In today’s unpredictable world, businesses are facing constant disruptions, from natural disasters and cyberattacks to economic downturns and global pandemics. Business continuity has become paramount, ensuring operations can continue despite unforeseen challenges. While many focus on the immediate impacts of these disruptions, the unsung heroes behind seamless recovery are often overlooked: the IT department.
Beyond the surface of everyday tasks, IT plays a critical role in maintaining business continuity. IT professionals are the architects of resilient systems, implementing robust infrastructure, data backup strategies, and disaster recovery plans. They are the first responders, working tirelessly to restore critical systems and ensure minimal downtime, allowing businesses to weather the storm and emerge stronger.
Beyond the Break-Fix: Redefining the Role of IT in Business Continuity

In today’s rapidly evolving business landscape, IT has transcended its traditional role as a reactive “break-fix” department. It has become an integral strategic partner, driving innovation, agility, and resilience. As businesses strive for continuous operations and seamless customer experiences, the role of IT in business continuity has taken on paramount importance.
Gone are the days when IT merely addressed technology outages and system failures. Now, IT is expected to proactively anticipate disruptions, mitigate risks, and ensure business operations remain uninterrupted. This shift demands a holistic approach to business continuity planning, encompassing various aspects of IT infrastructure, data security, disaster recovery, and operational processes.
From Reactive to Proactive: Embracing a Shift in Mindset
The cornerstone of redefining IT’s role in business continuity lies in a fundamental shift from a reactive to a proactive mindset. Instead of simply reacting to disruptions, IT teams must actively identify vulnerabilities, implement preventive measures, and continuously refine their business continuity strategies.
This proactive approach involves:
- Regular risk assessments to identify potential threats and vulnerabilities
- Developing comprehensive disaster recovery plans for critical systems and data
- Implementing robust security measures to protect against cyberattacks and data breaches
- Testing and validating business continuity plans on a regular basis
- Building a resilient IT infrastructure that can withstand disruptions
Beyond Technology: Fostering Collaboration and Communication
Business continuity is not solely an IT responsibility. It requires cross-functional collaboration and seamless communication across the entire organization. IT teams must work closely with business leaders, department heads, and employees to ensure alignment, understanding, and effective implementation of business continuity strategies.
Key areas of collaboration include:
- Defining critical business processes and their recovery time objectives (RTOs)
- Identifying key stakeholders and their roles in the event of a disruption
- Establishing clear communication channels for crisis management
- Conducting regular training and drills to prepare employees for emergency situations
Embracing Technology to Enhance Resilience
Technology plays a crucial role in supporting business continuity. Modern IT solutions offer a wide range of capabilities for enhancing resilience, such as:
- Cloud computing for disaster recovery and data backup
- Artificial intelligence (AI) for predictive maintenance and threat detection
- Automation for streamlining disaster recovery processes
- Cybersecurity tools for protecting against data breaches and malware attacks
The Future of IT in Business Continuity
As technology continues to evolve, the role of IT in business continuity will become even more multifaceted. The focus will shift towards leveraging emerging technologies to create even more resilient and adaptable businesses. This includes:
- Edge computing for distributing workloads and reducing reliance on centralized data centers
- Blockchain for ensuring data integrity and immutability
- Quantum computing for enhancing security and accelerating data processing
Conclusion
Redefining the role of IT in business continuity is not merely a technical endeavor; it’s a fundamental shift in mindset and approach. By embracing proactive measures, fostering collaboration, and leveraging emerging technologies, IT can become a strategic partner in ensuring business continuity and driving organizational success in today’s volatile and unpredictable business environment.
Disaster Recovery Planning: Ensuring Business Resilience in the Face of Disruption

In today’s interconnected world, businesses are constantly vulnerable to a wide range of disruptions, from natural disasters and cyberattacks to technical failures and pandemics. The impact of these events can be devastating, leading to financial losses, operational downtime, and reputational damage. To mitigate these risks and ensure business continuity, a robust disaster recovery plan is essential.
Why is Disaster Recovery Planning Crucial?
