In today’s digital age, where our online activities are constantly tracked and monitored, protecting our privacy has become more crucial than ever. One of the most effective ways to safeguard your online privacy is by using a Virtual Private Network (VPN). A VPN encrypts your internet traffic and routes it through a server in another location, masking your IP address and making it difficult for anyone to track your online activities. But with so many VPNs available, choosing the best one for your needs can be overwhelming.
This comprehensive guide will walk you through everything you need to know about finding the best VPN for privacy. We’ll delve into the essential features to look for, discuss the different types of VPNs, and provide insights into how to choose a VPN that best suits your specific privacy requirements. Whether you’re concerned about government surveillance, protecting your data while using public Wi-Fi, or simply want to browse the internet anonymously, this guide will empower you to make an informed decision and secure your online privacy.
What is a VPN and How Does It Work?
A Virtual Private Network (VPN) is a technology that creates a secure and encrypted connection between your device and the internet. It essentially acts as a tunnel, protecting your online activity and data from prying eyes. While you might have heard of VPNs in the context of privacy and security, they also offer several other benefits, such as accessing geo-restricted content and bypassing censorship.
The core of how a VPN works involves routing your internet traffic through an intermediary server. This server is owned and operated by the VPN provider. When you connect to a VPN, your device sends all its internet traffic to the VPN server. The VPN server then relays this traffic to your destination, masking your IP address and encrypting the data. This means that your internet service provider (ISP) and other potential snoopers cannot see what you are doing online.
Here is a breakdown of how a VPN works:
- You connect to a VPN server: You install a VPN app on your device and connect to a server operated by the VPN provider.
- Your data is encrypted: The VPN encrypts your internet traffic, creating a secure tunnel between your device and the VPN server.
- Your data is routed through the VPN server: Your encrypted traffic is sent to the VPN server, which then relays it to your destination.
- Your IP address is masked: The VPN server replaces your actual IP address with its own, making it appear as if you are browsing from the location of the server.
Think of it like this: a VPN acts like a secure tunnel between your device and the internet. Instead of your data traveling directly to the websites you visit, it travels through the tunnel, where it is encrypted and your IP address is hidden. This makes it difficult for anyone to track your online activity or access your data.
Why Privacy Matters in the Digital Age
In today’s digital age, where our lives are increasingly intertwined with technology, privacy has become a paramount concern. From social media platforms to online shopping websites, our personal data is being collected and analyzed at an unprecedented rate. While this data can be used to provide personalized experiences and targeted advertising, it also poses significant risks to our privacy.
The Impact of Data Collection
The collection of our personal data has a profound impact on our lives. It can be used to:
- Track our online behavior and browsing history
- Target us with tailored advertising
- Create detailed profiles of our interests and preferences
- Influence our decisions and opinions
This information can be valuable to companies, but it can also be used for malicious purposes, such as identity theft, fraud, and discrimination.
The Importance of Privacy Protection
Protecting our privacy is crucial for several reasons:
- Freedom of expression: Fear of surveillance can stifle free speech and limit our ability to express ourselves openly.
- Personal autonomy: Privacy allows us to control our own information and make choices about how it is used.
- Security: Protecting our personal data helps to prevent identity theft and other security breaches.
- Equality: Privacy ensures that everyone has the right to control their information, regardless of their background or social status.
In a world where our data is constantly being collected and analyzed, privacy is not a luxury but a necessity.
Steps to Protect Your Privacy
There are several steps you can take to protect your privacy online:
- Use strong passwords and enable two-factor authentication.
- Be mindful of the information you share online and on social media.
- Review your privacy settings on all websites and apps you use.
- Use privacy-enhancing tools like VPNs and ad blockers.
- Stay informed about data privacy laws and regulations.
The Future of Privacy
The digital age is constantly evolving, and so are the threats to our privacy. It is important to stay vigilant and advocate for policies that protect our fundamental right to privacy.
Key Features to Look for in a Privacy-Focused VPN
In today’s digital age, safeguarding your online privacy is paramount. A Virtual Private Network (VPN) is an indispensable tool for enhancing your security and anonymity while browsing the internet. However, not all VPNs are created equal, and choosing a truly privacy-focused VPN requires careful consideration.
1. Strong Encryption
The backbone of any VPN’s privacy protection lies in its encryption. Look for VPNs that use robust encryption algorithms like AES-256, which is widely considered to be virtually unbreakable. This ensures that your data is scrambled and rendered incomprehensible to unauthorized parties.
2. No-Logs Policy
A strict no-logs policy is essential. This means that the VPN provider does not store any information about your browsing activity, traffic, or connection details. A reputable VPN provider will transparently publish its logging policy for scrutiny.
