In today’s digital landscape, navigating the complexities of cybersecurity is paramount. From the ever-evolving threat landscape to the rapid adoption of new technologies, organizations face a constant barrage of challenges in protecting their valuable assets. As we step into 2024, it’s crucial to understand the top cybersecurity trends shaping the year ahead. This knowledge empowers businesses and individuals to proactively fortify their defenses against emerging threats and build a robust security posture.
This article delves into the most impactful cybersecurity trends of 2024, providing insights into the evolving threats, technological advancements, and best practices for staying ahead of the curve. We will explore the rise of AI-powered security, the increasing prominence of cyberattacks targeting critical infrastructure, and the growing importance of zero-trust security. By understanding these trends, organizations can make informed decisions to mitigate risks, protect their data, and ensure business continuity in the face of evolving cyber threats.
The Evolving Threat Landscape: What to Expect in 2024

The cyber threat landscape is constantly evolving, with new threats emerging and attackers finding innovative ways to exploit vulnerabilities. As we enter 2024, it’s crucial to understand the emerging trends and prepare for potential threats. Here’s a glimpse into what we can expect:
Artificial Intelligence (AI) and Machine Learning (ML)
AI and ML are rapidly transforming cybersecurity. While these technologies can be used to enhance security measures, they can also be weaponized by attackers. Expect to see more sophisticated attacks powered by AI, including:
- AI-driven phishing attacks that can personalize emails and create convincing social engineering campaigns.
- AI-powered malware that can adapt to security defenses and evade detection.
- Automated botnets that can launch large-scale attacks with unprecedented speed and efficiency.
Ransomware and Data Extortion
Ransomware remains a significant threat, with attackers increasingly targeting critical infrastructure and demanding higher ransoms. Expect to see:
- More sophisticated ransomware strains that can encrypt data more effectively and evade security solutions.
- Double extortion attacks where attackers threaten to leak stolen data if the ransom is not paid.
- Targeted attacks on specific industries or organizations, leveraging industry-specific vulnerabilities.
Supply Chain Attacks
Supply chain attacks are becoming increasingly common, with attackers targeting vulnerable software and hardware vendors. Expect to see:
- Attacks on cloud service providers, compromising sensitive data and applications.
- Exploitation of third-party vendors, gaining access to internal systems through compromised software or services.
- Increased use of malicious code embedded in software updates or patches.
Cybercrime as a Service (CaaS)
CaaS is a growing trend, enabling attackers to purchase ready-made tools and services for launching attacks. Expect to see:
- More accessible attack tools, allowing individuals with limited technical expertise to launch sophisticated attacks.
- Increased availability of ransomware-as-a-service, making it easier for attackers to launch ransomware attacks.
- Emerging markets for stolen data, facilitating data breaches and extortion schemes.
The Rise of the Metaverse
The metaverse presents new opportunities and challenges for cybersecurity. Expect to see:
- New attack vectors in the metaverse, such as phishing attacks targeting virtual assets or identity theft.
- Attacks on virtual environments, disrupting services or stealing valuable data.
- Emerging threats related to privacy and data security in the metaverse.
Conclusion
The threat landscape in 2024 will be characterized by increasing sophistication, automation, and a focus on critical infrastructure and data extortion. By understanding these emerging trends and taking proactive steps to mitigate risks, organizations can strengthen their cybersecurity posture and protect their data and systems.
AI-Powered Attacks: The Rise of Sophisticated Cyber Threats

The landscape of cyber threats is constantly evolving, with attackers continuously seeking new ways to exploit vulnerabilities. In recent years, the advent of artificial intelligence (AI) has introduced a new dimension to this arms race, empowering attackers with unprecedented capabilities.
AI-powered attacks leverage the power of machine learning and deep learning algorithms to automate and enhance various aspects of cybercrime. This includes tasks such as:
- Target identification: AI can analyze vast amounts of data to identify potential victims and their weaknesses.
- Phishing campaign creation: AI can generate highly personalized and convincing phishing emails that are more likely to deceive unsuspecting users.
- Malware development: AI can assist in creating sophisticated malware that can evade detection and exploit new vulnerabilities.
- Attack execution: AI can automate attack execution, making it more efficient and scalable.