A disaster recovery plan provides a structured framework for responding to and recovering from disruptive events. It outlines the steps necessary to protect critical assets, minimize downtime, and restore operations to a pre-disruption state. The benefits of a well-defined plan include:
- Minimized Business Disruption: A plan helps to quickly restore essential operations, reducing downtime and financial losses.
- Data Protection and Recovery: Critical data and systems are protected and can be readily restored, preventing data loss and disruption.
- Enhanced Business Continuity: The plan ensures that the organization can continue operating, even in the face of significant challenges.
- Improved Risk Management: By identifying and assessing potential risks, organizations can take proactive measures to mitigate them.
- Increased Stakeholder Confidence: A well-prepared business demonstrates its resilience and commitment to protecting its assets, building trust with stakeholders.
Key Components of a Disaster Recovery Plan
A comprehensive disaster recovery plan should include the following essential components:
- Risk Assessment: Identify and assess potential risks, including their likelihood and impact.
- Business Impact Analysis: Determine the critical business functions and the consequences of their disruption.
- Recovery Time Objectives (RTOs): Define the maximum acceptable downtime for each critical function.
- Recovery Point Objectives (RPOs): Specify the acceptable amount of data loss that can be tolerated.
- Recovery Strategies: Outline the methods for restoring critical systems and data, such as backups, data replication, and cloud services.
- Communication Plan: Establish procedures for communicating with stakeholders, employees, and customers during and after a disaster.
- Testing and Maintenance: Regularly test the plan and update it as needed to ensure its effectiveness.
Implementing a Successful Disaster Recovery Plan
Implementing a successful disaster recovery plan requires a structured approach:
- Obtain Executive Buy-in: Secure support from top management to ensure the plan is prioritized and funded.
- Engage Key Stakeholders: Involve relevant departments and individuals in the planning process.
- Define Clear Responsibilities: Assign roles and responsibilities to ensure clear accountability.
- Develop Detailed Procedures: Create step-by-step instructions for responding to and recovering from various disaster scenarios.
- Regularly Test and Exercise: Conduct periodic drills to validate the plan and identify areas for improvement.
- Continuously Improve: Review the plan regularly, incorporate lessons learned from real or simulated events, and adapt it to changing business needs.
Conclusion
In today’s volatile environment, disaster recovery planning is no longer optional; it is a necessity for business survival. By implementing a comprehensive and well-tested plan, organizations can protect their critical assets, minimize downtime, and ensure business continuity in the face of unexpected disruptions. Proactive disaster recovery planning is the key to building resilience and safeguarding the future of your organization.
The Cloud as a Continuity Enabler: Leveraging Scalability and Flexibility

In today’s dynamic business landscape, ensuring business continuity is paramount. Disruptions, whether caused by natural disasters, cyberattacks, or internal errors, can severely impact operations, revenue, and reputation. The cloud, with its inherent scalability and flexibility, has emerged as a powerful tool to enhance business continuity strategies.
Scalability and Elasticity for Enhanced Resilience
The cloud’s ability to scale resources on demand is a game-changer for business continuity. Businesses can quickly provision additional computing power, storage, and network bandwidth during peak demand or unexpected surges. This elasticity allows organizations to handle spikes in traffic, prevent system overload, and maintain critical operations even during challenging events.
Redundancy and Disaster Recovery Simplified
Cloud providers offer multiple data centers and redundancy built into their infrastructure. This eliminates the need for businesses to invest in expensive and complex on-premises disaster recovery solutions. By replicating data and applications across geographically dispersed locations, cloud providers ensure minimal downtime and swift recovery from catastrophic events.
Simplified Backup and Recovery
Cloud-based backup and recovery solutions streamline the process of protecting valuable data. Regular backups are automated, and data can be restored quickly and easily. This simplifies the recovery process and minimizes data loss, ensuring business continuity in the face of hardware failures, accidental deletions, or malware attacks.
Cost-Effectiveness and Agility
Cloud-based business continuity solutions are often more cost-effective than traditional on-premises solutions. Businesses can pay only for the resources they use, avoiding upfront investments in hardware and infrastructure. Moreover, the cloud’s agility allows organizations to adapt quickly to changing business needs and implement new continuity strategies efficiently.