3. Kill Switch
A kill switch acts as a safety net, automatically disconnecting your internet connection if the VPN connection drops. This prevents accidental exposure of your IP address and ensures that your data remains protected.
4. Leak Protection
VPN services should include robust leak protection mechanisms to prevent DNS leaks and WebRTC leaks, which can compromise your privacy by exposing your real IP address.
5. Jurisdiction
The jurisdiction of the VPN provider can significantly impact your privacy. Companies based in countries with strong privacy laws and limited data retention requirements offer greater assurance of your online security.
6. Transparency and Auditability
Transparency is crucial. A reputable VPN provider will openly disclose its ownership, infrastructure, and security practices. Some providers undergo independent audits to verify their claims and enhance user trust.
7. Customer Support
Having access to reliable customer support can be invaluable, especially if you encounter any technical issues or need assistance with configuring the VPN.
Conclusion
Choosing a privacy-focused VPN is crucial for protecting your online activities from prying eyes. By considering the key features outlined above, you can find a VPN provider that prioritizes your privacy and security, empowering you to navigate the digital world with confidence.
Understanding VPN Protocols: OpenVPN, IKEv2, WireGuard
A Virtual Private Network (VPN) is a powerful tool that encrypts your internet traffic and routes it through a server in another location, providing privacy, security, and the ability to access geo-restricted content. While the concept of a VPN is straightforward, the underlying protocols that power these services can be complex and affect your overall experience. This guide will explore three popular VPN protocols: OpenVPN, IKEv2, and WireGuard, helping you understand their strengths, weaknesses, and suitability for different use cases.
OpenVPN
OpenVPN is a widely-used, open-source VPN protocol known for its robust security and strong encryption. It utilizes the TLS/SSL protocol, a standard for secure communication over the internet, to establish a secure tunnel. OpenVPN supports a variety of encryption ciphers and authentication methods, making it highly customizable and adaptable to different security requirements.
Strengths:
- Strong Security: OpenVPN’s open-source nature and extensive audit trail make it one of the most secure VPN protocols available.
- Compatibility: OpenVPN is compatible with a wide range of platforms and devices, including Windows, macOS, Linux, Android, and iOS.
- Customizability: OpenVPN offers various settings, allowing you to fine-tune the protocol to meet your specific needs.
Weaknesses:
- Performance: OpenVPN can be relatively resource-intensive, potentially leading to slower connection speeds and higher latency.
- Complexity: Setting up and configuring OpenVPN manually can be challenging for beginners.
IKEv2
IKEv2 (Internet Key Exchange version 2) is a VPN protocol developed by Cisco Systems and Microsoft. It offers strong security features and is often used by businesses and organizations due to its reliability and resilience to network changes.
Strengths:
- Speed and Performance: IKEv2 is known for its fast connection speeds and low latency, making it suitable for streaming and gaming.
- Reliability: IKEv2 is designed to be resilient to network changes, seamlessly reconnecting even when there are disruptions in your internet connection.
Weaknesses:
- Limited Platform Support: IKEv2 is not as widely supported as OpenVPN, with some platforms lacking native support.
- Less Customizability: IKEv2 offers fewer customization options compared to OpenVPN.
WireGuard
WireGuard is a relatively new VPN protocol that has gained popularity for its simplicity, speed, and efficiency. It utilizes modern cryptography and is designed to be lightweight and performant.
Strengths:
- Speed and Performance: WireGuard is incredibly fast and efficient, delivering significantly faster connection speeds compared to other protocols.
- Simplicity: WireGuard is simple to set up and configure, even for beginners.
- Security: WireGuard utilizes modern encryption algorithms and is considered to be very secure.
Weaknesses:
- Limited Platform Support: While WireGuard is gaining traction, its platform support is still developing.
Choosing the Right VPN Protocol
The best VPN protocol for you depends on your specific needs and priorities. Here’s a breakdown:
- OpenVPN: Ideal for users seeking maximum security and customizability, even if it means sacrificing some speed.
- IKEv2: Suitable for users who prioritize speed and reliability, especially for streaming and gaming.
- WireGuard: A great option for users who want the fastest speeds and a simple, easy-to-use VPN experience.
Ultimately, the best way to determine the best protocol for you is to try them out and see which one provides the best performance and user experience.
No-Logs Policy: Ensuring Your Data Stays Private
In today’s digital age, where data privacy is a growing concern, a no-logs policy stands as a beacon of security and trust. It’s a commitment by a company to not store or log any of your user data, ensuring that your online activities remain private and confidential.
