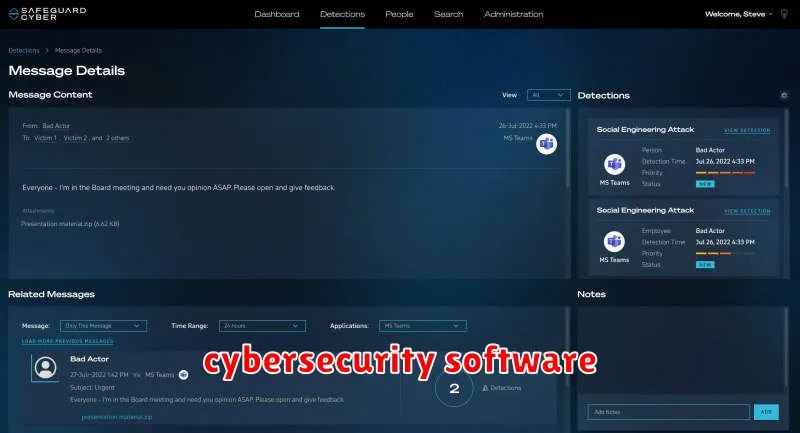
In today’s digital landscape, where cyberattacks are becoming increasingly sophisticated, businesses of all sizes are at risk. From data breaches to ransomware attacks, the consequences of a cyberattack can be devastating. To protect your business and its valuable data, investing in robust cybersecurity software solutions is essential.
This comprehensive guide will highlight the top cybersecurity software solutions for businesses in 2024. We will explore a range of options, including antivirus software, endpoint protection, firewalls, intrusion detection systems, data loss prevention, and more. By understanding the key features and benefits of each solution, you can make informed decisions to safeguard your business and navigate the ever-evolving cyber threat landscape.
Understanding the Cybersecurity Landscape for Businesses

In today’s digital age, cybersecurity is no longer an option, it’s a necessity. Businesses of all sizes are facing an increasingly complex and evolving threat landscape, making it more important than ever to understand the risks and implement robust security measures.
The cybersecurity landscape is constantly changing, with new threats emerging all the time. From sophisticated malware attacks to data breaches and ransomware, businesses need to be prepared for anything. The consequences of a successful cyberattack can be devastating, resulting in financial losses, reputational damage, and even legal action.
Key Cybersecurity Challenges
Here are some of the key challenges that businesses face in today’s cybersecurity landscape:
- Sophisticated attacks: Cybercriminals are becoming increasingly sophisticated in their methods, using advanced techniques to bypass traditional security measures.
- The rise of mobile devices: The proliferation of mobile devices has expanded the attack surface, making it more difficult to secure all endpoints.
- The Internet of Things (IoT): The growing number of connected devices creates new vulnerabilities, as many IoT devices lack proper security protocols.
- Data privacy regulations: Businesses are subject to increasingly stringent data privacy regulations, such as the GDPR and CCPA, which impose significant compliance obligations.
- The skills gap: There is a significant shortage of cybersecurity professionals, making it difficult for businesses to find and retain qualified talent.
Strategies for Protecting Your Business
To effectively navigate the cybersecurity landscape, businesses need to adopt a comprehensive and proactive approach. Here are some key strategies:
- Implement a strong security framework: This includes policies, procedures, and technologies designed to protect sensitive data and systems.
- Regularly update software and systems: Patching vulnerabilities promptly is essential to prevent attackers from exploiting known weaknesses.
- Train employees on security awareness: Educating employees about cybersecurity best practices can significantly reduce the risk of phishing attacks and other social engineering threats.
- Use multi-factor authentication: This adds an extra layer of security by requiring users to provide multiple forms of identification.
- Consider cybersecurity insurance: This can help mitigate the financial impact of a cyberattack.
- Partner with a cybersecurity expert: Engaging with a reputable cybersecurity firm can provide valuable expertise, support, and resources.
Cybersecurity is an ongoing journey, and businesses must stay vigilant and adapt to the evolving threat landscape. By understanding the key challenges and implementing robust security measures, businesses can protect their assets, reputation, and bottom line.
Essential Features of Top Cybersecurity Software

In today’s digital landscape, cybersecurity is more crucial than ever. With increasing cyber threats, businesses and individuals alike need robust protection to safeguard their sensitive data and systems. Top cybersecurity software offers a comprehensive suite of features to combat these threats and ensure digital security.