Key Considerations for Cloud-Based Continuity
While the cloud offers significant advantages, organizations must consider several factors when implementing cloud-based business continuity strategies. These include:
- Security: Ensure robust security measures to protect sensitive data and applications in the cloud.
- Data Sovereignty: Understand data location and compliance regulations for international operations.
- Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO): Define acceptable downtime and data loss tolerance levels.
By thoughtfully considering these factors and working with reputable cloud providers, organizations can leverage the cloud’s power to build robust business continuity strategies and minimize the impact of disruptions. This ensures a resilient and adaptable business that can withstand challenges and thrive in today’s unpredictable environment.
Data Protection and Backup: Safeguarding Critical Information Assets

In today’s digital age, data is the lifeblood of businesses and individuals alike. From financial records to personal photographs, our information assets hold immense value and require robust protection measures. Data protection and backup strategies are essential for safeguarding this critical information, ensuring its availability, integrity, and confidentiality in the face of potential threats.
Data Protection encompasses a range of measures designed to prevent unauthorized access, use, disclosure, disruption, modification, or destruction of data. It involves implementing a multi-layered approach, including:
- Access control: Restricting access to sensitive data based on user roles and permissions.
- Encryption: Transforming data into an unreadable format, ensuring confidentiality even if compromised.
- Data loss prevention (DLP): Implementing policies and tools to prevent sensitive data from leaving the organization’s control.
- Network security: Protecting the network infrastructure from unauthorized access and cyberattacks.
- Employee training: Educating employees about data security best practices and potential risks.
Data backup, on the other hand, is the process of creating copies of data and storing them in a separate location. This serves as a safeguard against data loss due to hardware failures, natural disasters, or malicious attacks. Effective backup strategies include:
- Regular backups: Performing backups on a frequent basis to ensure that recent changes are captured.
- Multiple backup copies: Creating multiple copies of data and storing them in different locations for redundancy.
- Off-site storage: Storing backups in a separate physical location to protect against local disasters.
- Data recovery testing: Regularly testing the backup and recovery process to ensure its effectiveness.
The Importance of Data Protection and Backup
Data protection and backup are paramount for several reasons:
- Business continuity: Ensuring that critical operations can resume quickly after a data loss event.
- Compliance with regulations: Meeting industry-specific regulations and legal requirements regarding data security.
- Reputation management: Protecting sensitive information from breaches that could damage the organization’s reputation.
- Financial stability: Minimizing financial losses associated with data loss, such as downtime, recovery costs, and legal penalties.
- Customer trust: Maintaining customer confidence by demonstrating a commitment to data security.
Conclusion
Data protection and backup are integral components of a comprehensive cybersecurity strategy. By implementing robust measures, organizations and individuals can safeguard their critical information assets, ensuring their availability, integrity, and confidentiality. Regular assessment, continuous improvement, and staying abreast of evolving threats are essential for maintaining a strong data security posture.
Cybersecurity as a Foundation: Protecting Business Operations from Cyber Threats
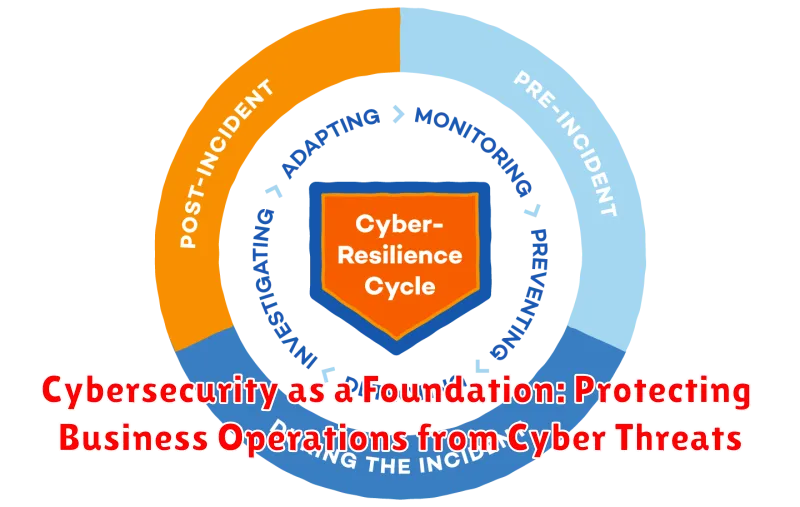
In today’s digitally driven world, where businesses rely heavily on technology for their operations, cybersecurity has become a paramount concern. Cyberattacks are growing in sophistication and frequency, posing a significant threat to businesses of all sizes. The consequences of a successful cyberattack can be devastating, leading to financial losses, reputational damage, and disruptions to critical operations. As such, establishing a robust cybersecurity foundation is no longer an option, but a necessity for every business.