Imagine a world where your internet browsing history, app usage, and online communications are constantly tracked and stored. This scenario can be unsettling for many, as it raises concerns about potential misuse or unauthorized access to sensitive information. A no-logs policy aims to alleviate these anxieties by providing a secure environment where your data is not collected or retained.
Why is a No-Logs Policy Important?
The importance of a no-logs policy can be understood by considering its benefits:
- Enhanced Privacy: It ensures that your personal information, browsing habits, and online activities remain private and inaccessible to third parties.
- Increased Security: By not storing data, the risk of data breaches and unauthorized access is significantly reduced.
- Transparency and Trust: A no-logs policy fosters trust between users and companies, as it demonstrates a commitment to user privacy.
- Compliance with Regulations: In many jurisdictions, data privacy regulations require companies to adopt measures that protect user data, and a no-logs policy can contribute to compliance.
How Does a No-Logs Policy Work?
A no-logs policy typically involves the following principles:
- No User Data Collection: The company refrains from collecting any identifiable user information, such as browsing history, IP addresses, or communication content.
- No Data Storage: Any temporary data used for service delivery is immediately deleted upon completion of the service.
- Third-Party Access Restrictions: The company does not share user data with third parties, ensuring that it remains protected.
- Regular Audits: Independent audits may be conducted to verify the implementation and effectiveness of the no-logs policy.
Examples of No-Logs Services
Several companies offer services that adhere to a strict no-logs policy. These include:
- VPN providers: VPNs that implement a no-logs policy encrypt your internet traffic and mask your IP address, providing anonymity and privacy.
- Messaging apps: Secure messaging apps that prioritize privacy often adopt a no-logs approach to ensure the confidentiality of your communications.
- Cloud storage providers: Some cloud storage services offer no-logs encryption to protect your data from unauthorized access.
Choosing a No-Logs Service
When selecting a service that claims to have a no-logs policy, it’s crucial to:
- Verify the policy: Thoroughly review the company’s privacy policy to confirm the details of their no-logs implementation.
- Seek independent audits: Look for evidence of independent audits that verify the company’s adherence to their no-logs policy.
- Consider reputation: Choose companies with a proven track record of privacy protection and transparency.
Conclusion
In an era where our digital footprint is constantly growing, a no-logs policy offers a valuable safeguard for privacy and security. By choosing services that prioritize a no-logs approach, you can protect your online activities from prying eyes and ensure that your data remains private and confidential.
Jurisdiction and Its Impact on VPN Privacy
In the digital age, where online privacy is paramount, the concept of jurisdiction plays a crucial role in understanding the impact of VPNs. A VPN (Virtual Private Network) encrypts internet traffic and routes it through a server in another location, offering a degree of anonymity and security. However, the jurisdiction of the VPN provider can significantly influence the level of privacy afforded to users.
Jurisdiction refers to the legal authority or power of a state, country, or other entity to govern and enforce laws within its territory. When it comes to VPNs, the jurisdiction where the provider is based determines the legal framework that governs the collection, storage, and handling of user data. This has significant implications for user privacy.
Data Retention Laws
One of the most prominent ways jurisdiction impacts VPN privacy is through data retention laws. Some countries have laws that require internet service providers, including VPN providers, to store user data for a specific period. This data can include browsing history, IP addresses, and timestamps, potentially compromising user privacy.
Surveillance and Law Enforcement
Another crucial factor is the level of surveillance and law enforcement powers in a jurisdiction. Some countries have extensive surveillance programs and broad powers for government agencies to access user data. If a VPN provider is based in a country with such practices, it may be legally obligated to cooperate with authorities, potentially exposing user information.
Privacy Policies and Transparency
While some VPN providers may have strong privacy policies, the legal framework of their jurisdiction can influence their ability to adhere to these promises. Countries with strong privacy laws and regulations can provide greater assurance that user data is protected. However, in countries with weaker privacy standards, VPN providers may have less incentive or legal obligation to safeguard user information.
Choosing a VPN: Jurisdiction Matters
When selecting a VPN service, it is essential to consider the jurisdiction of the provider. Look for VPNs based in countries known for strong privacy laws and regulations, such as Switzerland or Iceland. Additionally, research the provider’s privacy policy, data retention practices, and transparency regarding data collection and sharing.
Ultimately, understanding the impact of jurisdiction on VPN privacy is crucial for making informed decisions about online security and protecting personal data. By carefully evaluating the legal framework surrounding a VPN provider, users can choose services that offer a higher degree of privacy and anonymity.
Kill Switch and DNS Leak Protection
In today’s digital landscape, where internet connectivity is paramount, ensuring online privacy and security is crucial. Kill switch and DNS leak protection are two essential features that help safeguard your online activities.
What is a Kill Switch?