Antivirus and Anti-Malware Protection
A fundamental feature of any cybersecurity software is antivirus and anti-malware protection. This component scans your system for malicious software, such as viruses, worms, Trojans, and ransomware, and eliminates or quarantines them to prevent damage.
Firewall
A firewall acts as a barrier between your computer or network and the outside world. It analyzes incoming and outgoing network traffic, blocking unauthorized access and preventing malicious connections from entering your system.
Intrusion Detection and Prevention Systems (IDS/IPS)
Intrusion Detection and Prevention Systems (IDS/IPS) provide an extra layer of security by monitoring network activity for suspicious patterns. They can detect and block potential attacks before they cause harm, significantly reducing the risk of breaches.
Endpoint Security
Endpoint security protects individual devices, such as laptops, desktops, and mobile phones, from threats. It includes features like real-time threat monitoring, data loss prevention, and application control to ensure that endpoints remain secure.
Data Loss Prevention (DLP)
Data Loss Prevention (DLP) safeguards sensitive information from unauthorized access, use, or disclosure. This feature can identify and block attempts to transfer confidential data outside the organization, protecting valuable assets from theft or misuse.
Vulnerability Scanning
Vulnerability scanning identifies security weaknesses in your systems and applications. By regularly performing vulnerability scans, you can proactively address potential vulnerabilities and minimize the risk of exploitation by attackers.
Security Information and Event Management (SIEM)
Security Information and Event Management (SIEM) systems centralize security logs and events from various sources, providing a unified view of your security posture. They enable real-time threat detection, incident response, and security analysis, helping you stay ahead of potential threats.
User and Entity Behavior Analytics (UEBA)
User and Entity Behavior Analytics (UEBA) monitors user activities and identifies anomalies that may indicate malicious behavior. By analyzing patterns and deviations from normal behavior, UEBA can detect potential insider threats or compromised accounts.
Security Awareness Training
Security awareness training is crucial to educate users about cybersecurity best practices and common threats. By empowering users with knowledge, you can reduce the risk of phishing attacks, malware infections, and other security incidents.
Choosing the right cybersecurity software is essential for protecting your organization or personal data. By selecting a solution that includes the essential features mentioned above, you can effectively mitigate risks and ensure a secure digital environment. Remember to regularly update your software and follow best practices to stay ahead of evolving threats.
Best Antivirus Software for Business

In today’s digital world, businesses are increasingly vulnerable to cyberattacks. From malware to ransomware, cyber threats are constantly evolving and becoming more sophisticated. To protect your business from these threats, it is crucial to have a robust antivirus solution in place.
An antivirus software provides a critical layer of protection for your business by detecting, preventing, and removing malware from your systems. It also safeguards your sensitive data, protects your network, and ensures business continuity. But with so many antivirus products available, choosing the best one for your business can be overwhelming.
Key Features to Consider
Here are some key features to consider when choosing an antivirus software for your business:
- Real-time protection: This feature continuously monitors your systems for suspicious activity and blocks any threats before they can cause harm.
- Malware detection and removal: The antivirus should be able to detect and remove a wide range of malware, including viruses, worms, trojans, and ransomware.
- Firewall: A firewall is a crucial security feature that acts as a barrier between your network and the outside world, preventing unauthorized access.
- Anti-phishing protection: Phishing attacks are a common way for cybercriminals to steal sensitive information. A good antivirus solution will protect your business from these attacks.
- Email security: Email is one of the most common ways for malware to spread. The antivirus should have strong email security features to protect your business from these threats.
- Endpoint protection: This feature protects all devices on your network, including laptops, desktops, and mobile devices.
- Centralized management: A centralized management console makes it easy to manage the antivirus across all your devices.
- Technical support: It’s essential to have access to technical support in case you encounter any issues.
Top Antivirus Software for Business
Here are some of the top antivirus software options for business:
- Bitdefender GravityZone: This comprehensive solution offers a wide range of features, including real-time protection, malware detection and removal, firewall, anti-phishing, and endpoint protection.
- Symantec Endpoint Protection: Symantec Endpoint Protection provides robust protection against various threats, including malware, ransomware, and zero-day exploits.
- Trend Micro Worry-Free Services: Trend Micro offers a cloud-based antivirus solution that provides real-time protection, email security, and endpoint protection for businesses of all sizes.