The implications of AI-powered attacks are significant. Attackers can now launch highly targeted and sophisticated attacks that are more difficult to detect and prevent. This poses a serious threat to individuals, businesses, and governments alike.
Examples of AI-Powered Attacks
Several real-world examples illustrate the growing threat of AI-powered attacks:
- Deepfakes: AI can be used to create realistic fake videos of individuals, which can be used for disinformation or to damage reputations.
- AI-powered malware: Researchers have developed AI-based malware that can evade traditional antivirus solutions.
- Automated phishing campaigns: AI can be used to create and launch large-scale phishing attacks that are highly personalized and difficult to distinguish from legitimate communications.
Protecting Against AI-Powered Attacks
While AI poses significant challenges, it also provides opportunities to defend against these threats. Organizations and individuals can take several steps to enhance their cybersecurity posture:
- Implement robust security measures: This includes using strong passwords, enabling multi-factor authentication, and keeping software up-to-date.
- Invest in AI-powered security solutions: These solutions can help detect and prevent AI-powered attacks.
- Educate users: Employees should be trained to identify and report suspicious activities.
- Foster collaboration: Sharing threat intelligence and best practices with other organizations is crucial in combating AI-powered attacks.
The battle against AI-powered attacks is ongoing. As AI technology continues to evolve, so too will the tactics employed by attackers. By staying vigilant, embracing new technologies, and collaborating with others, we can mitigate the risks and ensure a safer digital environment.
The Human Element: Social Engineering Tactics and How to Mitigate Risk

In the digital age, where technology reigns supreme, it’s easy to overlook the human element in cybersecurity. But the reality is, humans are often the weakest link in the chain, making them prime targets for social engineering attacks. This tactic exploits human psychology and trust to gain unauthorized access to sensitive information or systems. Understanding the various tactics employed by social engineers and implementing effective mitigation strategies is crucial for organizations of all sizes.
Social engineers often employ a variety of techniques to manipulate their targets. These tactics can range from seemingly harmless requests to elaborate phishing schemes. Let’s delve into some common social engineering tactics:
Common Social Engineering Tactics
Phishing: This involves sending deceptive emails, texts, or messages disguised as legitimate communications from trusted sources, aiming to trick recipients into revealing confidential information or clicking malicious links.
Pretexting: Social engineers create a fabricated scenario or false identity to gain the trust of their target, leading them to divulge sensitive information or grant access to systems.
Baiting: This tactic involves offering enticing rewards or opportunities, such as free software or access to exclusive content, to lure victims into downloading malicious files or clicking malicious links.
Quid Pro Quo: Social engineers leverage the principle of reciprocity, offering something in exchange for sensitive information or access to resources.
Scare Tactics: Using fear or urgency to manipulate individuals into taking immediate action, such as revealing personal information or granting access to systems.
Mitigating Social Engineering Risks
While social engineers are adept at exploiting human vulnerabilities, organizations can take proactive measures to mitigate these risks:
Employee Training and Awareness: Educating employees about social engineering tactics and best practices for identifying and avoiding these attacks is crucial. Regular training sessions, simulations, and phishing campaigns can enhance awareness and sharpen detection skills.
Strong Security Policies: Implementing strict policies around password management, data access, and user behavior can minimize vulnerabilities and prevent unauthorized access.
Multi-Factor Authentication: Employing multi-factor authentication (MFA) adds an extra layer of security, requiring users to provide multiple forms of identification before granting access.
Data Encryption: Encrypting sensitive data, whether at rest or in transit, ensures that even if information falls into the wrong hands, it remains inaccessible.
Security Software and Tools: Utilizing antivirus software, firewalls, and intrusion detection systems (IDS) can help detect and prevent malicious activities.
Conclusion
Social engineering attacks pose significant threats to individuals and organizations alike. By understanding common tactics and implementing effective mitigation strategies, organizations can fortify their defenses and protect themselves from these sophisticated attacks. Continuous vigilance, employee training, and robust security measures are essential for creating a secure digital environment.
