA for you will depend on your specific needs and security requirements. Consider the following factors when choosing a method:
- Security: How secure do you need your account to be?
- Convenience: How easy do you want the process to be?
- Cost: How much are you willing to spend on 2FA?
It’s generally a good idea to use multiple methods of 2FA to further enhance your security. For example, you could use an authentication app and a security key. By using multiple methods, you make it much more difficult for attackers to gain access to your account.
Choosing the Right Two-Factor Authentication Solution

In today’s digital landscape, where cyber threats are rampant, securing your online accounts is paramount. Two-factor authentication (2FA) has emerged as a powerful tool to bolster account security by adding an extra layer of protection. However, with a plethora of 2FA solutions available, selecting the right one can be overwhelming. This guide will help you navigate the options and make an informed decision.
Understanding Two-Factor Authentication
2FA, also known as multi-factor authentication (MFA), requires you to provide two distinct forms of authentication to gain access to an account. The first factor is typically your password, while the second factor adds an extra layer of security. This second factor can be something you know, something you have, or something you are. Examples include:
- Something you know: A security code sent via SMS or email.
- Something you have: A physical security key or a smartphone with a dedicated app.
- Something you are: Biometric authentication such as fingerprint scanning or facial recognition.
Types of Two-Factor Authentication Solutions
Let’s delve into the most prevalent 2FA solutions and their strengths and weaknesses:
SMS-Based Authentication
SMS-based 2FA sends a time-sensitive code to your mobile phone. It’s widely available and convenient, but it’s susceptible to SIM swapping attacks, where a malicious actor can gain control of your phone number and intercept the code.
Email-Based Authentication
Similar to SMS, email-based 2FA sends a code to your email address. This method shares the vulnerability of SMS and may not be as secure. However, it’s convenient if you don’t have access to your phone.
Authenticator Apps
Authenticator apps like Google Authenticator or Authy generate time-based one-time passwords (TOTPs). These apps are generally more secure than SMS or email as they use a more robust cryptographic method. However, you need to have the app installed on your device, and losing your phone can render it unusable.
Hardware Security Keys
Hardware security keys are physical devices that plug into your computer’s USB port. They provide the highest level of security but require a physical device that you need to carry with you. Some popular options include YubiKey and Titan Security Key.
Biometric Authentication
Biometric authentication utilizes unique biological traits, such as fingerprints, facial recognition, or iris scanning, to verify your identity. It’s convenient and generally secure, but it can be susceptible to spoofing attacks.
Choosing the Right Solution
Selecting the best 2FA solution depends on your specific needs and risk tolerance. Here are some factors to consider:
- Security: Hardware security keys generally offer the highest security, followed by authenticator apps. SMS and email are the least secure options.
- Convenience: SMS and email are the most convenient, while hardware security keys require a physical device.
- Cost: Authenticator apps are free, while hardware security keys can be expensive.
- Compatibility: Ensure the chosen 2FA solution is compatible with the services you want to protect.
Conclusion
Implementing 2FA is crucial for enhancing your online security. Carefully evaluate different solutions based on security, convenience, cost, and compatibility. Choose a method that aligns with your needs and provides robust protection against unauthorized access. Remember, the stronger your defenses, the safer your digital life.
Step-by-Step Guide to Implementing Two-Factor Authentication

Two-factor authentication (2FA) is an essential security measure that adds an extra layer of protection to your online accounts. By requiring two forms of authentication, 2FA makes it significantly harder for unauthorized individuals to access your sensitive information. This guide will walk you through the process of implementing 2FA on various platforms, ensuring you can bolster your online security with ease.
Understanding Two-Factor Authentication
2FA works by requiring users to provide two distinct forms of authentication before granting access to an account. These forms usually include something you know (password) and something you have (authenticator app, physical token, or biometrics). This multi-layered approach significantly reduces the risk of unauthorized access, even if one factor is compromised.
How to Enable Two-Factor Authentication
The implementation of 2FA varies depending on the platform you are using. However, the general process involves the following steps:
1. Access Account Settings
Navigate to the security or settings section of the platform you want to secure. Look for options related to two-factor authentication, login verification, or multi-factor authentication.
2. Choose Your Authentication Method
Most platforms offer a selection of authentication methods, including:
- Authenticator Apps: These apps (such as Google Authenticator or Authy) generate time-based codes that change every 30 seconds.