- Sophos Intercept X: Intercept X is a next-generation antivirus solution that uses advanced AI and machine learning to detect and block even the most sophisticated threats.
- McAfee Total Protection for Business: McAfee offers a comprehensive security solution that includes antivirus, firewall, anti-phishing, and data loss prevention.
Conclusion
Choosing the best antivirus software for your business is a crucial decision. It’s important to consider your specific needs and requirements, such as the size of your business, the types of data you handle, and your budget. By investing in a robust antivirus solution, you can protect your business from cyber threats and keep your data safe.
Robust Firewall Protection for Enhanced Security

In today’s digital landscape, where cyber threats are becoming increasingly sophisticated, robust firewall protection is essential for safeguarding sensitive data and ensuring the integrity of your network. Firewalls act as the first line of defense, meticulously scrutinizing incoming and outgoing network traffic, blocking unauthorized access and malicious activities. This comprehensive guide will delve into the critical aspects of firewall protection, empowering you to fortify your digital infrastructure against a multitude of threats.
Understanding the Role of Firewalls
At its core, a firewall serves as a security barrier between your network and the external world. It acts as a gatekeeper, meticulously examining each network connection request and allowing only legitimate traffic to pass through. This vigilant scrutiny is crucial in preventing unauthorized access to your systems, data breaches, and other cyberattacks.
Types of Firewalls
Firewalls come in various forms, each tailored to specific security needs. Let’s explore the two primary types:
- Hardware Firewalls: These physical devices are typically deployed at the network edge, offering a robust barrier against external threats. They are renowned for their high performance and advanced security features, making them ideal for large enterprises and organizations with critical infrastructure.
- Software Firewalls: These virtual firewalls are installed directly on individual computers or servers. While not as powerful as hardware counterparts, they provide essential protection for smaller networks or individual systems. Software firewalls are often included as part of operating system installations or as independent applications.
Key Features of Firewalls
Modern firewalls boast a wide array of security features designed to thwart cyber threats. Some of the most prominent features include:
- Packet Filtering: This fundamental feature involves examining network packets based on various criteria, such as source and destination IP addresses, port numbers, and protocols. By analyzing these characteristics, firewalls can identify and block suspicious traffic.
- Stateful Inspection: This advanced technique goes beyond simple packet filtering by tracking the state of network connections. It allows firewalls to monitor the flow of data within a connection, ensuring that only legitimate traffic is permitted.
- Intrusion Detection and Prevention (IDS/IPS): These features detect and respond to malicious activity within the network. They monitor traffic patterns for suspicious behavior, such as known attack signatures or attempts to exploit vulnerabilities. When threats are identified, firewalls can take action to block or mitigate them.
- VPN Support: Many firewalls integrate with Virtual Private Networks (VPNs), allowing secure remote access to network resources. VPNs encrypt traffic and route it through secure tunnels, enhancing privacy and security for users working outside the office.
- Application Control: This feature enables administrators to control which applications are allowed to communicate with the internet or other networks. By restricting access to certain applications, organizations can reduce the risk of malware infections and data leaks.
- Centralized Management: Sophisticated firewalls offer centralized management consoles, allowing administrators to monitor and configure multiple firewalls from a single location. This streamlined approach simplifies management tasks and enhances overall security posture.
Implementing Robust Firewall Protection
To achieve optimal firewall protection, consider the following best practices:
- Choose the Right Firewall: Select a firewall that aligns with your specific security needs, network size, and budget. Consider factors like performance, features, and ease of management.
- Implement Strong Passwords: Secure your firewall with strong passwords to prevent unauthorized access. Use complex combinations of letters, numbers, and symbols.
- Keep Your Firewall Updated: Regularly update your firewall software to ensure you have the latest security patches and bug fixes. This is crucial for staying ahead of emerging threats.
- Configure Firewall Rules: Carefully configure firewall rules to allow only legitimate traffic while blocking suspicious or unnecessary connections. Review and adjust rules periodically.
- Monitor Firewall Logs: Actively monitor firewall logs for suspicious activity or security incidents. Timely detection can help prevent further damage.
- Train Employees: Educate employees about cybersecurity best practices, including the importance of strong passwords, safe browsing habits, and phishing awareness. This can help reduce the risk of accidental breaches.