Beyond the Password: Exploring Multi-Factor Authentication and Zero Trust Security
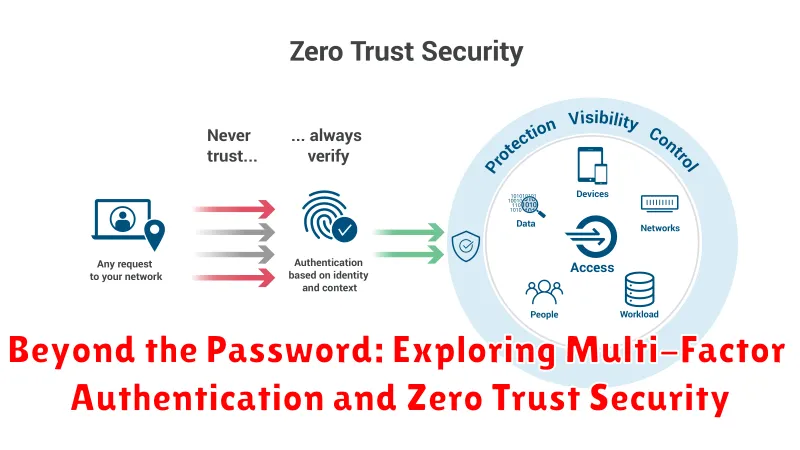
In today’s digital landscape, where cyber threats are constantly evolving, securing sensitive data is paramount. Traditional password-based authentication methods, while familiar, are no longer sufficient to safeguard against sophisticated attacks. This is where multi-factor authentication (MFA) and zero trust security come into play, offering a robust defense against unauthorized access and data breaches.
Multi-Factor Authentication: A Layer of Protection
MFA adds an extra layer of security by requiring users to provide multiple forms of authentication beyond just a password. These factors can include:
- Something you know: Password, PIN, security question
- Something you have: Phone, security token, smart card
- Something you are: Biometrics like fingerprint or facial recognition
By combining these factors, MFA significantly reduces the risk of unauthorized access, as it becomes much harder for attackers to compromise multiple authentication factors simultaneously.
Zero Trust Security: Trust No One
Zero trust security takes a different approach, assuming that no user or device can be trusted by default, regardless of its location or network access. Instead of relying on perimeter security, zero trust focuses on verifying every access request and enforcing least privilege principles.
Key principles of zero trust include:
- Continuous authentication: Verifying identity and access privileges regularly
- Micro-segmentation: Isolating network resources and limiting access to only authorized users and devices
- Data encryption: Protecting sensitive information even if it falls into the wrong hands
Benefits of Multi-Factor Authentication and Zero Trust Security
Implementing MFA and zero trust security measures offers numerous benefits:
- Enhanced security: Reduced risk of unauthorized access and data breaches
- Improved compliance: Meeting regulatory requirements for data protection
- Increased user confidence: Providing users with peace of mind knowing their data is secure
- Reduced operational costs: Preventing costly security incidents and data breaches
Conclusion: A Secure Future
In the ever-evolving world of cybersecurity, multi-factor authentication and zero trust security are essential tools for safeguarding sensitive data and protecting against malicious attacks. By adopting these robust security measures, organizations can build a more secure future, minimizing risks and ensuring the confidentiality and integrity of their critical assets.
Cybersecurity Mesh: A Flexible Approach to Protecting Distributed Networks
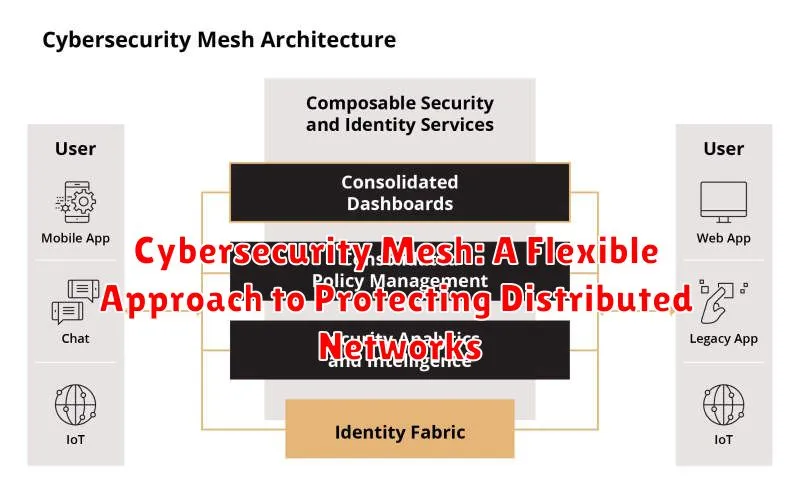
As businesses increasingly adopt cloud-native architectures and embrace remote work, the traditional perimeter-based security model has become insufficient. The distributed nature of modern networks requires a more flexible and adaptable approach to cybersecurity. Enter cybersecurity mesh, a revolutionary concept that aims to secure data and applications across the entire enterprise, regardless of location or device.