A kill switch, also known as an internet kill switch, is a security feature found in some VPNs (Virtual Private Networks) and other privacy-enhancing software. It acts as a safety net, immediately cutting off your internet connection if the VPN connection drops or fails. This prevents your real IP address from being exposed to the internet, thereby protecting your online privacy.
How Does a Kill Switch Work?
When you enable a kill switch, your VPN client monitors the VPN connection. If the connection is lost or interrupted, the kill switch automatically disables all internet traffic to and from your device. This ensures that your data remains secure, even if the VPN connection becomes unstable or disconnects unexpectedly.
What is DNS Leak Protection?
DNS (Domain Name System) leak protection is another vital feature that safeguards your online privacy. When you browse the internet, your device sends DNS requests to resolve domain names (like google.com) into IP addresses. These DNS requests can reveal your location and browsing history to third parties if not protected.
How Does DNS Leak Protection Work?
DNS leak protection encrypts all DNS requests sent by your device, ensuring that they are routed through the VPN server instead of your ISP. This prevents your ISP from monitoring your DNS requests and gaining access to your browsing history.
Why are Kill Switch and DNS Leak Protection Important?
Both kill switch and DNS leak protection are essential for maintaining online privacy and security. They protect your sensitive data from being intercepted or monitored by third parties. These features are particularly important if you are:
- Using public Wi-Fi networks.
- Accessing sensitive information online.
- Concerned about your online privacy.
Conclusion
Kill switch and DNS leak protection are invaluable features that enhance your online security. By implementing these measures, you can significantly reduce the risks associated with online privacy breaches and data leaks. Ensure that your VPN provider offers both these features to safeguard your online activities and enjoy a secure and private internet experience.
Speed and Performance Considerations
When building a website, it’s crucial to prioritize speed and performance. A fast-loading website not only provides a seamless user experience but also contributes to a positive brand image and improved SEO rankings. In today’s digital landscape, users expect instant gratification, and a slow website can quickly drive them away to competitors.
Several factors influence a website’s speed, including:
- Server response time: The time it takes for the server to process a request and send back the website’s content.
- File sizes: Large images, videos, and scripts can significantly slow down page loading times.
- Number of HTTP requests: Each request to load a resource (e.g., images, CSS files) adds to the overall loading time.
- Website code efficiency: Optimized code with minimal redundancies can lead to faster processing.
- Caching: Storing frequently accessed data locally can reduce the need for repeated server requests.
Here are some essential strategies to enhance website speed and performance:
Optimize Images
Images are often the biggest culprits behind slow page load times. Compress your images without sacrificing quality using tools like TinyPNG or Optimizilla. Use appropriate image formats like WebP, which offers superior compression compared to JPEG or PNG.
Minimize HTTP Requests
Combine multiple CSS files into one, reduce the number of external scripts, and use sprites for icons to reduce the number of HTTP requests.
Leverage Browser Caching
Configure your web server to enable browser caching, which allows browsers to store frequently accessed resources locally, minimizing server requests. Set appropriate cache expiration times for static files.
Use a Content Delivery Network (CDN)
CDNs deliver website content from servers geographically closer to users, reducing latency and improving loading times. They also handle peak traffic effectively, ensuring your website remains responsive even during high demand periods.
Optimize Website Code
Ensure your code is clean, efficient, and well-structured. Minimize unnecessary elements and remove any unused code. Consider using a code minifier to reduce file sizes.
Enable Lazy Loading
Lazy loading images only loads them when they appear in the user’s viewport, reducing initial page load time and improving perceived performance. This technique is particularly useful for websites with many images.
Monitor Performance
Regularly monitor your website’s performance using tools like Google PageSpeed Insights, Lighthouse, or GTmetrix. Identify areas for improvement and continuously optimize your website based on the insights gained.
By implementing these strategies, you can create a website that loads quickly and provides an enjoyable user experience. A fast website is essential for attracting and retaining visitors, boosting conversions, and ultimately achieving your online goals.
Choosing the Right VPN for Your Needs
In today’s digital age, where our online activity is constantly being monitored, a VPN (Virtual Private Network) has become an essential tool for protecting our privacy and security. A VPN encrypts your internet traffic and routes it through a server in a different location, effectively masking your IP address and making it difficult for anyone to track your online activity.
However, with so many VPN providers on the market, it can be overwhelming to choose the right one for your needs. This article will guide you through the key factors to consider when selecting a VPN.
Factors to Consider When Choosing a VPN
Here are some important factors to consider when choosing a VPN:
1. Security and Privacy
The most crucial aspect of any VPN is its security and privacy features. Look for a VPN that uses strong encryption protocols like AES-256 and has a no-logs policy. This ensures that your data is protected from prying eyes and your online activity is not logged or stored by the VPN provider.