Conclusion
Robust firewall protection is paramount in today’s digital landscape. By understanding the role of firewalls, leveraging their key features, and implementing best practices, you can significantly enhance your network security. Remember, a multi-layered security approach that combines firewalls with other security measures, such as antivirus software and intrusion detection systems, is crucial for achieving a truly comprehensive defense against cyber threats.
Intrusion Detection and Prevention Systems (IDPS)
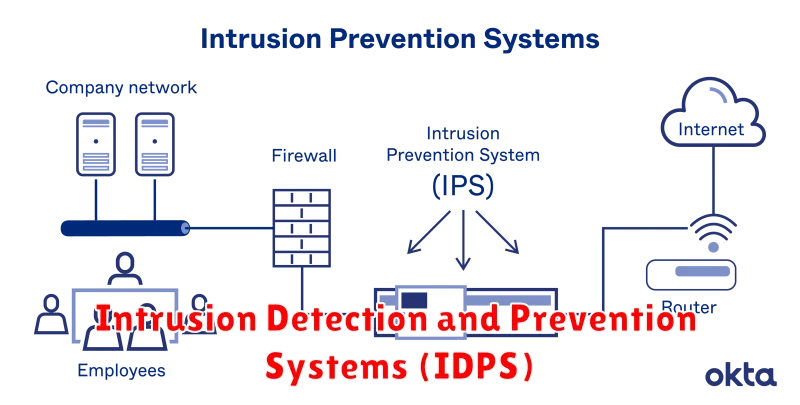
Intrusion detection and prevention systems (IDPS) are a critical component of cybersecurity, providing a robust defense against a wide range of threats. They act as the first line of defense, safeguarding networks and systems from malicious attacks, unauthorized access, and data breaches.
IDPS work by monitoring network traffic and system activity for suspicious patterns and behaviors. They employ a variety of techniques, including:
- Signature-based detection: Identifying known malicious patterns or signatures in network traffic.
- Anomaly detection: Detecting deviations from normal network activity and identifying potential threats based on statistical analysis.
- Behavioral analysis: Analyzing user behavior and identifying suspicious actions that deviate from established patterns.
Types of IDPS
IDPS can be categorized into two main types:
- Intrusion Detection Systems (IDS): These systems are primarily designed to detect malicious activity and alert administrators. They passively monitor network traffic and generate alerts when suspicious activity is detected.
- Intrusion Prevention Systems (IPS): These systems are more proactive, taking steps to prevent malicious activity from reaching its target. They can block suspicious traffic, reset connections, and even modify firewall rules in real-time.
Benefits of Implementing IDPS
Implementing an IDPS offers numerous benefits for organizations, including:
- Enhanced security: IDPS act as a first line of defense, protecting against a wide range of threats, including malware, phishing attacks, and denial-of-service attacks.
- Improved threat detection: They can detect and alert administrators to threats that might otherwise go unnoticed.
- Reduced security risks: By proactively preventing malicious activity, IDPS help reduce the risk of data breaches, system compromises, and financial losses.
- Compliance with regulations: IDPS can help organizations comply with industry regulations and data privacy laws.
Deployment Considerations
When implementing an IDPS, organizations should consider several factors:
- Network architecture: The network topology and size should be considered to determine the optimal placement of IDPS devices.
- Performance impact: IDPS can consume significant network bandwidth and resources. It’s essential to choose an IDPS solution that minimizes performance impact.
- Management and maintenance: IDPS require ongoing management and maintenance to ensure their effectiveness.
- Integration with other security tools: IDPS should be integrated with other security tools, such as firewalls, antivirus software, and SIEM systems, to create a comprehensive security posture.
Conclusion
Intrusion detection and prevention systems are a critical component of any robust cybersecurity strategy. By implementing an effective IDPS, organizations can strengthen their security posture, mitigate threats, and protect their valuable assets.