The cybersecurity mesh approach emphasizes a decentralized, distributed, and interconnected network of security controls. Instead of relying on a centralized security infrastructure, the mesh leverages a collection of smaller, interconnected security components that work together to protect the enterprise. These components can be deployed across various locations, including on-premises, cloud, and edge devices, providing a comprehensive and adaptable security posture.
Key Principles of Cybersecurity Mesh:
- Decentralization: Security controls are distributed across the network, eliminating reliance on a single point of failure. This allows for greater agility and resilience in the face of attacks.
- Interconnectivity: The mesh components communicate and share information with each other, enabling real-time threat detection and response. This collaboration fosters a more comprehensive understanding of threats and enables coordinated defenses.
- Automation and Orchestration: Automation plays a crucial role in the cybersecurity mesh, streamlining security tasks and reducing manual intervention. Orchestration tools enable the seamless integration of various security components, creating a cohesive security system.
- Zero Trust: The cybersecurity mesh embraces the zero-trust principle, assuming that no user or device can be trusted by default. This principle requires rigorous authentication and authorization for every access request, enhancing security throughout the network.
Benefits of Cybersecurity Mesh:
The cybersecurity mesh offers numerous advantages for businesses operating in a distributed environment:
- Improved Security Posture: By leveraging a distributed network of security controls, the mesh provides comprehensive protection across the entire enterprise, regardless of location.
- Enhanced Agility and Scalability: The decentralized architecture allows for easy scaling and adaptation to evolving security threats and business requirements.
- Reduced Risk and Costs: The mesh approach helps organizations mitigate risk by distributing security responsibilities and automating key tasks, reducing the need for costly security personnel.
- Improved User Experience: The mesh can deliver seamless access to resources while maintaining high levels of security, enhancing user productivity and satisfaction.
Implementing Cybersecurity Mesh:
Implementing a cybersecurity mesh requires a strategic approach that considers the specific needs of the organization. It involves:
- Defining Security Policies: Establish clear security policies that guide the implementation and operation of the mesh.
- Selecting Appropriate Security Technologies: Choose security tools that support the mesh principles and integrate seamlessly with existing infrastructure.
- Building a Strong Security Team: Recruit skilled security professionals who can design, deploy, and manage the mesh effectively.
- Continuous Monitoring and Improvement: Regularly monitor the mesh performance and make adjustments to ensure optimal security and efficiency.
In conclusion, cybersecurity mesh is a transformative approach to protecting distributed networks. By embracing decentralization, interconnectivity, automation, and zero trust, organizations can achieve a more robust and adaptable security posture that keeps pace with the evolving threat landscape. As businesses continue to embrace digital transformation and distributed architectures, the cybersecurity mesh will become increasingly critical for safeguarding data and applications across the entire enterprise.
Data Privacy in the Spotlight: Navigating Compliance and Building Trust

In today’s digital landscape, where data reigns supreme, the issue of data privacy has taken center stage. As organizations increasingly collect and leverage personal information, the need to safeguard this sensitive data and comply with evolving regulations has become paramount. This article delves into the critical aspects of data privacy, exploring the challenges and opportunities it presents for businesses and individuals alike.
The rise of data privacy laws like the General Data Protection Regulation (GDPR) in the European Union and the California Consumer Privacy Act (CCPA) in the United States has significantly impacted how organizations handle personal data. These regulations emphasize transparency, individual control, and accountability, empowering individuals with the right to access, correct, and delete their data. Failure to comply with these stringent rules can result in hefty fines and reputational damage.