- SMS or Email Codes: Receive a unique code via SMS or email that you need to enter during login.
- Security Keys: Physical devices that plug into your computer’s USB port and generate a unique code.
- Biometrics: Use fingerprint scanning, facial recognition, or iris scanning for authentication.
3. Set Up Your Chosen Method
Follow the platform’s instructions for setting up your chosen authentication method. This usually involves generating a QR code that you scan with your authenticator app, entering a code received via SMS or email, or registering a security key.
4. Verify Your Setup
After setting up your 2FA method, try logging in to your account. You will be prompted to enter the second factor (code from your authenticator app, SMS code, etc.).
Benefits of Using Two-Factor Authentication
Implementing 2FA offers several significant advantages, including:
- Enhanced Security: 2FA significantly reduces the risk of unauthorized access to your accounts, even if your password is compromised.
- Increased Protection Against Phishing Attacks: Phishing attacks often target passwords, but 2FA requires an additional factor, making them less effective.
- Improved Account Recovery: 2FA can help you recover your account more easily in case of forgotten passwords or device loss.
- Peace of Mind: Knowing that your accounts are protected by an extra layer of security can provide peace of mind.
Conclusion
Implementing two-factor authentication is a simple yet powerful step to enhancing the security of your online accounts. By adding an extra layer of protection, you can significantly reduce the risk of unauthorized access and safeguard your sensitive information. Take the time to enable 2FA on all your critical accounts and enjoy the peace of mind that comes with knowing your data is secure.
Best Practices for Secure Two-Factor Authentication Implementation

Two-factor authentication (2FA) is a vital security measure that adds an extra layer of protection to user accounts. By requiring users to provide two distinct forms of authentication, 2FA significantly reduces the risk of unauthorized access, even if one factor is compromised. However, implementing 2FA effectively requires careful consideration of best practices to ensure maximum security and usability.
Choose Strong Authentication Methods
The effectiveness of 2FA hinges on the strength of the authentication methods employed. Avoid weak or easily guessable factors like SMS codes, which are susceptible to SIM swapping attacks. Instead, opt for more robust methods like:
- Time-based One-Time Password (TOTP) applications: These apps generate unique codes that expire after a short time, making them significantly harder to intercept.
- Hardware security keys: These physical devices provide a highly secure and tamper-proof method of authentication, offering excellent protection against phishing attacks.
- Biometric authentication: Fingerprint scanning, facial recognition, or iris scanning can offer convenient and secure authentication methods, but their effectiveness depends on the quality of the technology employed.
Implement Strong Password Policies
While 2FA provides an extra layer of security, strong password policies are still crucial. Encourage users to create strong, unique passwords for each account and enforce password complexity requirements like:
- Minimum length: Require a minimum password length of 12 characters or more.
- Character variety: Enforce the inclusion of uppercase and lowercase letters, numbers, and symbols.
- Password complexity: Avoid common or easily guessable passwords.
Enable 2FA for All Critical Accounts
2FA should be enabled for all accounts that contain sensitive information, including:
- Financial accounts: Banks, payment platforms, and investment accounts.
- Email accounts: Email accounts are often used as a primary point of contact for account recovery, making them particularly important to secure.
- Social media accounts: Social media accounts can contain personal information and sensitive data.
Ensure User Friendliness and Accessibility
While security is paramount, 2FA implementation should not hinder usability. Consider these aspects:
- Easy setup: Make the process of setting up 2FA straightforward and intuitive for users.
- Multiple authentication options: Offer users a choice of authentication methods to accommodate their preferences and device capabilities.
- Accessibility: Ensure that 2FA is accessible to users with disabilities by providing alternative methods of authentication.
Regularly Review and Update Security Measures
Security threats are constantly evolving, so it’s crucial to regularly review and update your 2FA implementation. Ensure that you are using the latest versions of authentication methods and software and stay informed about emerging security best practices.
Conclusion
Implementing 2FA effectively is essential for protecting user accounts and sensitive data. By following these best practices, organizations and individuals can significantly reduce the risk of unauthorized access and build a stronger defense against cyber threats.