2. Server Network and Location
A vast server network with servers in numerous locations is essential for accessing geo-restricted content and improving your internet speed. Choose a VPN with servers in the regions you frequently access content from.
3. Speed and Performance
A VPN can sometimes slow down your internet connection, especially if you choose a server that is far away or if the VPN is overloaded. Look for a VPN that prioritizes speed and performance, and try out different servers to see which one provides the best connection for you.
4. Compatibility and User Friendliness
Ensure that the VPN you choose is compatible with your devices and operating systems. The VPN should also be user-friendly, with a simple and intuitive interface.
5. Price and Value
VPN providers offer different pricing plans, so compare the features and value they provide before making a decision. Consider whether you need a long-term subscription or if a monthly plan is sufficient.
6. Customer Support
Having reliable customer support is essential in case you encounter any issues or have questions about the VPN. Look for a provider that offers 24/7 support via live chat, email, or phone.
Conclusion
Choosing the right VPN is crucial for protecting your online privacy and security. Consider the factors discussed above, such as security, server network, speed, compatibility, price, and customer support, to make an informed decision.
Remember, a good VPN should be a seamless and reliable part of your online experience, enhancing your privacy and security without sacrificing performance. Don’t compromise on your digital well-being – choose a VPN that meets your specific needs and provides the protection you deserve.
Free VPNs vs. Paid VPNs: Weighing the Trade-offs
In today’s digital landscape, where online privacy and security are paramount, Virtual Private Networks (VPNs) have become essential tools. VPNs encrypt your internet traffic and route it through a server in a different location, masking your IP address and protecting your data from prying eyes. While both free and paid VPNs exist, understanding the key differences and trade-offs is crucial for making an informed decision.
Free VPNs: The Allure of Free
The allure of free VPNs is undeniable. They offer a seemingly effortless way to enhance your online privacy and bypass geo-restrictions without spending a dime. However, the reality is often far more nuanced. Here’s a breakdown of the typical limitations of free VPNs:
- Limited Server Locations: Free VPNs typically offer a restricted selection of server locations, limiting your ability to access geographically restricted content or improve your browsing speeds.
- Slower Speeds: Free VPNs often struggle to provide high-speed connections due to server overload and bandwidth limitations. This can lead to frustrating buffering and lag during streaming or downloading.
- Data Caps: Many free VPNs impose data caps, restricting the amount of data you can transfer through their servers each month. This can be a significant constraint if you’re a heavy internet user.
- Compromised Security: Free VPNs may compromise your security by collecting and selling your browsing data to third-party advertisers. Some even engage in malware or phishing practices, putting your devices at risk.
- Limited Features: Free VPNs generally lack advanced features such as kill switches, split tunneling, and dedicated streaming servers. These features enhance security and improve performance, but are often reserved for paid plans.
Paid VPNs: Investing in Security and Performance
While free VPNs offer a tempting alternative, paid VPNs provide a more reliable and secure online experience. Here are the advantages of choosing a paid VPN:
- Enhanced Privacy and Security: Paid VPNs prioritize user privacy and invest in robust security measures. They often offer military-grade encryption, no-logging policies, and advanced features like kill switches, ensuring your data remains protected.
- Faster Speeds: Paid VPNs have access to a wider network of servers with ample bandwidth, resulting in significantly faster speeds compared to free options. This translates into smoother streaming, faster downloads, and a more enjoyable online experience.
- Unlimited Data: Paid VPNs typically offer unlimited data usage, allowing you to browse, stream, and download without worrying about exceeding limits. This is particularly beneficial for heavy internet users.
- Excellent Customer Support: Paid VPNs usually provide responsive and reliable customer support, ensuring that any technical issues or concerns are addressed promptly. This added layer of support can be crucial for users who need assistance with setting up or using their VPN.
Weighing the Trade-offs: Finding the Right Fit
Ultimately, the decision of whether to choose a free or paid VPN depends on your individual needs and priorities. If you’re primarily concerned with basic privacy protection and occasional use, a free VPN may suffice. However, if you value enhanced security, reliable performance, unlimited data, and advanced features, a paid VPN is the wiser choice.
Remember, compromising on security can have serious consequences. Investing in a reputable paid VPN provides peace of mind knowing that your online activities are protected and your data is secure. As the saying goes, “You get what you pay for.”