A comprehensive cybersecurity strategy should encompass multiple layers of protection, including:
- Network security: Implementing firewalls, intrusion detection systems, and access control measures to prevent unauthorized access to the network.
- Endpoint security: Protecting individual devices, such as computers, laptops, and mobile phones, from malware and other threats.
- Data security: Implementing encryption, data loss prevention (DLP) solutions, and secure data storage practices to protect sensitive information.
- User education and awareness: Training employees to recognize and report suspicious activities, promoting safe browsing habits, and enforcing strong password policies.
- Incident response planning: Developing a clear plan for responding to cyberattacks, including steps for containment, remediation, and recovery.
Investing in cybersecurity is an investment in the future of your business. By taking proactive steps to protect your systems, data, and reputation, you can mitigate risks, enhance operational efficiency, and build a more resilient organization.
The Importance of Cybersecurity for Business Operations
The impact of cyberattacks can be far-reaching, affecting multiple aspects of a business’s operations. Here are some key areas where cybersecurity plays a critical role:
- Financial stability: Cyberattacks can lead to financial losses through theft of funds, data breaches, and ransomware demands.
- Customer trust: Data breaches can damage customer trust and lead to reputational damage, potentially impacting sales and brand loyalty.
- Operational efficiency: Disruptions to critical systems and data access can significantly hamper productivity and operational efficiency.
- Legal compliance: Businesses are subject to various data privacy regulations, such as GDPR and CCPA, and failure to comply can result in hefty fines and penalties.
By prioritizing cybersecurity, businesses can avoid these potential consequences and build a more resilient and sustainable operation.
Cybersecurity Best Practices
To ensure optimal cybersecurity, businesses should implement a comprehensive strategy that incorporates the following best practices:
- Regularly update software and systems: Software updates often include security patches that address vulnerabilities, making it critical to stay up-to-date.
- Use strong passwords and multi-factor authentication: Strong passwords and multi-factor authentication add an extra layer of security to protect accounts and data.
- Implement access control measures: Limiting access to sensitive information and systems based on user roles and permissions helps prevent unauthorized access.
- Back up data regularly: Regular data backups provide a safety net in case of data loss due to cyberattacks or other incidents.
- Conduct regular security audits and assessments: Periodic audits and assessments help identify vulnerabilities and weaknesses in your security posture.
- Stay informed about emerging threats: Staying up-to-date on the latest cybersecurity threats and trends allows businesses to proactively adapt their defenses.
By adhering to these best practices, businesses can significantly improve their security posture and mitigate the risks of cyberattacks.
Conclusion
In the digital age, cybersecurity is not a luxury, but a fundamental necessity for any business that wants to thrive. A robust cybersecurity foundation is essential for protecting business operations, safeguarding sensitive information, and maintaining customer trust. By prioritizing cybersecurity, businesses can build a more resilient organization, mitigate risks, and create a safer and more secure environment for all.
Collaboration and Communication: Key Ingredients for Effective Business Continuity

In the ever-changing landscape of today’s business world, unforeseen events can disrupt operations and threaten the very survival of companies. It is therefore essential for organizations to have a robust business continuity plan in place to mitigate the impact of such incidents and ensure a swift and seamless recovery. While technological solutions and infrastructure play a crucial role, the success of any business continuity strategy hinges on two fundamental pillars: collaboration and communication.
Collaboration: The Foundation for Resilience
When faced with a crisis, businesses need to act quickly and decisively. This requires a collaborative effort from all stakeholders, including employees, management, and external partners. Effective collaboration ensures that everyone is on the same page, working towards a common goal, and leveraging their unique skills and expertise to overcome challenges.