Data Loss Prevention (DLP) Solutions
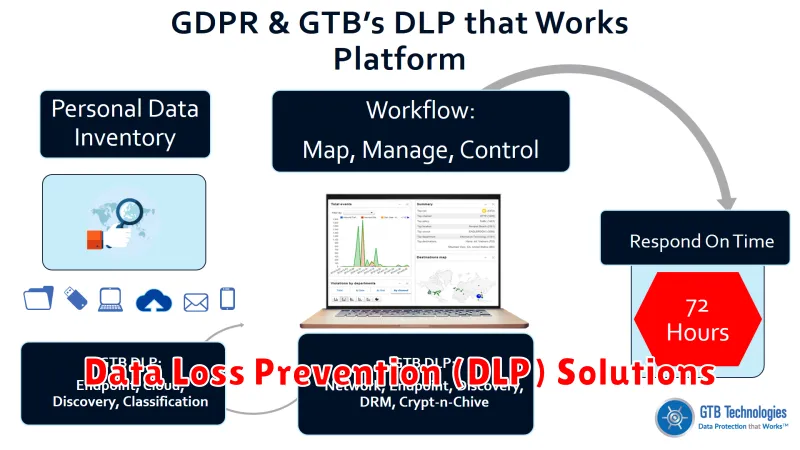
In today’s digital age, data security is paramount. With sensitive information being constantly accessed, shared, and stored, businesses face an ever-present threat of data breaches. To mitigate this risk, organizations are turning to Data Loss Prevention (DLP) solutions. DLP is a comprehensive approach to protecting sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction. DLP solutions employ a range of technologies and techniques to identify, monitor, and control data movement across various channels, both within and outside the organization.
DLP solutions typically consist of the following components:
- Data Discovery and Classification: This stage involves identifying and classifying sensitive data based on predefined rules and policies.
- Data Monitoring and Analysis: Continuous monitoring of data activity across various endpoints and systems, including email, web browsing, and file transfers, helps detect suspicious patterns and potential data breaches.
- Data Protection Controls: Implementing safeguards to prevent unauthorized access, use, and disclosure of sensitive data. These controls can include encryption, access control, and data masking.
- Alerting and Reporting: Generating real-time alerts and comprehensive reports to notify security teams about potential data breaches and provide insights into data security posture.
The benefits of implementing DLP solutions are numerous, including:
- Enhanced Data Security: By proactively identifying and protecting sensitive data, DLP solutions significantly reduce the risk of data breaches.
- Compliance with Regulations: DLP solutions help organizations meet compliance requirements, such as GDPR, HIPAA, and PCI DSS, by ensuring data privacy and confidentiality.
- Improved Risk Management: By providing visibility into data activity and potential security threats, DLP solutions enhance risk management capabilities and help organizations make informed decisions.
- Cost Reduction: By preventing data breaches and minimizing the impact of security incidents, DLP solutions can save organizations significant costs associated with data recovery, legal fees, and reputational damage.
In conclusion, DLP solutions play a crucial role in safeguarding sensitive data in today’s digital landscape. By implementing a comprehensive DLP strategy, organizations can effectively mitigate data security risks, ensure compliance with regulations, and protect their valuable assets.
Security Information and Event Management (SIEM)

Security information and event management (SIEM) is a type of security software that provides real-time analysis of security alerts generated by various sources within a network. It aggregates security data from multiple sources, normalizes it, and then analyzes it for potential security threats. SIEM systems can help organizations detect and respond to security incidents more quickly and effectively.
Key Features of SIEM
SIEM systems typically include the following features:
- Log collection and aggregation: SIEM systems collect logs from various sources, including firewalls, intrusion detection systems (IDS), antivirus software, and servers.
- Log normalization: SIEM systems normalize logs from different sources so that they can be analyzed in a consistent way.
- Correlation and analysis: SIEM systems use correlation rules to identify potential security threats by analyzing patterns in the data.
- Alerting and reporting: SIEM systems generate alerts when suspicious activity is detected. They also provide detailed reports on security incidents.
- Incident response: SIEM systems can help organizations to respond to security incidents more effectively by providing information about the incident and potential remediation steps.
Benefits of Using SIEM
There are many benefits to using SIEM, including:
- Improved threat detection: SIEM systems can help organizations to detect threats that might otherwise go unnoticed.
- Faster incident response: SIEM systems can help organizations to respond to security incidents more quickly and effectively.
- Reduced security risk: By detecting and responding to threats more effectively, SIEM systems can help organizations to reduce their security risk.
- Improved compliance: SIEM systems can help organizations to comply with security regulations, such as PCI DSS and HIPAA.
- Centralized security management: SIEM systems provide a single platform for managing security data and events.