Addressing Common Challenges in Two-Factor Authentication Adoption
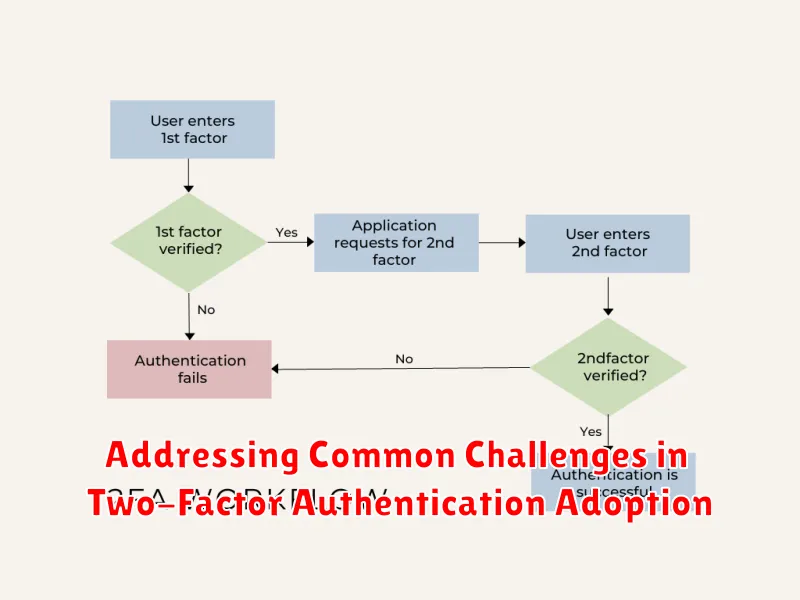
Two-factor authentication (2FA) is an essential security measure for online accounts. It adds an extra layer of protection by requiring users to provide two forms of identification before granting access. Despite its numerous benefits, many organizations and individuals still face challenges in adopting 2FA. This article will explore some common challenges and provide practical solutions to overcome them.
User Friendliness and Complexity
One of the biggest hurdles is the perception that 2FA is cumbersome and difficult to use. Users may find the extra step of entering a code or using a physical token inconvenient, especially for frequently accessed accounts. To address this, organizations should prioritize user-friendly implementation. Implementing easy-to-understand instructions, providing multiple authentication methods, and offering seamless integration with existing workflows can significantly improve the user experience.
Security Trade-offs and Concerns
Some users may be hesitant to adopt 2FA due to concerns about security trade-offs. For instance, they might worry about the security of their authentication app or the potential for phishing attacks targeting their second factor. It’s crucial to address these concerns by educating users about the benefits of 2FA and emphasizing the security measures in place. Organizations should also implement robust security protocols, including encryption and multi-factor authentication for their own systems, to build trust and encourage adoption.
Technical Limitations and Compatibility Issues
Technical limitations and compatibility issues can also hinder 2FA adoption. Some older devices or systems may not support 2FA, or the implementation might be incompatible with specific browsers or operating systems. Organizations should assess their infrastructure and identify potential compatibility issues. They can then provide alternative authentication methods, such as SMS codes or hardware tokens, and work with vendors to resolve any compatibility problems.
Conclusion
Addressing common challenges in 2FA adoption is essential for enhancing online security. By prioritizing user friendliness, addressing security concerns, and overcoming technical limitations, organizations can encourage widespread adoption of this crucial security measure. Through education, communication, and ongoing support, we can create a safer online environment for everyone.
Enhancing Security with Multi-Factor Authentication
In today’s digital landscape, where data breaches are becoming increasingly common, it is crucial to implement robust security measures to protect sensitive information. One of the most effective ways to enhance security is through multi-factor authentication (MFA). MFA adds an extra layer of protection by requiring users to provide multiple forms of authentication before granting access to accounts or systems.
Traditional passwords, while widely used, are vulnerable to attacks such as phishing and brute force. However, MFA significantly reduces the risk of unauthorized access by requiring users to present additional proof of identity beyond just their password. This can be achieved through various methods, including:
- One-time passwords (OTPs): These are unique codes generated by an authenticator app or hardware token, which expire after a short period.
- Biometrics: This involves using unique biological traits, such as fingerprint scanning, facial recognition, or iris scanning, for identification.
- Security keys: These are small, physical devices that plug into a computer or mobile device and generate a random code for authentication.
- Push notifications: Users receive a notification on their mobile device that they must approve to complete the login process.
By implementing MFA, organizations and individuals can significantly reduce the likelihood of unauthorized access, even if a password is compromised. It effectively mitigates the risks associated with weak passwords, stolen credentials, and phishing attacks.