Top-Rated VPN Services for Privacy
In today’s digital world, protecting your privacy online is more important than ever. With growing concerns about government surveillance, data breaches, and online tracking, a Virtual Private Network (VPN) has become an essential tool for safeguarding your personal information. A VPN encrypts your internet traffic and routes it through a secure server, masking your IP address and making it difficult for anyone to track your online activity. With so many VPN services available, it can be overwhelming to choose the best one for your needs. This article will guide you through some of the top-rated VPN services for privacy, focusing on their key features, pros, and cons.
1. NordVPN
NordVPN is widely recognized as one of the leading VPN providers, renowned for its strong security features and vast server network. Here’s a breakdown of its key strengths:
- Robust Encryption: NordVPN uses industry-standard 256-bit AES encryption, ensuring your data is highly secure.
- No-Logs Policy: NordVPN strictly adheres to a no-logs policy, meaning they don’t track or store any of your browsing history or activity.
- Extensive Server Network: With over 5,500 servers in 60+ countries, NordVPN provides access to a wide range of server locations.
- Dedicated Streaming Servers: NordVPN offers specialized servers optimized for streaming services like Netflix, BBC iPlayer, and Hulu, enabling you to access geographically restricted content.
- Kill Switch Feature: NordVPN’s kill switch feature automatically cuts off your internet connection if the VPN connection drops, preventing any accidental data leaks.
Pros:
- Strong security and privacy features.
- Extensive server network.
- Dedicated streaming servers.
- User-friendly interface.
Cons:
- Can be slightly more expensive than some competitors.
2. ExpressVPN
ExpressVPN is another popular VPN service known for its blazing-fast speeds and exceptional customer support. Its key features include:
- Lightning-Fast Speeds: ExpressVPN is renowned for its fast connection speeds, making it ideal for streaming and online gaming.
- Strict No-Logs Policy: Similar to NordVPN, ExpressVPN maintains a strict no-logs policy, safeguarding your privacy.
- Global Server Network: With over 3,000 servers in 94 countries, ExpressVPN provides ample server choices.
- TrustedServer Technology: ExpressVPN’s TrustedServer technology ensures that its servers are physically secure and tamper-proof.
- Split Tunneling: ExpressVPN’s split tunneling feature allows you to choose which apps use the VPN connection and which use your regular internet connection.
Pros:
- Fast connection speeds.
- Excellent customer support.
- TrustedServer technology enhances security.
- Split tunneling feature for flexibility.
Cons:
- More expensive than some other options.
3. Surfshark
Surfshark offers a compelling combination of affordability, performance, and strong security features, making it a popular choice for budget-conscious users. Its key highlights are:
- Unlimited Simultaneous Connections: Surfshark allows you to connect an unlimited number of devices with a single subscription, making it ideal for families or those with multiple devices.
- CleanWeb Feature: Surfshark’s CleanWeb feature blocks malware, ads, and trackers, enhancing your online safety.
- NoBorders Mode: Surfshark’s NoBorders mode circumvents internet censorship, enabling you to access blocked websites and services.
- MultiHop Feature: Surfshark’s MultiHop feature routes your traffic through multiple VPN servers, adding an extra layer of security and anonymity.
Pros:
- Affordable pricing.
- Unlimited simultaneous connections.
- CleanWeb feature for enhanced security.
- MultiHop feature for extra privacy.
Cons:
- Server network is smaller than some competitors.
4. CyberGhost
CyberGhost is known for its user-friendly interface and robust security measures. Key features include:
- Dedicated Streaming Profiles: CyberGhost offers dedicated profiles for popular streaming services, making it easy to access geographically restricted content.
- Automatic Wi-Fi Protection: CyberGhost automatically connects to a VPN server when you join a public Wi-Fi network, ensuring your security.
- 7 Simultaneous Connections: CyberGhost allows you to connect up to seven devices simultaneously.
- Strict No-Logs Policy: CyberGhost adheres to a strict no-logs policy, protecting your online privacy.
Pros:
- User-friendly interface.
- Dedicated streaming profiles.
- Automatic Wi-Fi protection.
- Multiple simultaneous connections.
Cons:
- Can be slightly slower than some competitors.
5. Private Internet Access (PIA)
Private Internet Access (PIA) is a popular choice for privacy-conscious users, offering a combination of affordability, security, and speed. Its key features include:
- WireGuard Protocol Support: PIA supports the WireGuard protocol, known for its fast speeds and strong security.
- MACE Feature: PIA’s MACE feature blocks ads, trackers, and malware, enhancing your online experience.
- SOCKS5 Proxy Support: PIA offers SOCKS5 proxy support, which can be used for bypassing geo-restrictions and enhancing privacy.
- Large Server Network: PIA has a large server network with over 35,000 servers in 84 countries.
Pros:
- Affordable pricing.
- WireGuard protocol support for fast speeds.
- MACE feature for enhanced online security.