Navigating the complex web of data privacy regulations requires a proactive approach. Organizations must adopt a comprehensive data privacy strategy that encompasses the following key elements:
- Data Inventory and Mapping: Identifying and classifying all personal data collected, stored, and processed by the organization.
- Privacy Impact Assessments (PIAs): Conducting thorough assessments to evaluate the privacy risks associated with data processing activities.
- Data Minimization: Limiting the collection and storage of personal data to what is strictly necessary.
- Security Measures: Implementing robust technical and organizational safeguards to protect data from unauthorized access, disclosure, alteration, or destruction.
- Transparency and Consent: Clearly informing individuals about how their data is being used and obtaining their explicit consent.
- Data Subject Rights: Establishing procedures to respond to individuals’ requests for access, correction, deletion, or restriction of their personal data.
- Data Breach Response: Developing a plan to promptly detect, investigate, and report data breaches in accordance with legal requirements.
Compliance with data privacy regulations is not merely a legal obligation; it’s a fundamental aspect of building trust with customers, partners, and employees. When organizations demonstrate their commitment to protecting personal data, they foster a sense of security and reliability, enhancing their reputation and fostering stronger relationships. A robust data privacy program can serve as a competitive advantage, differentiating businesses that prioritize transparency and ethical data practices.
In the era of data abundance, organizations have a responsibility to balance innovation with the fundamental right to privacy. By embracing data privacy principles and implementing best practices, businesses can navigate this challenging landscape, build trust, and unlock the full potential of data in a responsible and ethical manner.
The Skills Gap Challenge: Building a Future-Ready Cybersecurity Workforce
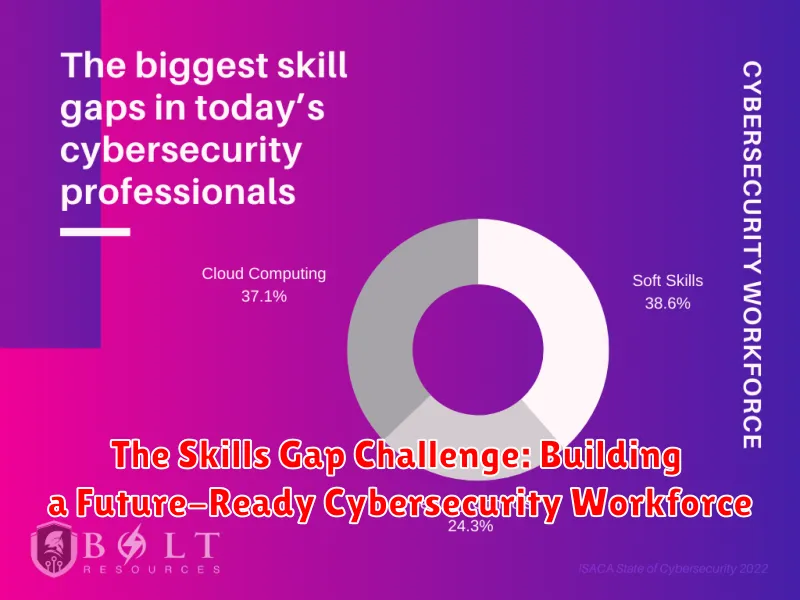
In today’s rapidly evolving digital landscape, cybersecurity has become a paramount concern for individuals and organizations alike. The increasing sophistication of cyberattacks, coupled with the ever-growing interconnectedness of our world, has led to a surge in demand for skilled cybersecurity professionals. However, a significant skills gap persists, posing a substantial challenge to the industry’s ability to effectively protect against emerging threats.
The cybersecurity skills gap is a complex issue with multiple contributing factors. One primary driver is the rapid pace of innovation in the cyber domain. New technologies, such as artificial intelligence (AI), cloud computing, and the Internet of Things (IoT), are constantly introducing new attack vectors and vulnerabilities. This rapid evolution requires cybersecurity professionals to continuously update their knowledge and skills to stay ahead of the curve.
Another contributing factor is the shortage of qualified individuals entering the cybersecurity workforce. While the demand for cybersecurity professionals is growing rapidly, the supply of qualified candidates is lagging behind. This shortage is partly due to a lack of awareness and interest in cybersecurity careers among students and young professionals. Additionally, traditional cybersecurity education programs often struggle to keep pace with the dynamic nature of the field.