Here’s how collaboration fosters resilience:
- Shared understanding: Collaboration facilitates the exchange of information, ensuring that everyone involved understands the nature of the disruption, the impact on operations, and the immediate steps needed to address the situation.
- Cross-functional coordination: By breaking down silos between departments, collaboration allows teams to work together seamlessly, coordinating their efforts and leveraging each other’s strengths to overcome obstacles.
- Agile decision-making: Collaboration empowers teams to make informed decisions quickly, adapting to changing circumstances and implementing solutions efficiently.
Communication: The Lifeline for Success
Clear and consistent communication is vital for maintaining operational continuity. It acts as a lifeline, keeping everyone informed, coordinated, and aligned throughout the crisis. Effective communication channels ensure that information flows freely and accurately, minimizing confusion and panic.
Here’s how communication fuels business continuity:
- Information dissemination: Prompt and accurate communication keeps employees, customers, and stakeholders informed about the situation, the company’s response, and any necessary changes in procedures.
- Status updates: Regular updates provide reassurance and keep everyone informed about the progress of recovery efforts, fostering confidence and trust.
- Feedback and escalation: Open communication channels enable employees to report issues, seek assistance, and escalate concerns to ensure a timely and effective response.
Building a Collaborative and Communicative Culture
Developing a collaborative and communicative culture within an organization is a continuous process that requires sustained effort. It involves:
- Investing in communication tools: Implementing robust communication platforms, such as instant messaging, video conferencing, and collaborative workspaces, facilitates seamless information sharing and collaboration.
- Promoting open communication: Encouraging open dialogue, constructive feedback, and active listening fosters a culture of transparency and trust.
- Regular drills and exercises: Conducting regular business continuity drills and simulations allows employees to practice collaboration and communication procedures in a safe environment, improving their preparedness for real-world events.
Conclusion:
In the face of unexpected disruptions, collaboration and communication are not just nice-to-haves; they are essential for survival. By fostering a culture of teamwork, transparency, and effective communication, organizations can significantly enhance their resilience and ensure a smooth recovery from any unforeseen challenges.
Testing and Refining: Ensuring Your Business Continuity Plan is Up to the Task
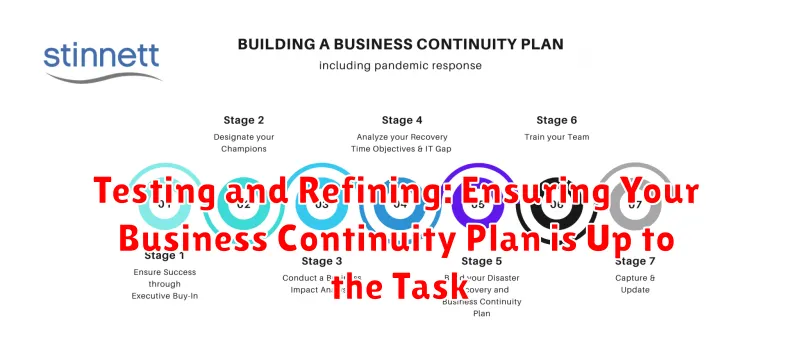
A robust business continuity plan (BCP) is crucial for any organization, providing a roadmap to navigate disruptions and keep operations running smoothly. But a plan is only as effective as its implementation. Regular testing and refining are essential to ensure your BCP is up to the task when disaster strikes.
Why Test Your BCP?
Testing your BCP offers several benefits:
- Identifies Gaps and Weaknesses: Testing reveals areas where your plan is inadequate, allowing you to address them proactively.
- Ensures Plan Feasibility: Real-world simulations confirm whether your plan is practical and achievable under pressure.
- Improves Communication and Coordination: Testing fosters collaboration among team members, enhancing communication and coordination during a crisis.
- Builds Confidence and Preparedness: Regular testing instills confidence in your plan and prepares your team to respond effectively.
Types of BCP Tests
There are various testing methods, each with its own advantages:
- Tabletop Exercises: A low-cost, low-impact method where teams discuss hypothetical scenarios and review their responses.