Challenges of Using SIEM
While SIEM can provide many benefits, there are also some challenges associated with its implementation and use:
- Complexity: SIEM systems can be complex to configure and manage.
- Cost: SIEM systems can be expensive to purchase and implement.
- Data overload: SIEM systems can generate a large amount of data, which can be difficult to manage and analyze.
- False positives: SIEM systems can sometimes generate false positives, which can lead to wasted time and effort.
Conclusion
SIEM is a powerful tool that can help organizations to improve their security posture. However, it is important to carefully consider the challenges involved before implementing a SIEM solution. By carefully planning and implementing a SIEM solution, organizations can reap the many benefits of this technology.
Cloud Security Solutions for Modern Businesses
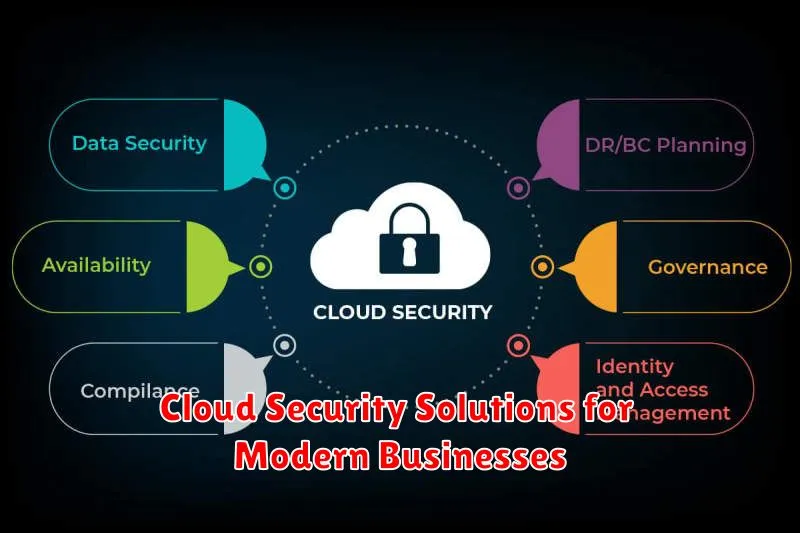
In today’s digital landscape, businesses are increasingly relying on cloud computing to improve efficiency, scalability, and cost-effectiveness. However, this transition also brings new security challenges. As data and applications move to the cloud, it’s crucial to implement robust security measures to protect sensitive information and ensure business continuity.
This article will explore the key cloud security solutions that modern businesses should adopt. We’ll cover essential topics such as:
- Data Encryption: Encrypting data both at rest and in transit is a fundamental security practice. Cloud providers offer various encryption options, including encryption keys managed by the customer.
- Identity and Access Management (IAM): Implementing strong IAM controls is essential for limiting unauthorized access to cloud resources. This involves using multi-factor authentication, role-based access control, and regular security audits.
- Network Security: Securing cloud networks is paramount. This can be achieved through firewalls, intrusion detection and prevention systems (IDS/IPS), and virtual private networks (VPNs).
- Security Monitoring and Threat Detection: Continuously monitoring cloud environments for suspicious activities is crucial. Cloud security information and event management (SIEM) tools and threat intelligence services can help identify and respond to potential threats.
- Vulnerability Management: Regularly scanning cloud applications and infrastructure for vulnerabilities is critical. Automated vulnerability scanning tools and penetration testing can help identify and address security weaknesses.
- Data Loss Prevention (DLP): Protecting sensitive data from unauthorized disclosure is paramount. DLP solutions can monitor data transfers, detect suspicious activities, and enforce data access policies.
- Cloud Security Posture Management (CSPM): CSPM tools provide a comprehensive view of cloud security posture. They can assess compliance with security best practices, identify misconfigurations, and provide remediation recommendations.
By implementing these cloud security solutions, businesses can significantly enhance their security posture and mitigate the risks associated with cloud adoption. Remember, cloud security is an ongoing process that requires continuous monitoring, evaluation, and adaptation to emerging threats.
Investing in cloud security solutions is essential for modern businesses seeking to protect their valuable data, ensure business continuity, and maintain customer trust. By taking proactive measures to secure their cloud environments, businesses can leverage the benefits of cloud computing with peace of mind.