- Large server network.
Cons:
- Can be slightly slower than some competitors.
Conclusion
Choosing the right VPN service for your privacy depends on your individual needs and priorities. Whether you’re looking for the strongest security features, the fastest speeds, or the most affordable option, there’s a VPN service out there that’s perfect for you. By carefully considering the key features, pros, and cons of each service, you can select the VPN that best protects your online privacy and enhances your digital experience.
Using a VPN on Different Devices
A Virtual Private Network (VPN) is a powerful tool that can enhance your online privacy and security. It encrypts your internet traffic and routes it through a server in another location, making it difficult for third parties to track your online activities. One of the biggest advantages of using a VPN is that it can be used on a variety of devices, including your computer, smartphone, tablet, and even your smart TV.
Computers
Using a VPN on your computer is a straightforward process. Most VPN providers offer dedicated apps for Windows and macOS operating systems. Simply download the app, create an account, and connect to a server of your choice. Once you’re connected, all of your internet traffic will be encrypted and routed through the VPN server.
Smartphones and Tablets
VPNs are also widely available for mobile devices. Whether you use an Android or iOS device, you can easily find a VPN app in your respective app store. The process of setting up a VPN on your smartphone or tablet is very similar to using it on a computer. Simply download the app, create an account, and connect to a server. Your mobile device will then be protected by the VPN.
Smart TVs
While not as common, you can even use a VPN on your smart TV. Some VPN providers offer dedicated apps for smart TVs, while others allow you to configure a VPN on your router, which will then protect all devices connected to your network, including your TV. This is especially useful for accessing streaming services that are not available in your region.
Routers
Configuring a VPN on your router is a slightly more advanced process, but it offers the most comprehensive protection. When you set up a VPN on your router, all devices connected to your network will automatically be protected by the VPN. This is a great option if you want to secure all of your devices without having to manually configure a VPN on each one.
Benefits of Using a VPN on Multiple Devices
Using a VPN on multiple devices offers several benefits:
- Enhanced Privacy: A VPN can help you stay anonymous online by masking your IP address and encrypting your traffic.
- Increased Security: A VPN can protect you from cyberattacks and data breaches by encrypting your data and routing it through a secure tunnel.
- Access to Geo-Restricted Content: A VPN allows you to bypass geographical restrictions and access content that is not available in your region.
- Improved Security on Public Wi-Fi: When using public Wi-Fi, a VPN can protect your data from hackers and snoopers.
Choosing a VPN
When choosing a VPN, consider factors such as speed, security, privacy policies, and price. Look for a VPN that offers strong encryption, a no-logs policy, and a wide network of servers.
VPN for Public Wi-Fi Security

Public Wi-Fi networks, while convenient, can pose serious security risks. These networks are often unsecured and open to anyone, making it easy for hackers to intercept your data. This is where a VPN (Virtual Private Network) comes in.
A VPN encrypts your internet traffic and routes it through a secure server, effectively creating a private tunnel between your device and the internet. This makes it much harder for hackers to snoop on your activity, even when connected to a public Wi-Fi network.
Why Use a VPN for Public Wi-Fi?
Here are some compelling reasons why using a VPN on public Wi-Fi is essential:
- Data Encryption: A VPN encrypts all your online activity, protecting your sensitive data like passwords, banking information, and personal communications.
- Privacy Protection: It masks your IP address, making it difficult for websites and advertisers to track your online behavior.
- Bypass Geo-Restrictions: VPNs allow you to access websites and content that may be blocked in your location.
- Increased Security: A VPN adds an extra layer of security by protecting your connection from hackers and malware.
How to Choose the Right VPN
When selecting a VPN, consider these factors:
- Strong Encryption: Look for VPNs that use industry-standard encryption protocols like AES-256.
- No Logging Policy: Choose a VPN that doesn’t store your browsing history or personal data.
- Speed and Performance: Opt for a VPN with a fast and reliable network.
- Customer Support: Look for a VPN provider with responsive and helpful customer support.
- Device Compatibility: Ensure the VPN is compatible with your devices (computers, smartphones, tablets).
Conclusion
Using a VPN on public Wi-Fi is an essential step in protecting your online security and privacy. By encrypting your data and masking your IP address, a VPN provides a safe and secure connection, ensuring your personal information remains private.