- Functional Tests: Involve activating specific aspects of your plan, like restoring data or activating alternate communication channels.
- Full-Scale Simulations: The most comprehensive test, where teams simulate a real-world emergency, including evacuation, communication, and operational recovery.
Refining Your BCP
Testing often reveals areas for improvement. Use the insights gained from testing to refine your BCP:
- Update Contact Information: Ensure all emergency contacts are up-to-date and easily accessible.
- Clarify Responsibilities: Clearly define roles and responsibilities for each team member involved in the recovery process.
- Review Recovery Strategies: Reassess your recovery strategies, considering any changes in technology or business processes.
- Improve Communication Channels: Ensure your communication channels are reliable and can handle high volumes of traffic.
Conclusion
Testing and refining your BCP are crucial steps in ensuring its effectiveness. By regularly evaluating and updating your plan, you can build confidence and be prepared to navigate any disruption, minimizing the impact on your business.
IT’s Strategic Role: Aligning Technology with Business Goals for Long-Term Success
In today’s rapidly evolving technological landscape, Information Technology (IT) has transcended its traditional role as a mere support function and emerged as a strategic driver of business growth and innovation. The ability of IT to align with business goals is paramount for organizations to achieve sustainable competitive advantage and long-term success. This article explores the multifaceted role of IT in shaping business strategy and how organizations can leverage technology to achieve their strategic objectives.
IT as a Catalyst for Business Transformation
IT has become a powerful catalyst for business transformation, enabling organizations to streamline processes, enhance customer experiences, and unlock new revenue streams. By leveraging emerging technologies such as cloud computing, artificial intelligence (AI), and big data analytics, organizations can:
- Automate repetitive tasks, freeing up human resources for more strategic activities.
- Improve operational efficiency by optimizing workflows and reducing bottlenecks.
- Gain valuable insights from data to make informed decisions and anticipate market trends.
- Personalize customer experiences based on their individual preferences and behavior.
- Develop innovative products and services that meet evolving customer demands.
Aligning IT Strategy with Business Goals
Effective IT strategy is not merely about acquiring the latest technologies. It’s about aligning technology investments with the organization’s overarching business goals. This requires a collaborative approach where IT leaders work closely with business stakeholders to understand their needs and translate them into actionable technology solutions.
Key steps in aligning IT strategy with business goals include:
- Defining clear business objectives: What are the organization’s strategic priorities and how can technology contribute to their achievement?
- Conducting a technology assessment: Analyzing existing IT infrastructure, identifying gaps, and evaluating emerging technologies that can address business needs.
- Developing a roadmap: Creating a comprehensive plan that outlines technology investments, implementation timelines, and anticipated outcomes.
- Prioritizing projects: Focusing on initiatives that deliver the greatest return on investment and align with strategic goals.
- Continuous monitoring and evaluation: Tracking progress, measuring impact, and making adjustments as needed to ensure alignment with evolving business needs.
Building a Data-Driven Culture
In today’s data-driven world, organizations need to embrace a culture that values data-driven decision making. IT plays a crucial role in fostering this culture by providing access to reliable data and enabling the use of analytics tools.
By leveraging big data analytics, organizations can gain insights into customer behavior, market trends, and operational efficiency. This data-driven intelligence empowers leaders to make more informed decisions, anticipate challenges, and seize opportunities.
The Importance of Agility and Innovation
To remain competitive in the digital age, organizations must embrace agility and innovation. IT can play a key role in fostering this culture by:
- Promoting a culture of experimentation and continuous improvement: Encourage employees to explore new technologies and share their ideas for process improvements.
- Adopting agile methodologies: Employing flexible and iterative development practices that allow for rapid prototyping and adaptation to changing requirements.
- Investing in talent development: Building a workforce with the skills and knowledge to leverage emerging technologies effectively.
Conclusion
In conclusion, IT has become an indispensable strategic asset for organizations seeking to achieve sustainable growth and success. By aligning technology investments with business goals, embracing a data-driven culture, and fostering agility and innovation, organizations can leverage IT to transform their operations, enhance customer experiences, and unlock new opportunities in the digital age.