The consequences of the cybersecurity skills gap are far-reaching and potentially devastating. Organizations that fail to adequately address their cybersecurity needs face a significantly higher risk of cyberattacks, which can lead to financial losses, reputational damage, and legal liabilities. Furthermore, a lack of qualified cybersecurity professionals can hinder the development and deployment of critical technologies and infrastructure, potentially impeding economic growth and national security.
To bridge the cybersecurity skills gap, a multifaceted approach is required. Governments, educational institutions, industry organizations, and individuals must all play a role in fostering a future-ready cybersecurity workforce. Some key initiatives include:
- Investing in cybersecurity education and training programs that align with industry needs and provide students with practical skills.
- Promoting cybersecurity careers to young people and encouraging them to pursue education and training in this field.
- Creating pathways for career advancement in cybersecurity, such as certification programs and mentorship opportunities.
- Enhancing cybersecurity research and development to drive innovation and create new solutions to emerging threats.
- Establishing public-private partnerships to address shared cybersecurity challenges and promote collaboration across sectors.
Building a future-ready cybersecurity workforce is essential for protecting our digital world from evolving threats. By taking a proactive and collaborative approach, we can address the skills gap and equip individuals and organizations with the knowledge and resources they need to navigate the complexities of the digital landscape.
Staying Ahead of the Curve: Best Practices for Cybersecurity in 2024

As the digital landscape continues to evolve at a breakneck pace, so too do the threats to our online security. In 2024, organizations and individuals alike face a complex tapestry of cyber risks that require proactive and comprehensive strategies to mitigate. This article explores the top cybersecurity best practices that will be crucial for staying ahead of the curve in the coming year.
1. Embrace a Zero Trust Security Framework
The days of assuming internal networks are safe are over. A Zero Trust approach mandates that all access to resources, whether internal or external, must be verified and authorized explicitly. This means implementing multi-factor authentication (MFA), least privilege access controls, and robust security monitoring for all systems and users.
2. Prioritize Patching and Vulnerability Management
Cybercriminals are constantly exploiting vulnerabilities in software and hardware. Organizations must make patching a top priority, ensuring that all systems are updated regularly with the latest security fixes. A comprehensive vulnerability management program is essential to proactively identify and address weaknesses in the security posture.
3. Implement Strong Password Policies and Multi-Factor Authentication (MFA)
Weak passwords remain a primary attack vector. Organizations and individuals must enforce strong password policies, encouraging the use of complex passwords that are difficult to guess. Multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code from a mobile device, before granting access.
4. Invest in Advanced Threat Detection and Response (TDR) Solutions
Traditional security solutions are often insufficient to combat sophisticated cyberattacks. Advanced threat detection and response (TDR) systems utilize machine learning and artificial intelligence (AI) to analyze large volumes of data, identify suspicious activities, and respond automatically to threats. These solutions can help organizations to detect and contain attacks before they cause significant damage.
5. Train Employees on Cybersecurity Awareness
Human error remains a significant vulnerability in any security strategy. Regular cybersecurity awareness training for employees is critical to educate them on best practices for identifying and preventing phishing scams, social engineering attacks, and other common threats. Training programs should cover topics such as password security, data protection, and how to recognize suspicious emails and websites.
6. Data Backup and Disaster Recovery
Even with the best security practices in place, there is always a risk of a data breach. Organizations must have a comprehensive data backup and disaster recovery plan to protect their critical data. Regularly back up all important data to a secure offsite location, and test the recovery process periodically to ensure its effectiveness.
7. Embrace Emerging Technologies
The cybersecurity landscape is constantly evolving, and organizations need to stay ahead of the curve by embracing emerging technologies. Blockchain, artificial intelligence (AI), and machine learning (ML) offer exciting opportunities to enhance security and automate threat detection and response.
Conclusion
Cybersecurity is an ongoing journey, not a destination. By adopting these best practices and staying informed about emerging threats, organizations and individuals can build a more robust and resilient security posture. Remember, the key to staying ahead of the curve is to be proactive, adaptable, and committed to continuous improvement.