Bypassing Censorship with a VPN
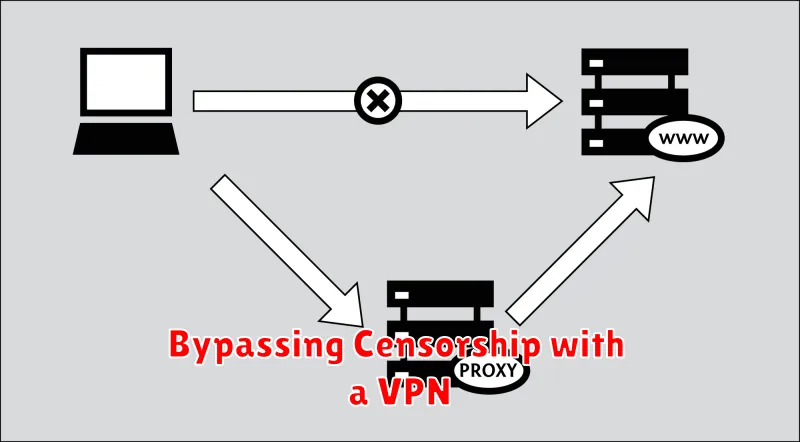
In today’s digital age, internet access has become an essential part of our lives. However, in many parts of the world, internet freedom is restricted by governments and organizations that impose censorship. This can limit access to information, social media platforms, and even basic communication tools.
Fortunately, there is a solution to this problem: Virtual Private Networks (VPNs). VPNs are powerful tools that can help you bypass censorship and regain control over your online privacy and security.
How VPNs Work
VPNs work by creating a secure and encrypted connection between your device and a server located in another country. When you connect to a VPN, your internet traffic is routed through this server, effectively masking your real IP address and location. This makes it difficult for censors to track your online activity or block access to specific websites.
Benefits of Using a VPN for Bypassing Censorship
Using a VPN to bypass censorship offers numerous benefits:
- Access to Blocked Websites and Services: VPNs allow you to access websites and services that are blocked in your region, such as social media platforms, news sites, and streaming services.
- Enhanced Privacy and Security: By encrypting your internet traffic, VPNs protect your data from prying eyes, including government surveillance and hackers.
- Anonymity: VPNs mask your real IP address, making it difficult for websites and services to track your online activity.
- Bypass Geo-Restrictions: VPNs allow you to access content that is only available in specific countries, such as streaming services with region-locked libraries.
Choosing the Right VPN
When choosing a VPN for bypassing censorship, it’s essential to consider the following factors:
- Server Network: Opt for a VPN with a vast server network in multiple locations to ensure reliable access to blocked websites and services.
- Security Features: Look for VPNs that use strong encryption protocols, such as AES-256, and offer features like a kill switch and DNS leak protection.
- Privacy Policy: Choose a VPN provider with a transparent and strict no-logs policy, ensuring your data isn’t stored or shared.
- Customer Support: Select a VPN provider with responsive customer support to address any issues or queries.
Conclusion
VPNs are essential tools for bypassing censorship and reclaiming your online freedom. They provide a secure and private way to access information, communicate freely, and enjoy a truly open internet experience. When selecting a VPN, prioritize security, privacy, and a reliable server network to ensure a seamless and secure connection.
Staying Anonymous Online with a VPN

In today’s digital age, our online privacy is under constant threat. From government surveillance to corporate data harvesting, it’s more important than ever to protect our anonymity online. One of the most effective tools for achieving this is a VPN (Virtual Private Network).
A VPN essentially creates a secure, encrypted tunnel between your device and the internet. This means that all your online activity is hidden from prying eyes, including your internet service provider (ISP), hackers, and even the government. By routing your traffic through a remote server, a VPN masks your real IP address, making it difficult to track your location or identify your identity.
Here are some of the key benefits of using a VPN:
- Enhanced privacy and security: VPNs encrypt your data, making it unreadable to anyone except you. This is especially important when using public Wi-Fi networks, which are notoriously vulnerable to hacking.
- Bypass censorship and geo-restrictions: Many countries censor internet content, and some websites and services are only available in specific regions. A VPN can help you bypass these restrictions by connecting you to a server in a different location.
- Unblock streaming services: Many streaming services, such as Netflix, Hulu, and BBC iPlayer, have different content libraries depending on your location. A VPN can help you access content that is not available in your region.
- Protect your online shopping and banking: When making online purchases or accessing your bank accounts, it’s crucial to protect your sensitive data from hackers. A VPN can help to secure your connection and prevent your information from being intercepted.
While VPNs offer many benefits, it’s important to choose a reputable provider. Not all VPNs are created equal, and some may compromise your privacy or security. Look for a provider with a strong no-logs policy, a reliable network, and robust encryption protocols.
Overall, a VPN is an essential tool for anyone who wants to stay anonymous and secure online. By encrypting your traffic and masking your IP address, a VPN can help you protect your privacy, bypass censorship, and access geo-restricted content. It’s a simple but powerful solution for safeguarding your online identity.