Employee Training and Awareness Programs

Employee training and awareness programs are crucial for any organization’s success. They equip employees with the knowledge, skills, and understanding necessary to perform their roles effectively, comply with regulations, and contribute to the overall goals of the company. These programs cover a wide range of topics, including safety, compliance, customer service, product knowledge, and professional development.
One of the primary benefits of employee training and awareness programs is enhanced productivity. By providing employees with the necessary skills and knowledge, organizations can improve efficiency, reduce errors, and boost output. Well-trained employees are better equipped to handle tasks, solve problems, and make informed decisions, leading to increased productivity and a positive impact on the bottom line.
Another significant benefit is improved safety. Safety training programs educate employees on workplace hazards, safety protocols, and emergency procedures. This knowledge helps prevent accidents, injuries, and illnesses, creating a safer work environment for everyone. In industries with inherent safety risks, such as construction or manufacturing, safety training is paramount.
Compliance with regulations is essential for any organization to avoid legal issues and penalties. Training programs ensure that employees are aware of and understand applicable laws, regulations, and industry standards. This knowledge helps them make ethical and compliant decisions in their daily work, protecting the organization from legal repercussions.
Furthermore, employee training and awareness programs contribute to employee satisfaction and retention. When employees feel valued and supported through ongoing training and development opportunities, they are more likely to be satisfied with their jobs and committed to the organization. This leads to reduced turnover rates, lower recruitment costs, and a more stable workforce.
In today’s rapidly changing business environment, continuous learning is essential. Employee training and awareness programs provide a platform for ongoing professional development, enabling employees to stay updated on industry trends, acquire new skills, and advance their careers. This fosters a culture of learning and innovation, driving organizational growth and competitiveness.
In conclusion, employee training and awareness programs are an essential investment for any organization. They lead to enhanced productivity, improved safety, compliance with regulations, employee satisfaction and retention, and continuous professional development. By prioritizing training and development, organizations can empower their employees, create a positive work environment, and achieve long-term success.
Choosing the Right Cybersecurity Software for Your Business

In today’s digital age, cybersecurity is more crucial than ever. Businesses of all sizes are vulnerable to cyberattacks, which can result in significant financial losses, reputational damage, and even legal repercussions. To protect your business, it is essential to invest in robust cybersecurity software. However, with a wide range of options available, choosing the right software can be a daunting task.
Factors to Consider When Choosing Cybersecurity Software
Here are some key factors to consider when selecting cybersecurity software for your business:
1. Your Business Needs
First and foremost, you need to assess your business’s specific cybersecurity needs. Consider the following:
- Industry: Different industries face different threats. For example, healthcare organizations need to protect sensitive patient data, while financial institutions are more vulnerable to fraud.
- Size: Larger businesses typically have more complex IT infrastructures and need more comprehensive cybersecurity solutions.
- Data Sensitivity: The type of data your business handles will also influence your software choices. For example, businesses that store sensitive financial information need more secure solutions.
2. Software Features
Once you understand your business needs, you can start looking at the features offered by different cybersecurity software solutions. Some common features include:
- Antivirus and Anti-Malware Protection: This is essential for protecting your devices from viruses and other malicious software.
- Firewall: A firewall acts as a barrier between your network and the internet, preventing unauthorized access.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems monitor your network for suspicious activity and take action to prevent attacks.
- Data Loss Prevention (DLP): DLP software helps to prevent sensitive data from leaving your network without authorization.
- Email Security: This protects your employees and customers from phishing attacks and other email-borne threats.
- Vulnerability Scanning: Regularly scanning your network for vulnerabilities can help identify and fix security weaknesses.
- Security Information and Event Management (SIEM): SIEM software helps you collect, analyze, and manage security data from across your organization.
3. Budget
Cybersecurity software can vary significantly in price. It’s important to set a budget and stick to it. Consider your business’s financial resources and prioritize the most essential features.
4. Ease of Use and Management
Choose software that is easy to use and manage, especially if your IT team is small or has limited experience. Look for solutions with intuitive interfaces and comprehensive documentation.
5. Vendor Support
Good vendor support is essential for any cybersecurity solution. Make sure the vendor offers 24/7 support, regular updates, and reliable technical assistance.
Choosing the Right Cybersecurity Software: A Summary
Choosing the right cybersecurity software can be a complex process. However, by considering your business needs, software features, budget, ease of use, and vendor support, you can make an informed decision that will help protect your business from cyber threats.