Here are some key benefits of using MFA:
- Enhanced account security: MFA adds an additional barrier to unauthorized access, making it significantly more difficult for attackers to gain access to accounts.
- Reduced risk of data breaches: By preventing unauthorized logins, MFA helps to protect sensitive data from falling into the wrong hands.
- Improved compliance: Many regulations, such as GDPR and HIPAA, require organizations to implement strong authentication measures, including MFA.
- Increased user confidence: Knowing that their accounts are protected with MFA can give users peace of mind and enhance their trust in the organization or service.
In conclusion, implementing MFA is a critical step towards enhancing security in the digital world. It provides a robust defense against various threats, safeguarding sensitive information and minimizing the risk of data breaches. By requiring multiple forms of authentication, MFA significantly strengthens account security and protects users from unauthorized access. As the digital landscape continues to evolve, it is essential for individuals and organizations to prioritize security measures like MFA to safeguard their data and ensure a secure online experience.
The Future of Authentication: Emerging Trends and Technologies
Authentication is a fundamental aspect of cybersecurity, ensuring that only authorized individuals can access sensitive data and systems. As technology continues to evolve, so too do the methods and technologies used for authentication. This article will delve into the emerging trends and technologies shaping the future of authentication, exploring how they are enhancing security, improving user experience, and driving innovation.
Beyond Passwords: The Rise of Multi-Factor Authentication (MFA)
Traditional password-based authentication is increasingly vulnerable to breaches and attacks. Multi-factor authentication (MFA) has emerged as a robust solution, requiring users to provide multiple forms of verification before granting access. This can include factors such as:
- Something you know: Password, PIN, security questions
- Something you have: Smartphone, security token, physical key
- Something you are: Biometric data like fingerprint, facial recognition, iris scan
MFA significantly enhances security by creating a layered defense against unauthorized access. By requiring multiple forms of verification, it becomes significantly harder for attackers to compromise an account, even if they obtain one of the authentication factors.
Biometric Authentication: A Seamless and Secure Future
Biometric authentication uses unique biological characteristics to identify and authenticate users. This technology has gained significant traction due to its ease of use, accuracy, and enhanced security. Common biometric methods include:
- Fingerprint scanning: Highly accurate and widely adopted, offering a convenient authentication method.
- Facial recognition: Growing in popularity, leveraging facial features for identification and verification.
- Iris scanning: Highly secure and unique, offering exceptional accuracy in identifying individuals.
Biometric authentication eliminates the need for passwords and other traditional authentication methods, creating a seamless and secure user experience. It’s particularly beneficial in scenarios requiring high security, such as financial transactions, access control systems, and mobile device authentication.
Passwordless Authentication: A New Era of Convenience and Security
Passwordless authentication aims to eliminate the reliance on passwords altogether. This emerging trend focuses on utilizing alternative authentication methods, such as:
- Push notifications: Users receive a notification on their trusted device to approve access.
- One-time passcodes (OTPs): Generated by authenticator apps or hardware tokens, offering a temporary and secure authentication factor.
- FIDO2 security keys: Small, physical devices that plug into a computer or mobile device, providing strong authentication.
Passwordless authentication enhances security by eliminating the vulnerability associated with password reuse and phishing attacks. It also improves user convenience by eliminating the need to remember complex passwords and the hassle of password resets.
The Rise of Blockchain and Decentralized Identity
Blockchain technology is revolutionizing various industries, and authentication is no exception. Decentralized identity solutions based on blockchain offer several advantages, including:
- Enhanced security: Cryptographic techniques ensure the integrity and immutability of user data.
- Increased privacy: Users have more control over their data, reducing the risk of data breaches.
- Improved interoperability: Users can manage their identities across multiple platforms and services.
Blockchain-based identity systems enable users to control their own digital identity, eliminating the need for centralized authorities and providing greater transparency and security.
Conclusion: A Future of Enhanced Security and Convenience
The future of authentication is characterized by a focus on enhancing security, improving user experience, and embracing innovation. The emerging trends discussed above, including MFA, biometric authentication, passwordless authentication, and blockchain-based identity solutions, are transforming how we authenticate and protect sensitive information. As technology continues to advance, we can expect even more sophisticated and secure authentication methods to emerge, shaping a future where access is both secure and convenient.